关联漏洞
描述
A tool written in Go that scans files & directories for the Follina exploit (CVE-2022-30190)
介绍
# FollinaScanner
A tool written in Go that scans files & directories for the Follina exploit (CVE-2022-30190)
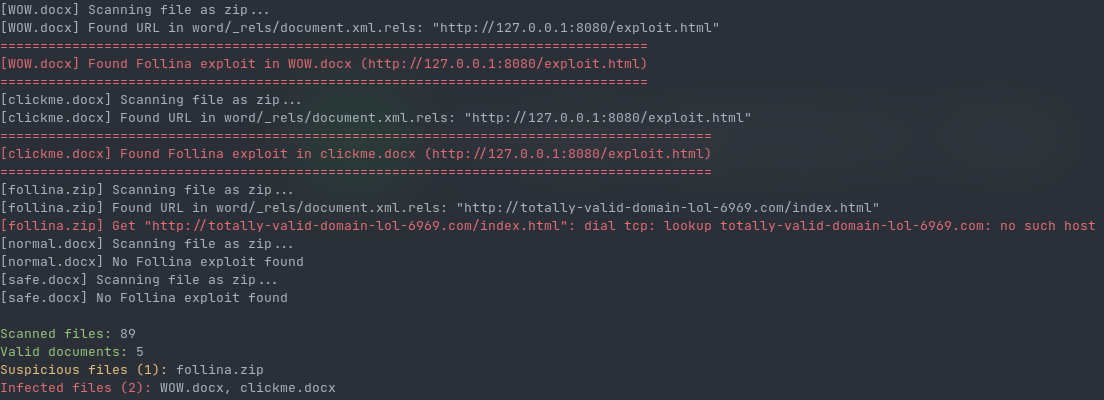
*(Note: "Suspicious files" means files that have a URL in them but isn't working)*
## Compiling
```sh
git clone https://github.com/ErrorNoInternet/FollinaScanner
cd FollinaScanner
go build
```
## Usage
```sh
# Scan the current directory
./follina-scanner -r .
# Scan a specific file
./follina-scanner amogus.docx
```
Use `./follina-scanner --help` for a list of arguments
<sub>If you would like to modify or use this repository (including its code) in your own project, please be sure to credit!</sub>
文件快照
[4.0K] /data/pocs/37e37030090a14ece710710507088fe66412e4ec
├── [ 257] go.mod
├── [1.0K] go.sum
├── [1.0K] LICENSE
├── [4.8K] main.go
├── [ 729] README.md
└── [4.0K] screenshots
└── [ 88K] screenshot0.png
1 directory, 6 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。