关联漏洞
描述
WordPress Automatic Plugin <= 3.92.0 - SQL Injection
介绍
<div align="center">
<img src="https://blogs.cappriciosec.com/uploaders/CVE-2024-27956-tool.png" alt="logo">
</div>
## Badges
[](https://choosealicense.com/licenses/mit/)



<a href="https://github.com/Cappricio-Securities/CVE-2024-27956/releases/"><img src="https://img.shields.io/github/release/Cappricio-Securities/CVE-2024-27956"></a>
[](https://twitter.com/cappricio_sec)
<p align="center">
<p align="center">
## License
[MIT](https://choosealicense.com/licenses/mit/)
## Installation
1. Install Python3 and pip [Instructions Here](https://www.python.org/downloads/) (If you can't figure this out, you shouldn't really be using this)
- Install via pip
- ```bash
pip install CVE-2024-27956
```
- Run bellow command to check
- `CVE-2024-27956 -h`
## Configurations
2. We integrated with the Telegram API to receive instant notifications for vulnerability detection.
- Telegram Notification
- ```bash
CVE-2024-27956 --chatid <YourTelegramChatID>
```
- Open your telegram and search for [`@CappricioSecuritiesTools_bot`](https://web.telegram.org/k/#@CappricioSecuritiesTools_bot) and click start
## Usages
3. This tool has multiple use cases.
- To Check Single URL
- ```bash
CVE-2024-27956 -u http://example.com
```
- To Check List of URL
- ```bash
CVE-2024-27956 -i urls.txt
```
- Save output into TXT file
- ```bash
CVE-2024-27956 -i urls.txt -o out.txt
```
- Want to Learn about [`CVE-2024-27956`](https://blogs.cappriciosec.com/blog/191/CVE-2024-27956)? Then Type Below command
- ```bash
CVE-2024-27956 -b
```
<p align="center">
<b>🚨 Disclaimer</b>
</p>
<p align="center">
<b>This tool is created for security bug identification and assistance; Cappricio Securities is not liable for any illegal use.
Use responsibly within legal and ethical boundaries. 🔐🛡️</b></p>
## Working PoC Video
[]( https://asciinema.org/a/sZ4JYdZjiFcpchLAbuMPVfUv7)
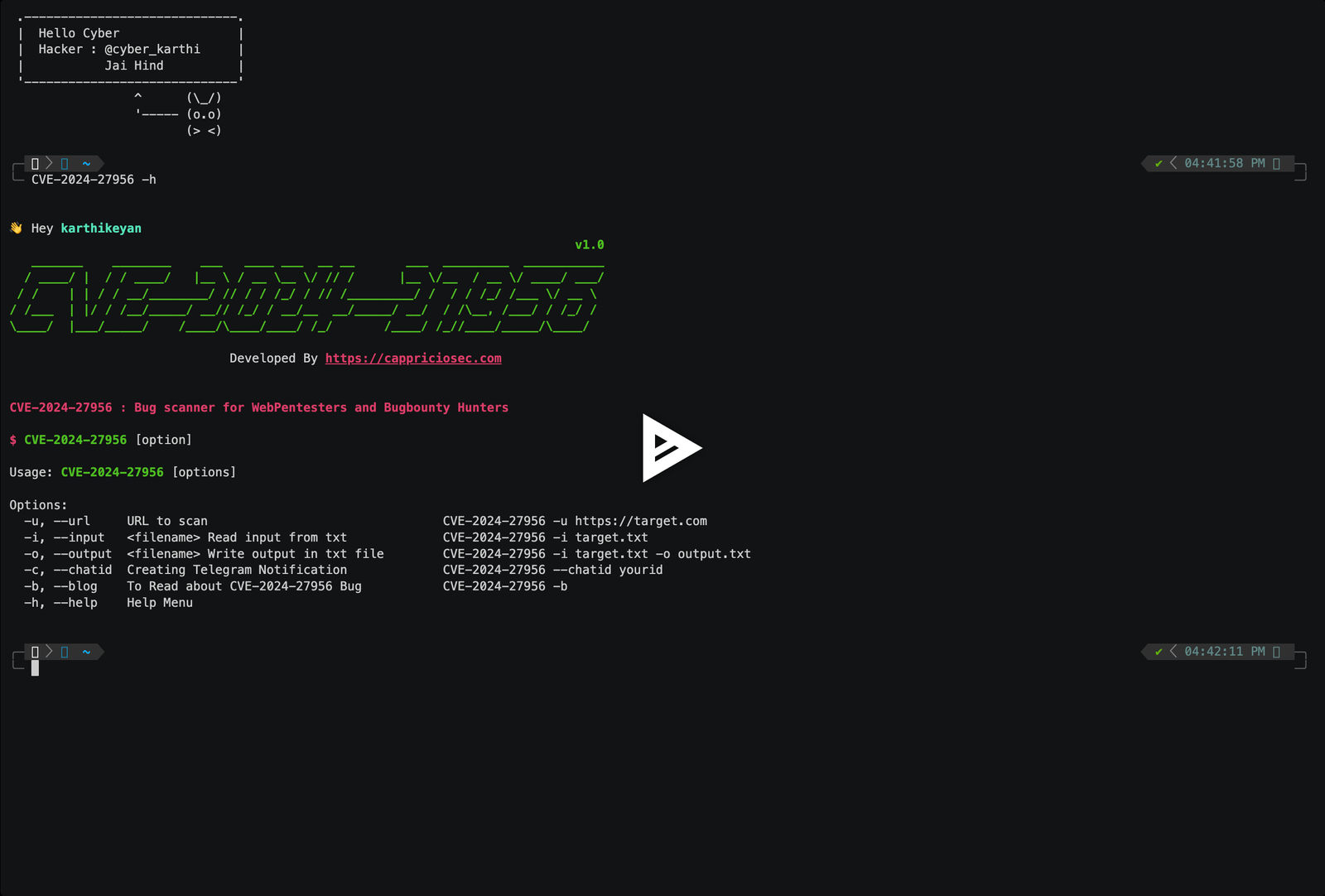
## Help menu
#### Get all items
```bash
👋 Hey Hacker
v1.0
_______ ________ ___ ____ ___ __ __ ___ _________ ___________
/ ____/ | / / ____/ |__ \ / __ \__ \/ // / |__ \/__ / __ \/ ____/ ___/
/ / | | / / __/________/ // / / /_/ / // /_________/ / / / /_/ /___ \/ __ \
/ /___ | |/ / /__/_____/ __// /_/ / __/__ __/_____/ __/ / /\__, /___/ / /_/ /
\____/ |___/_____/ /____/\____/____/ /_/ /____/ /_//____/_____/\____/
Developed By https://cappriciosec.com
CVE-2024-27956 : Bug scanner for WebPentesters and Bugbounty Hunters
$ CVE-2024-27956 [option]
Usage: CVE-2024-27956 [options]
```
| Argument | Type | Description | Examples |
| :-------- | :------- | :------------------------- | :------------------------- |
| `-u` | `--url` | URL to scan | CVE-2024-27956 -u https://target.com |
| `-i` | `--input` | filename Read input from txt | CVE-2024-27956 -i target.txt |
| `-o` | `--output` | filename Write output in txt file | CVE-2024-27956 -i target.txt -o output.txt |
| `-c` | `--chatid` | Creating Telegram Notification | CVE-2024-27956 --chatid yourid |
| `-b` | `--blog` | To Read about CVE-2024-27956 Bug | CVE-2024-27956 -b |
| `-h` | `--help` | Help Menu | CVE-2024-27956 -h |
## 🔗 Links
[](https://cappriciosec.com/)
[](https://www.linkedin.com/in/karthikeyan--v/)
[](https://twitter.com/karthithehacker)
## Author
- [@karthithehacker](https://github.com/karthi-the-hacker/)
## Feedback
If you have any feedback, please reach out to us at contact@karthithehacker.com
文件快照
[4.0K] /data/pocs/978803ca43c7925b33d6f39c7bb413943eddb45d
├── [4.0K] cve202427956
│ ├── [4.0K] includes
│ │ ├── [ 654] bot.py
│ │ ├── [ 470] filereader.py
│ │ ├── [ 0] __init__.py
│ │ ├── [2.2K] scan.py
│ │ └── [ 285] writefile.py
│ ├── [1.7K] main.py
│ └── [4.0K] utils
│ ├── [1.9K] configure.py
│ ├── [ 953] const.py
│ ├── [2.3K] helpers.py
│ ├── [ 0] __init__.py
│ └── [ 227] status.py
├── [1.0K] LICENSE
├── [4.6K] README.md
└── [1.0K] setup.py
3 directories, 14 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。