关联漏洞
标题:微软 Microsoft SMBv3 缓冲区错误漏洞 (CVE-2020-0796)描述:Microsoft SMBv3是美国微软(Microsoft)公司的一个为设备提供SMB功能的支持固件。 Microsoft Server Message Block 3.1.1 (SMBv3)版本中存在缓冲区错误漏洞,该漏洞源于SMBv3协议在处理恶意压缩数据包时,进入了错误流程。远程未经身份验证的攻击者可利用该漏洞在应用程序中执行任意代码。以下产品及版本受到影响:Microsoft Windows 10版本1903,Windows Server版本1903,Windows 10版本1909,Windo
描述
Powershell SMBv3 Compression checker
介绍
> **Warning**
> This repository has been archived and is no longer actively maintained.
# CVE-2020-0796
Powershell SMBv3 Compression checker
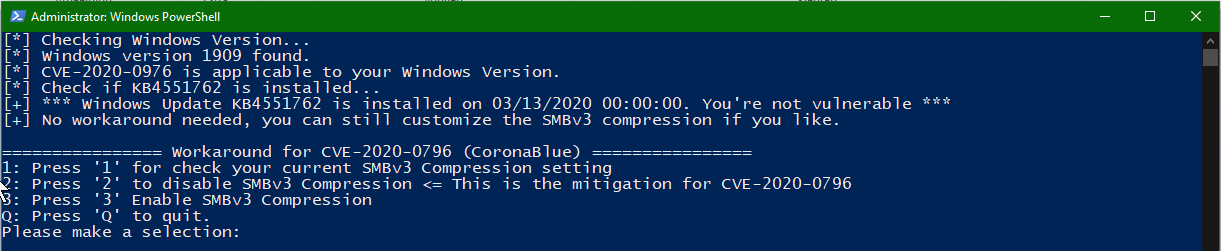
Related blog post: https://binsec.nl/cve-2020-0796-smbv3-rce-vulnerebility-in-smbv3-coronablue/
## This vulnerability has so far only applied to the following operating systems:
Windows 10 Version 1903 for 32-bit Systems
Windows 10 Version 1903 for ARM64-based Systems
Windows 10 Version 1903 for x64-based Systems
Windows 10 Version 1909 for 32-bit Systems
Windows 10 Version 1909 for ARM64-based Systems
Windows 10 Version 1909 for x64-based Systems
Windows Server, version 1903 (Server Core installation)
Windows Server, version 1909 (Server Core installation)
## What is the default setting of Windows?
We have asked Microsoft what is the default setting for SMBv3 compression? Microsoft has answered this question that SMBv3 compression is enabled by default.
## March 12: Microsoft has released patch KB4551762 for fixing CVE-2020-0796
Patch download: https://www.catalog.update.microsoft.com/Search.aspx?q=KB4551762
文件快照
[4.0K] /data/pocs/71fb9fa588dd938b409a4cc9208b9cfb5ca4543b
├── [5.2K] CVE-2020-0796-Smbv3-checker.ps1
├── [4.0K] images
│ └── [ 26K] Image-of-Powershell-SMBv3-Compression-checker.png
└── [1.2K] README.md
1 directory, 3 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。