一、 漏洞 CVE-2024-9047 基础信息
漏洞信息
# WordPress 文件上传 <=4.24.11 路径遍历漏洞
## 漏洞概述
WordPress File Upload插件存在路径遍历漏洞,允许未认证的攻击者读取或删除超出预期目录的文件。
## 影响版本
所有版本,包括4.24.11及以下版本。
## 漏洞细节
在`wfu_file_downloader.php`文件中存在路径遍历漏洞,影响版本为4.24.11及以下版本。成功利用该漏洞需要目标WordPress安装使用PHP 7.4或更早版本。
## 影响
允许未认证的攻击者读取或删除超出预期目录的文件。
提示
尽管我们采用了先进的大模型技术,但其输出仍可能包含不准确或过时的信息。
神龙会尽力确保数据准确,但也请结合实际情况进行甄别与判断。
神龙祝您一切顺利!
神龙会尽力确保数据准确,但也请结合实际情况进行甄别与判断。
神龙祝您一切顺利!
漏洞标题
WordPress File Upload <= 4.24.11 - Unauthenticated Path Traversal to Arbitrary File Read and Deletion in wfu_file_downloader.php
来源:美国国家漏洞数据库 NVD
漏洞描述信息
The WordPress File Upload plugin for WordPress is vulnerable to Path Traversal in all versions up to, and including, 4.24.11 via wfu_file_downloader.php. This makes it possible for unauthenticated attackers to read or delete files outside of the originally intended directory. Successful exploitation requires the targeted WordPress installation to be using PHP 7.4 or earlier.
来源:美国国家漏洞数据库 NVD
CVSS信息
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
来源:美国国家漏洞数据库 NVD
漏洞类别
对路径名的限制不恰当(路径遍历)
来源:美国国家漏洞数据库 NVD
漏洞标题
WordPress plugin WordPress File Upload 路径遍历漏洞
来源:中国国家信息安全漏洞库 CNNVD
漏洞描述信息
WordPress和WordPress plugin都是WordPress基金会的产品。WordPress是一套使用PHP语言开发的博客平台。该平台支持在PHP和MySQL的服务器上架设个人博客网站。WordPress plugin是一个应用插件。 WordPress plugin WordPress File Upload 4.24.11版本及之前版本存在路径遍历漏洞。攻击者利用该漏洞可以读取或删除原始目录之外的文件。
来源:中国国家信息安全漏洞库 CNNVD
CVSS信息
N/A
来源:中国国家信息安全漏洞库 CNNVD
漏洞类别
路径遍历
来源:中国国家信息安全漏洞库 CNNVD
二、漏洞 CVE-2024-9047 的公开POC
| # | POC 描述 | 源链接 | 神龙链接 |
|---|---|---|---|
| 1 | WordPress File Upload插件任意文件读取漏洞(CVE-2024-9047)批量检测脚本 | https://github.com/iSee857/CVE-2024-9047-PoC | POC详情 |
| 2 | POC - WordPress File Upload plugin, in the wfu_file_downloader.php file before version <= 4.24.11 | https://github.com/verylazytech/CVE-2024-9047 | POC详情 |
| 3 | Exploit for WordPress File Upload Plugin - All versions up to 4.24.11 are vulnerable. | https://github.com/Nxploited/CVE-2024-9047-Exploit | POC详情 |
| 4 | CVE-2024-9047, wfu_file_downloader.php | https://github.com/chihyeonwon/CVE-2024-9047 | POC详情 |
| 5 | CVE-2024-9047, wfu_file_downloader.php | https://github.com/mr-won/CVE-2024-9047 | POC详情 |
| 6 | The WordPress File Upload plugin for WordPress is vulnerable to Path Traversal in all versions up to, and including, 4.24.11 via wfu_file_downloader.php. This makes it possible for unauthenticated attackers to read or delete files outside of the originally intended directory. Successful exploitation requires the targeted WordPress installation to be using PHP 7.4 or earlier. | https://github.com/projectdiscovery/nuclei-templates/blob/main/http/cves/2024/CVE-2024-9047.yaml | POC详情 |
| 7 | CVE-2024-9047, wfu_file_downloader.php | https://github.com/user20252228/CVE-2024-9047 | POC详情 |
| 8 | CVE-2024-9047, wfu_file_downloader.php | https://github.com/tpdlshdmlrkfmcla/CVE-2024-9047 | POC详情 |
| 9 | CVE-2024-9047 | https://github.com/amirqusairy99/WordPress-File-Upload-4.24.11---Unauthenticated-Path-Traversal | POC详情 |
三、漏洞 CVE-2024-9047 的情报信息
-
标题: WordPress File Upload <= 4.24.11 - Unauthenticated Path Traversal to Arbitrary File Read and Deletion in wfu_file_downloader.php -- 🔗来源链接
标签:
神龙速读 -
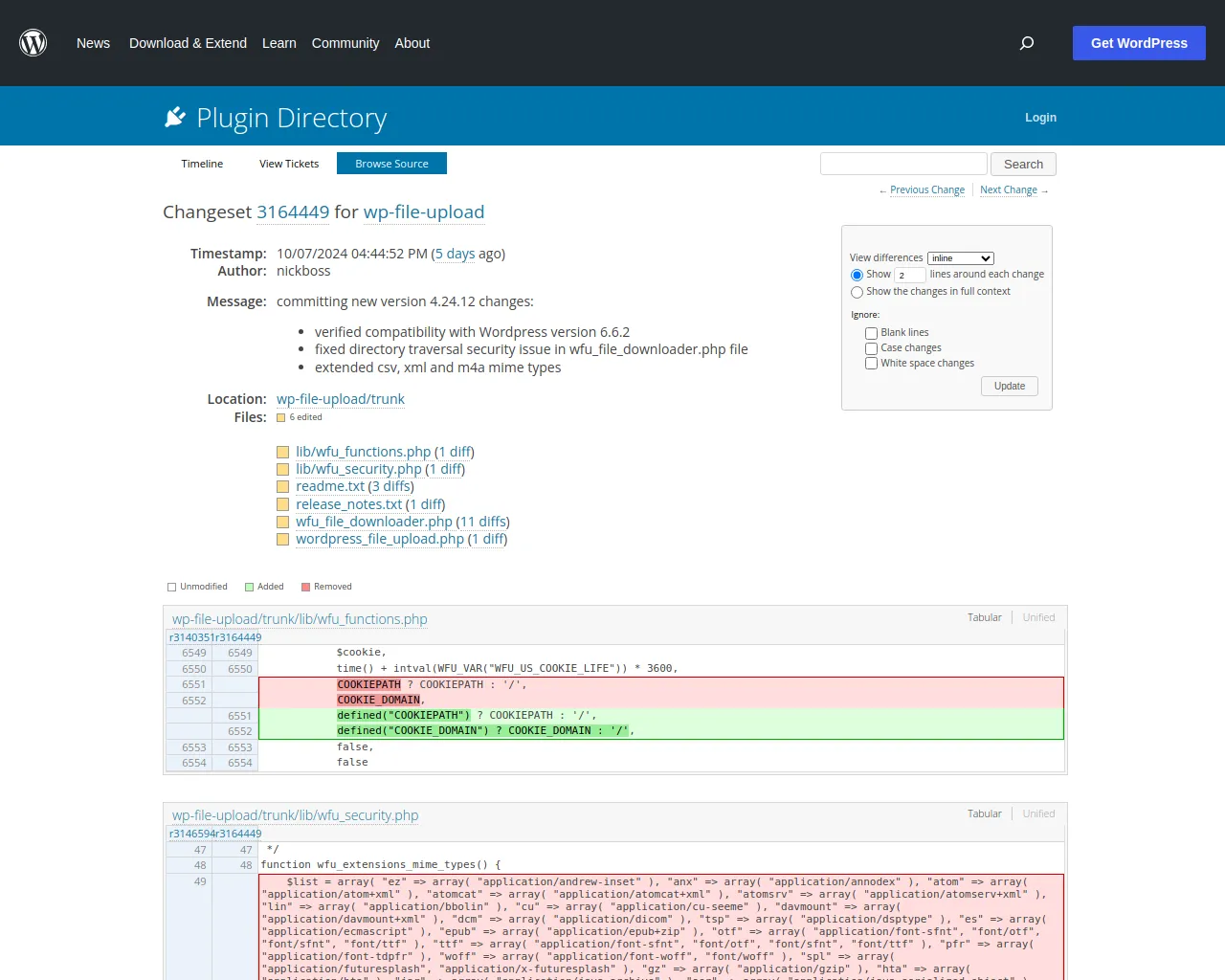
标题: Changeset 3164449 for wp-file-upload – WordPress Plugin Repository -- 🔗来源链接
标签:
- https://nvd.nist.gov/vuln/detail/CVE-2024-9047
四、漏洞 CVE-2024-9047 的评论
暂无评论