关联漏洞
描述
Scanner of vulnerability on crushftp instance
介绍
# CVE-2024-4040 - Exploit Scanners
## Introduction
This repository hosts a set of scripts related to CVE-2024-4040, a vulnerability affecting CrushFTP VFS (Virtual File System), which allows unauthorized access to files outside the server's intended directory structure.
thanks to the original writer of the original code : [https://github.com/simsor](https://github.com/simsor)
## About the Scripts
[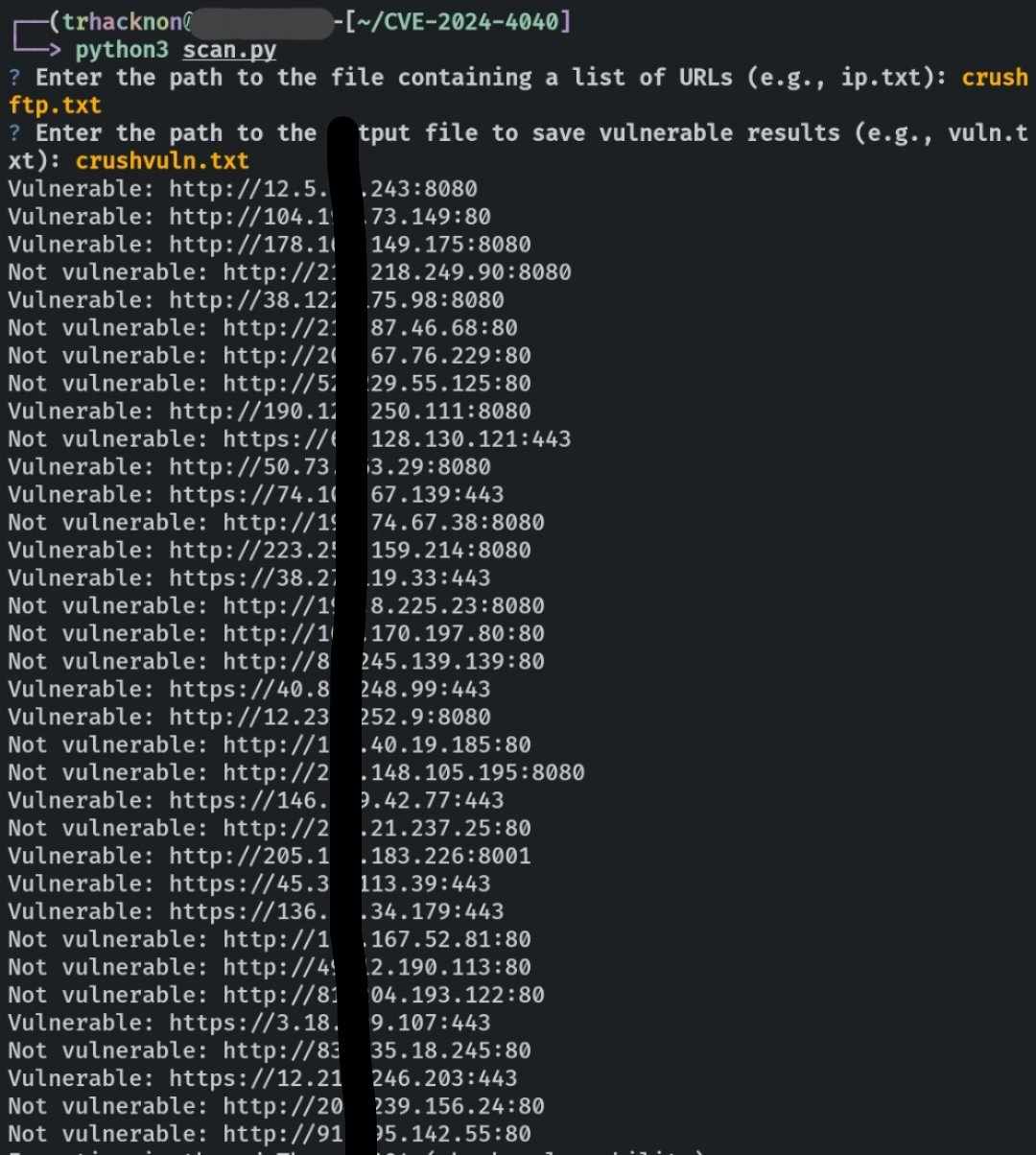](https://github.com/tucommenceapousser/CVE-2024-4040-Scanner)
### main.py
**Modified by Trhacknon**
This script, a modification by Trhacknon, enhances the functionality of the original exploit scanner. The following enhancements have been made:
- **Mass Scan:** It now supports scanning multiple targets simultaneously, allowing for a broader assessment of potential vulnerabilities.
- **Multithreading:** Utilizing multiple threads, the scanner boosts efficiency by concurrently scanning multiple targets.
- **Output:** Upon completion of a scan, the script prints "Vulnerable" to standard output if it successfully exploits the vulnerability, accompanied by an exit code of 1. Conversely, if the vulnerability exploitation fails, it prints "Not vulnerable" and exits with a status code of 0.
**Usage:**
```bash
python main.py
```
**Dependencies:** The script relies on the `requests` library.
### scan_logs.py
This script is designed to search for signs of compromise within a CrushFTP server installation directory. Essentially, it performs the equivalent of the following command:
```bash
$ grep -F -r '<INCLUDE>' /path/to/CrushFTP/logs/
```
For each match found, it attempts to extract the IP address from which the exploit originated.
## Clone on replit
[](https://repl.it/github/tucommenceapousser/CVE-2024-4040-Scanner)
## Usage
```
pip install requests questionary termcolor colorama
```
### main.py
1. Clone the repository:
```bash
git clone https://github.com/tucommenceapousser/CVE-2024-4040-Scanner
```
2. Navigate to the directory containing `main.py`.
3. Execute the script:
```bash
python main.py
```
### scan_logs.py
1. Clone the repository:
```bash
git clone https://github.com/tucommenceapousser/CVE-2024-4040-Scanner
```
2. Navigate to the directory containing `scan_logs.py`.
3. Execute the script:
```bash
python scan_logs.py
```
## Dependencies
- **Python 3:** The scripts are written in Python 3.
- **Requests Library:** Used for making HTTP requests, required by `main.py`.
## Contributing
Contributions are welcome! Feel free to submit pull requests or open issues if you encounter any problems or have suggestions for improvements.
## License
This project is licensed under the [MIT License](LICENSE).
文件快照
[4.0K] /data/pocs/be0c19c6d00c8a95850c9f73b5292bf16a0dcd4e
├── [301K] main.py
├── [2.9K] README.md
├── [115K] received_415572074523990.jpeg
└── [1.3K] scan_logs.py
0 directories, 4 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。