一、 漏洞 CVE-2025-1330 基础信息
漏洞信息
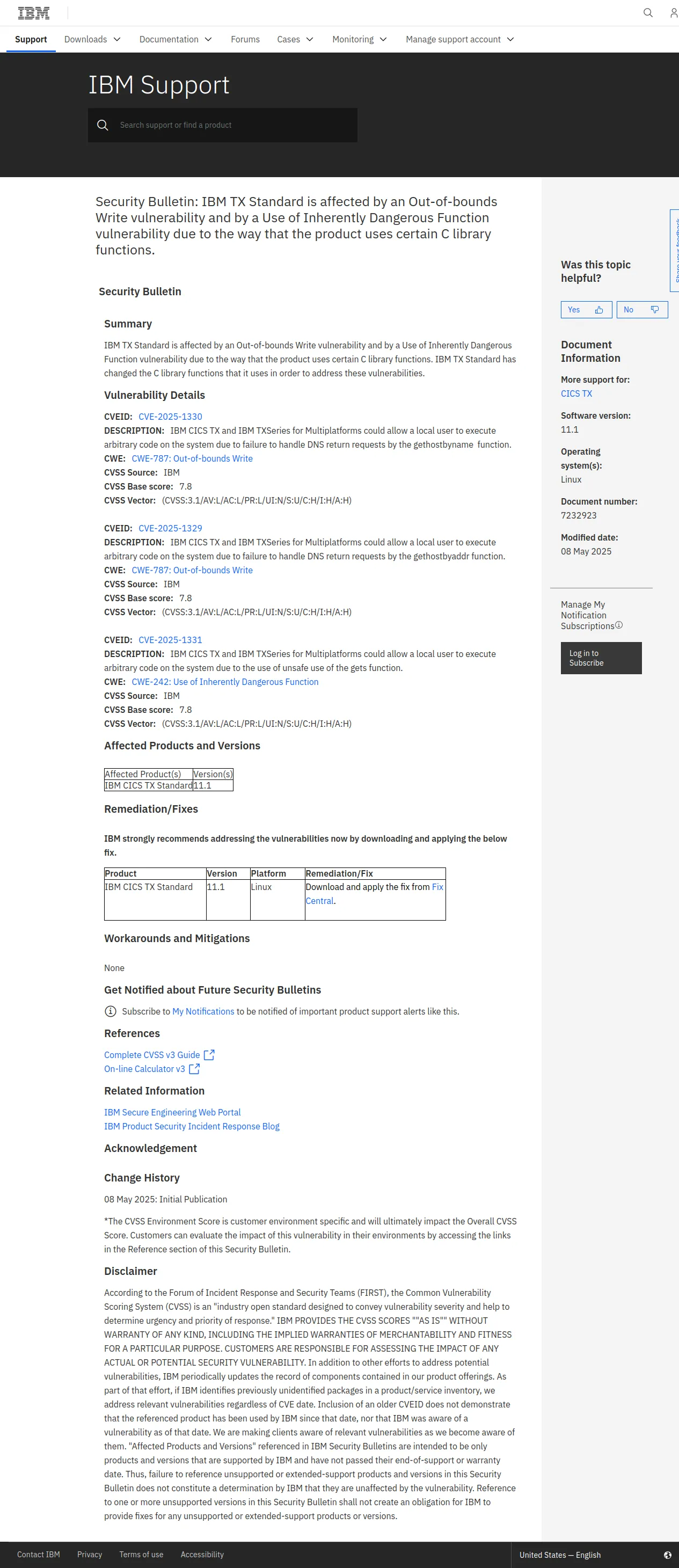
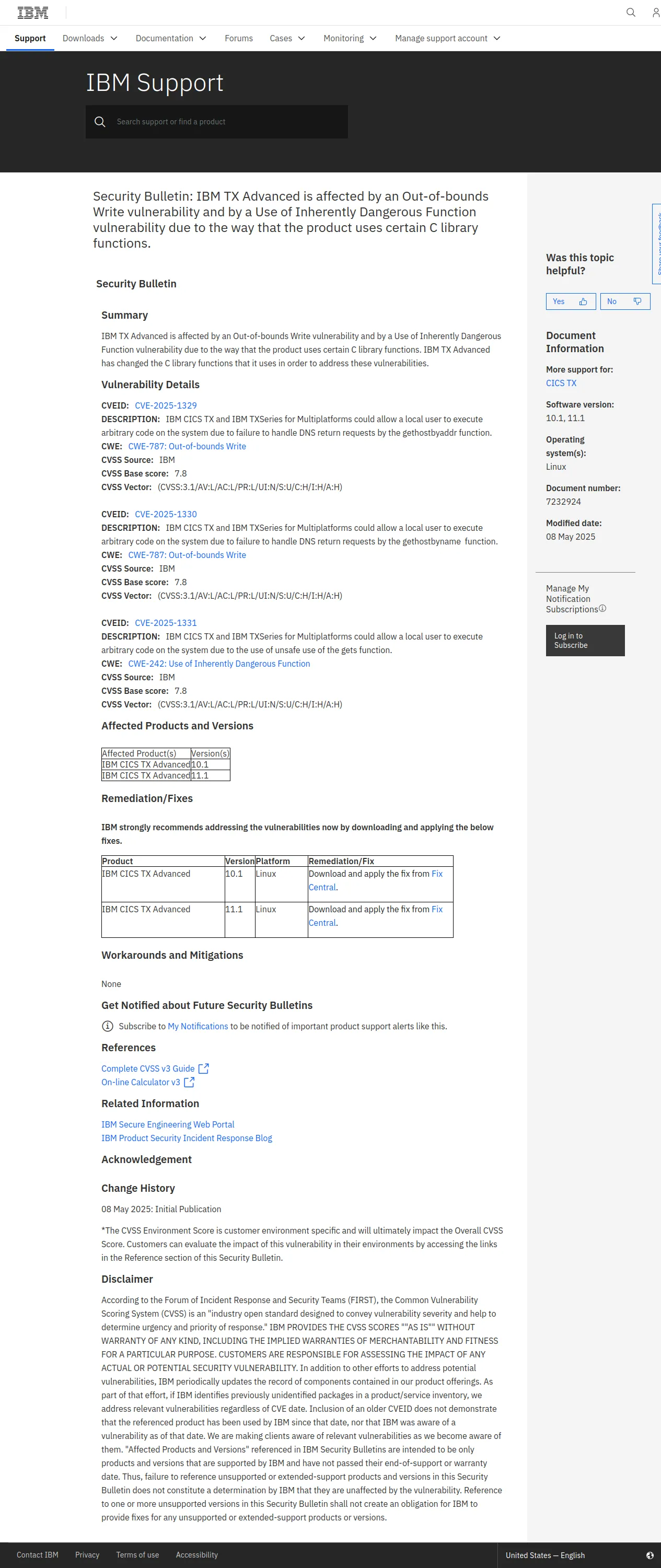
# IBM CICS TX代码执行漏洞
## 漏洞概述
IBM CICS TX Standard 11.1 和 IBM CICS TX Advanced 10.1 和 11.1 中存在一个漏洞,可能导致本地用户通过失败的DNS返回请求处理执行任意代码。
## 影响版本
- IBM CICS TX Standard 11.1
- IBM CICS TX Advanced 10.1
- IBM CICS TX Advanced 11.1
## 漏洞细节
该漏洞源于 `gethostbyname` 函数在处理DNS返回请求时存在不足,导致本地用户可能通过特定的输入执行任意代码。
## 漏洞影响
本地攻击者可以利用此漏洞在系统上执行任意代码,从而可能获得控制权或访问受限资源。
提示
神龙会尽力确保数据准确,但也请结合实际情况进行甄别与判断。
神龙祝您一切顺利!
漏洞标题
漏洞描述信息
CVSS信息
漏洞类别
漏洞标题
漏洞描述信息
CVSS信息
漏洞类别
二、漏洞 CVE-2025-1330 的公开POC
| # | POC 描述 | 源链接 | 神龙链接 |
|---|
三、漏洞 CVE-2025-1330 的情报信息
-
标题: Security Bulletin: IBM TX Standard is affected by an Out-of-bounds Write vulnerability and by a Use of Inherently Dangerous Function vulnerability due to the way that the product uses certain C library functions. -- 🔗来源链接
标签: vendor-advisory
神龙速读 -
标题: Security Bulletin: IBM TX Advanced is affected by an Out-of-bounds Write vulnerability and by a Use of Inherently Dangerous Function vulnerability due to the way that the product uses certain C library functions. -- 🔗来源链接
标签: vendor-advisory
神龙速读 - https://nvd.nist.gov/vuln/detail/CVE-2025-1330