一、 漏洞 CVE-2024-7954 基础信息
漏洞信息
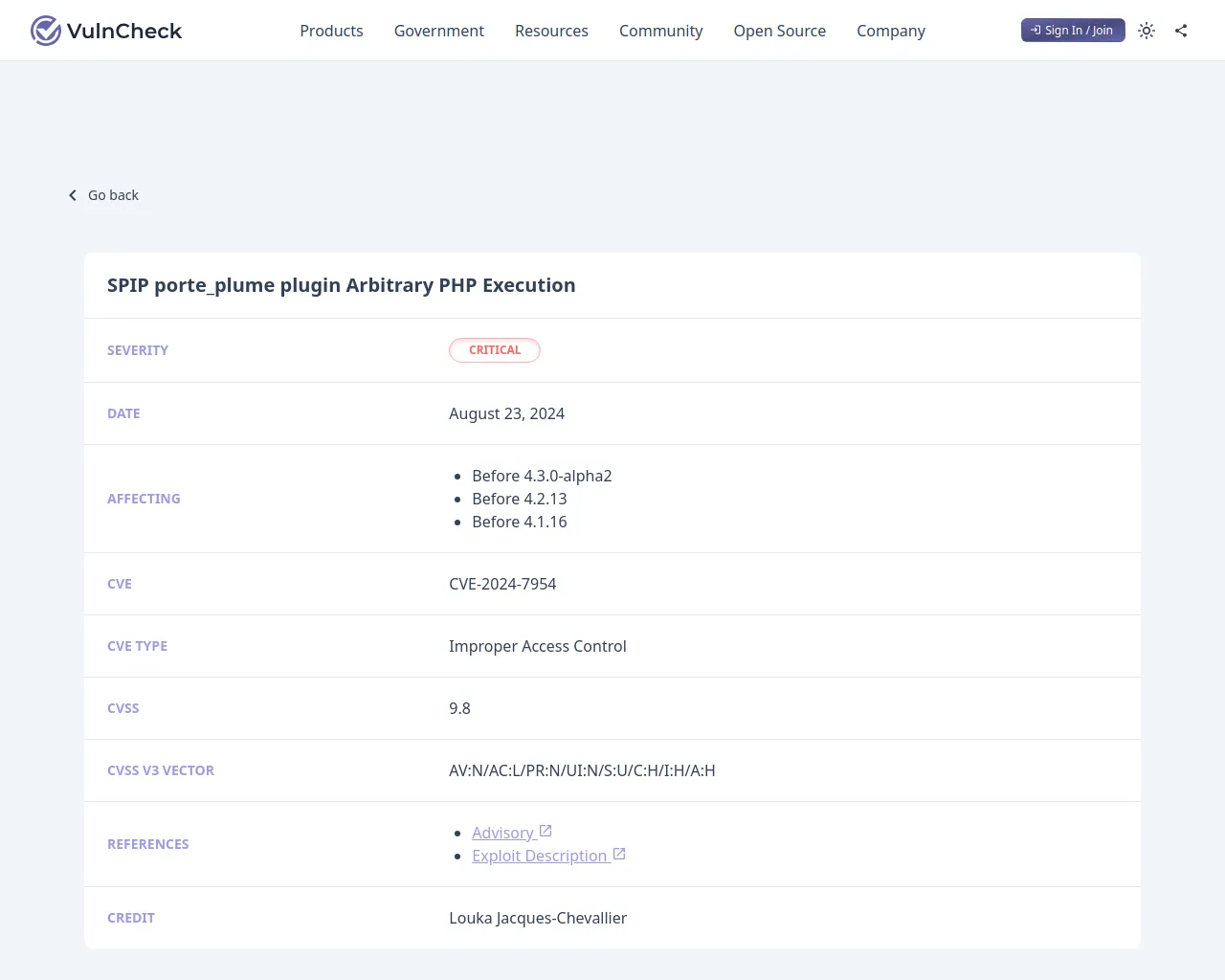
# SPIP porte_plume 插件任意 PHP 执行漏洞
## 概述
Porte_plume 插件在 SPIP 4.30-alpha2、4.2.13 和 4.1.16 版本之前存在任意代码执行漏洞。远程未认证攻击者可以通过发送恶意的 HTTP 请求,以 SPIP 用户的权限执行任意 PHP 代码。
## 影响版本
- SPIP 4.30-alpha2 之前版本
- SPIP 4.2.13 之前版本
- SPIP 4.1.16 之前版本
## 细节
攻击者可以通过发送精心构造的 HTTP 请求来利用此漏洞,使服务器执行任意 PHP 代码。
## 影响
该漏洞允许远程未认证的攻击者以 SPIP 用户的权限执行任意代码,可能导致完全控制受影响的系统。
提示
尽管我们采用了先进的大模型技术,但其输出仍可能包含不准确或过时的信息。
神龙会尽力确保数据准确,但也请结合实际情况进行甄别与判断。
神龙祝您一切顺利!
神龙会尽力确保数据准确,但也请结合实际情况进行甄别与判断。
神龙祝您一切顺利!
漏洞标题
SPIP porte_plume Plugin Arbitrary PHP Execution
来源:美国国家漏洞数据库 NVD
漏洞描述信息
The porte_plume plugin used by SPIP before 4.30-alpha2, 4.2.13, and 4.1.16 is vulnerable to an arbitrary code execution vulnerability. A remote and unauthenticated attacker can execute arbitrary PHP as the SPIP user by sending a crafted HTTP request.
来源:美国国家漏洞数据库 NVD
CVSS信息
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
来源:美国国家漏洞数据库 NVD
漏洞类别
访问控制不恰当
来源:美国国家漏洞数据库 NVD
漏洞标题
SPIP 安全漏洞
来源:中国国家信息安全漏洞库 CNNVD
漏洞描述信息
SPIP是SPIP开源的一个用于创建 Internet 站点的免费软件。 SPIP存在安全漏洞,该漏洞源于容易受到任意代码执行漏洞的影响,远程未经身份验证的攻击者可以通过发送精心设计的HTTP请求以SPIP用户身份执行任意PHP。
来源:中国国家信息安全漏洞库 CNNVD
CVSS信息
N/A
来源:中国国家信息安全漏洞库 CNNVD
漏洞类别
其他
来源:中国国家信息安全漏洞库 CNNVD
二、漏洞 CVE-2024-7954 的公开POC
| # | POC 描述 | 源链接 | 神龙链接 |
|---|---|---|---|
| 1 | Unauthenticated Remote Code Execution in SPIP versions up to and including 4.2.12 | https://github.com/Chocapikk/CVE-2024-7954 | POC详情 |
| 2 | This exploit will attempt to execute system commands on SPIP targets. | https://github.com/bigb0x/CVE-2024-7954 | POC详情 |
| 3 | Unauthenticated Remote Code Execution in SPIP versions up to and including 4.2.12 | https://github.com/fa-rrel/CVE-2024-7954-RCE | POC详情 |
| 4 | None | https://github.com/TheCyberguy-17/RCE_CVE-2024-7954 | POC详情 |
| 5 | None | https://github.com/MuhammadWaseem29/RCE-CVE-2024-7954 | POC详情 |
| 6 | The porte_plume plugin used by SPIP before 4.30-alpha2, 4.2.13, and 4.1.16 is vulnerable to an arbitrary code execution vulnerability. A remote and unauthenticated attacker can execute arbitrary PHP as the SPIP user by sending a crafted HTTP request. | https://github.com/issamiso/CVE-2024-7954 | POC详情 |
| 7 | Unauthenticated Remote Code Execution in SPIP versions up to and including 4.2.12 | https://github.com/gh-ost00/CVE-2024-7954-RCE | POC详情 |
| 8 | The porte_plume plugin used by SPIP before 4.30-alpha2, 4.2.13, and 4.1.16 is vulnerable to an arbitrary code execution vulnerability. A remote and unauthenticated attacker can execute arbitrary PHP as the SPIP user by sending a crafted HTTP request. | https://github.com/issamjr/CVE-2024-7954 | POC详情 |
| 9 | SPIP 4.30-alpha2、4.2.13、4.1.16之前的版本使用的porte_plume插件存在任意代码执行漏洞,远程未经身份验证的攻击者可以通过发送精心设计的HTTP 请求以SPIP用户身份执行任意PHP代码。 | https://github.com/zxj-hub/CVE-2024-7954POC | POC详情 |
| 10 | The porte_plume plugin used by SPIP before 4.30-alpha2, 4.2.13, and 4.1.16 is vulnerable to an arbitrary code execution vulnerability. A remote and unauthenticated attacker can execute arbitrary PHP as the SPIP user by sending a crafted HTTP request. (CRITICAL) | https://github.com/0dayan0n/RCE_CVE-2024-7954- | POC详情 |
| 11 | None | https://github.com/Arthikw3b/RCE-CVE-2024-7954 | POC详情 |
| 12 | The porte_plume plugin used by SPIP before 4.30-alpha2, 4.2.13, and 4.1.16 is vulnerable to an arbitrary code execution vulnerability. A remote and unauthenticated attacker can execute arbitrary PHP as the SPIP user by sending a crafted HTTP request. | https://github.com/projectdiscovery/nuclei-templates/blob/main/http/cves/2024/CVE-2024-7954.yaml | POC详情 |
| 13 | None | https://github.com/r0otk3r/CVE-2024-7954 | POC详情 |
| 14 | None | https://github.com/nak000/RCE-CVE-2024-7954 | POC详情 |
三、漏洞 CVE-2024-7954 的情报信息
-
标题: SPIP porte_plume plugin Arbitrary PHP Execution | Advisories | VulnCheck -- 🔗来源链接
标签: third-party-advisory
- https://blog.spip.net/Mise-a-jour-critique-de-securite-sortie-de-SPIP-4-3-0-alpha2-SPIP-4-2-13-SPIP-4.html vendor-advisory
- https://thinkloveshare.com/hacking/spip_preauth_rce_2024_part_1_the_feather/ technical-description exploit
- https://nvd.nist.gov/vuln/detail/CVE-2024-7954
四、漏洞 CVE-2024-7954 的评论
暂无评论