关联漏洞
标题:
ZK 安全漏洞
(CVE-2022-36537)
描述:ZK是ZK公司的一个高产的开源Java框架,用于构建惊人的企业网和移动应用程序。 ZK Framework v9.6.1版本、9.6.0.1版本、9.5.1.3版本、9.0.1.2版本、8.6.4.1版本存在安全漏洞。攻击者利用该漏洞通过发送 AuUploader 组件的特制 POST 请求访问敏感信息。
描述
CVE-2022-36537
介绍
# CVE-2022-36537
# Summary
R1Soft Server Backup Manager uses the ZK framework as the main framework. Its security requires all Web3 project parties to pay more attention to the security vulnerabilities of various Web3 infrastructures and patch them in time to avoid potential security risks and digital asset losses. We will dig out in time, track various security risks on web3, and provide leading security solutions to ensure that the web3 world chain and off-chain are safe and sound.
# Preface
ZK is the leading open-source Java Web framework for building enterprise Web applications. With over 2,000,000 downloads, ZK empowers a wide variety of companies and institutions, ranging from small to Fortune Global 500 in multiple industries.
R1Soft Server Backup Manager (SBM) offers service providers a flexible, server-friendly solution that takes the hassle out of running traditional backups. Users can run backups every 15 minutes without impacting server performance. Nearly 1,800 service providers use it to protect 250,000 servers.
# Affected Versions
ZK Framework `v9.6.1, 9.6.0.1, 9.5.1.3, 9.0.1.2 and 8.6.4.1.`
ConnectWise Recover `v2.9.7` and earlier versions are impacted.
R1Soft Server Backup Manager `v6.16.3` and earlier versions are impacted.
# ZK Framework Auth Bypass

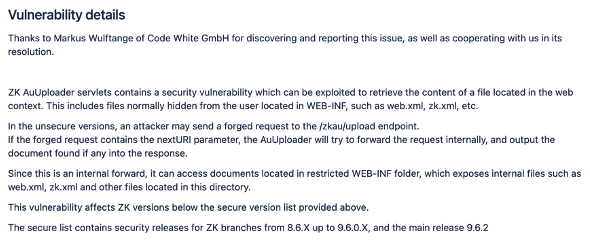
From the vulnerability description, if the route /zkau/upload contains the nextURI parameter, the ZK AuUploader servlet will forward the forward request, which can bypass the identity authentication and return the files in the web context, such as obtaining web.xml, zk page, applicationContext -security.xml configuration information, etc.
# Install
`You need python3, pip3, git.`
```
git clone https://github.com/agnihackers/CVE-2022-36537-EXPLOIT.git
cd CVE-2022-36537-EXPLOIT
pip3 install -r requirements.txt
chmod +x mysql-connector-java-5.1.48.jar
python3 CVE-2022-36537.py
```
# Shodan Dork
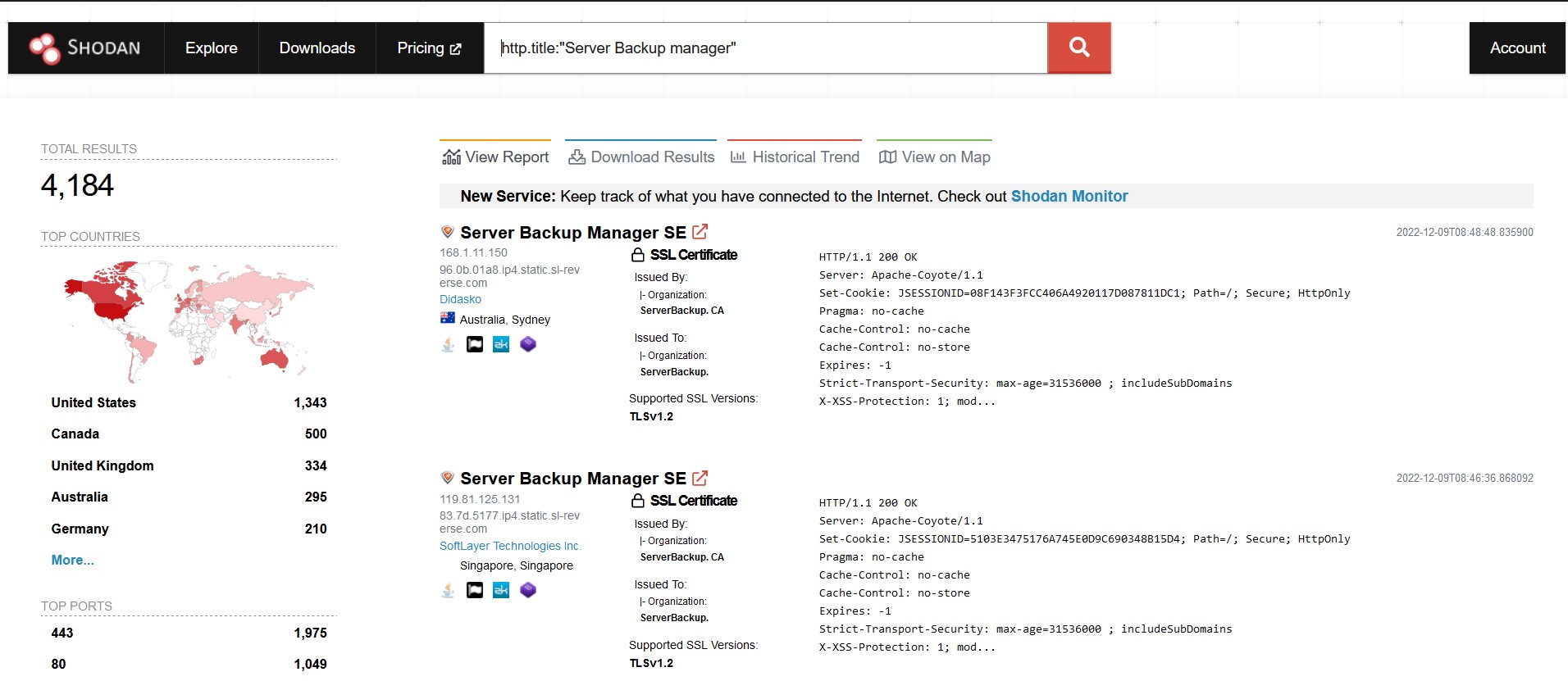
# CVE-2022–36537 Vulnerability More Details
https://twitter.com/AGNIHACKERS1/status/1601162549084696579?s=20&t=ncMMG7XNNZDns4Wn5CfPoA
文件快照
[4.0K] /data/pocs/e526ada34b5414dffb0f965f6d9ccc4204ce6cfb
├── [ 16M] chromedriver
├── [7.9K] CVE-2022-36537.py
├── [1.4K] Driver.java
├── [983K] mysql-connector-java-5.1.48.jar
├── [2.3K] README.md
├── [ 88] requirements.txt
├── [215K] Shodan Dork.jpg
├── [ 25K] unnamed.png
└── [ 79K] ZK-5150.png
0 directories, 9 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。