关联漏洞
标题:OpenSSH 安全漏洞 (CVE-2024-6387)描述:OpenSSH(OpenBSD Secure Shell)是加拿大OpenBSD计划组的一套用于安全访问远程计算机的连接工具。该工具是SSH协议的开源实现,支持对所有的传输进行加密,可有效阻止窃听、连接劫持以及其他网络级的攻击。 OpenSSH 存在安全漏洞,该漏洞源于信号处理程序中存在竞争条件,攻击者利用该漏洞可以在无需认证的情况下远程执行任意代码并获得系统控制权。
描述
Quickly identifies servers vulnerable to OpenSSH 'regreSSHion' (CVE-2024-6387).
介绍
# regreSSHion-checker
## 📜 Description
regreSSHion-checker is a lightweight, efficient tool designed to identify servers running vulnerable versions of OpenSSH, specifically targeting the recently discovered `regreSSHion` vulnerability (CVE-2024-6387). This tool facilitates rapid scanning of multiple IP addresses, domain names, and CIDR network ranges to detect potential vulnerabilities and ensure the security of your infrastructure.
## 🌟 Features
- **Rapid Scanning**: Quickly scan multiple IP addresses, domain names, and CIDR ranges for the CVE-2024-6387 vulnerability.
- **Banner Retrieval**: Efficiently retrieves SSH banners without authentication.
- **Concurrency**: Utilizes Go's concurrency model (goroutines) for parallel execution, significantly reducing scan times.
- **Clear Output**: Provides clear, emoji-coded output summarizing scan results.
- **Port Check**: Identifies closed ports and provides a summary of non-responsive hosts.
## 🛠️ Installing or Building
To install regreSSHion-checker from the GitHub repository, ensure you have Go installed and configured properly. Use the following command:
```bash
go get github.com/xonoxitron/regreSSHion-checker
```
After installation, you can use regreSSHion-checker as described in the usage section below.
To build `regreSSHion-checker` from source, ensure you have Go installed and follow these steps:
1. Clone the repository or download the source code.
```bash
git clone https://github.com/your/repo.git
cd regreSSHion-checker
```
2. Build the binary using `go build`.
```bash
go build regreSSHion-checker.go
```
3. Optionally, you can set execute permissions.
```bash
chmod +x regreSSHion-checker
```
Now you can use `./regreSSHion-checker` to scan for CVE-2024-6387 vulnerabilities in OpenSSH across your infrastructure.
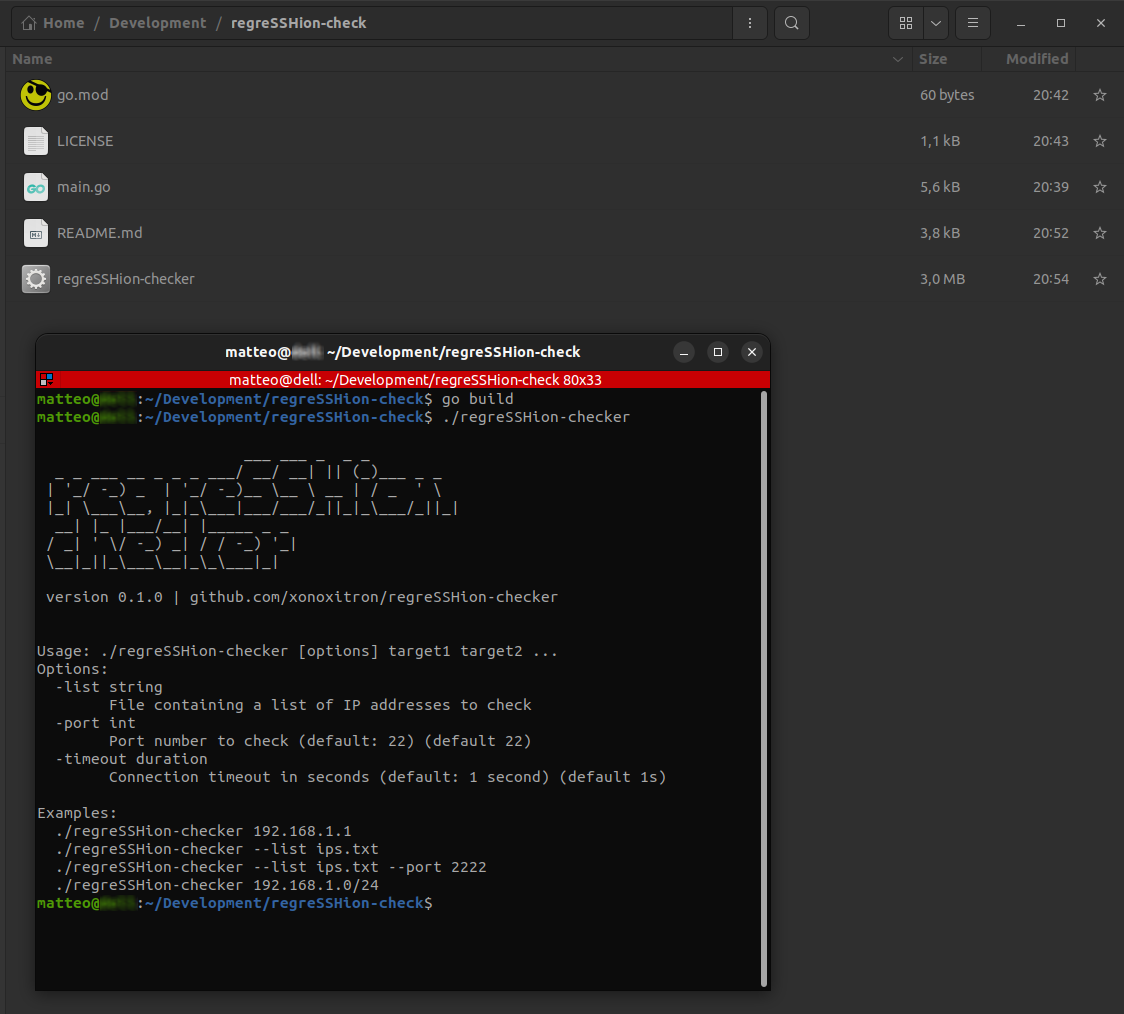
## 🚀 Usage
```bash
./regreSSHion-checker <targets> [--port PORT]
```
### Examples
#### Single IP
```bash
./regreSSHion-checker 192.168.1.1
```
#### IPs from a list
```bash
./regreSSHion-checker -list ip_list.txt
```
#### Multiple IPs and Domains
```bash
./regreSSHion-checker 192.168.1.1 example.com 192.168.1.2
```
#### CIDR Range
```bash
./regreSSHion-checker 192.168.1.0/24
```
#### With Custom Port
```bash
./regreSSHion-checker 192.168.1.1 example.com --port 2222
```
### Output
The tool provides a summary of the scanned targets:
- 🛡️ Not Vulnerable: Servers running a non-vulnerable version of OpenSSH.
- 🚨 Vulnerable: Servers running a vulnerable version of OpenSSH.
- 🔒 Closed Ports: Count of servers with port 22 (or specified port) closed.
- 📊 Total Scanned: Total number of targets scanned.
```text
🛡️ Servers not vulnerable: 1
[+] Server at 157.90.125.31 (running SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.11)
🚨 Servers likely vulnerable: 2
[+] Server at 4.231.170.121 (running SSH-2.0-OpenSSH_8.9p1 Ubuntu-3ubuntu0.10)
[+] Server at 4.231.170.122 (running SSH-2.0-OpenSSH_9.2p1 Debian-2+deb12u2)
🔒 Servers with port 22 closed: 254
📊 Total scanned targets: 257
```
## 📚 References
- [Qualys Blog on regreSSHion Vulnerability](https://blog.qualys.com/vulnerabilities-threat-research/2024/07/01/regresshion-remote-unauthenticated-code-execution-vulnerability-in-openssh-server)
---
### Notes:
- Ensure you have Go installed to compile and run the tool (`go build regreSSHion-checker.go`).
- Replace `regreSSHion-checker` with the name of the Go binary compiled from your source file.
- Adjust permissions if needed (`chmod +x regreSSHion-checker`) to execute the binary directly.
This README.md file now reflects the usage and features of the Go version of the regreSSHion-checker tool, providing users with clear instructions and examples for effective vulnerability scanning of OpenSSH servers.
文件快照
[4.0K] /data/pocs/ceb5a3c0868400270a69f1271f18924c84fa8746
├── [123K] banner.png
├── [ 60] go.mod
├── [1.0K] LICENSE
├── [5.5K] main.go
└── [3.8K] README.md
0 directories, 5 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。