关联漏洞
标题:
Apache Struts 输入验证错误漏洞
(CVE-2018-11776)
描述:Apache Struts是美国阿帕奇(Apache)软件基金会负责维护的一个开源项目,是一套用于创建企业级Java Web应用的开源MVC框架,主要提供两个版本框架产品,Struts 1和Struts 2。Apache Struts 2是Apache Struts的下一代产品,是在Struts 1和WebWork的技术基础上进行了合并的全新Struts 2框架,其体系结构与Struts 1差别较大。 Apache Struts 2.3版本至2.3.34版本和2.5版本至2.5.16版本中存在输入验证漏洞
描述
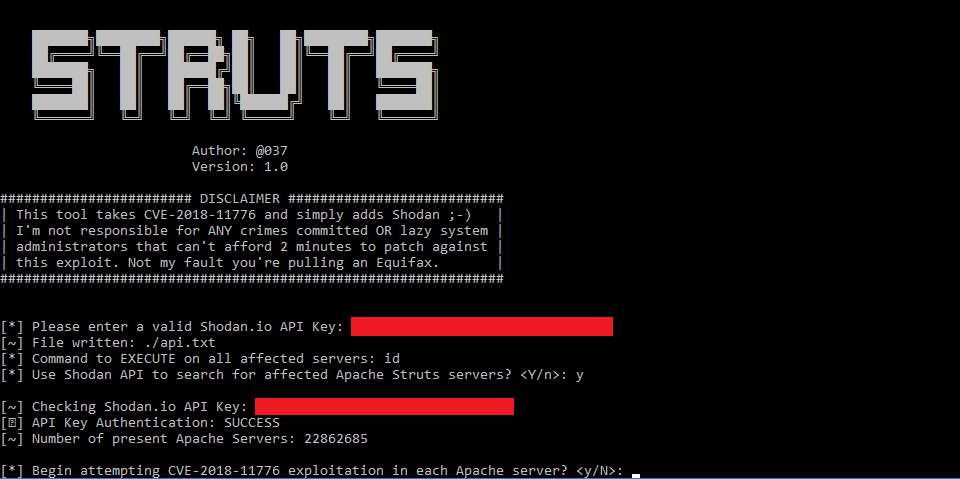
This tool takes advantage of CVE-2018-11776 and Shodan to perform mass exploitation of verified and vulnerable Apache Struts servers.
介绍
# APACHE STRUTS SHODAN EXPLOIT POC
* Author: [@037](https://twitter.com/037)
Original code can be found [here](https://github.com/hook-s3c/CVE-2018-11776-Python-PoC).
This tool takes advantage of CVE-2018-11776 and Shodan to perform mass exploitation of verified and vulnerable Apache Struts servers.
Shodan search parameter has been left out to weed out any skids trying to use this tool for malicious reasons. This tool is created to be treated as a proof of concept for researchers not an attack tool.
It's important to also mention this tool verifies if the host is vulnerable before performing the exploit process. Making simulated attacks stealthy.
### Prerequisites
You're required to install Python 3.x
```
apt-get install python3
```
You are also required to have Shodan module installed
```
pip install shodan
```
### Using Shodan API
This tool requires you to own an upgraded Shodan API
You may obtain one for free in [Shodan](https://shodan.io/) if you sign up using a .edu email.
文件快照
[4.0K] /data/pocs/6cd02273f34305922c4b09e485f88fca77ef6547
├── [ 21K] 1.png
├── [1.1K] README.md
└── [6.0K] Struts.py
0 directories, 3 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。