关联漏洞
描述
This script complements the results obtained through the keepass-password-dumper tool when exploiting the CVE-2023-32784 vulnerability affecting KeePass.
介绍
# BruteForce-to-KeePass
This script complements the results obtained through the ***keepass-password-dumper*** tool when exploiting the CVE-2023-32784 vulnerability affecting KeePass.
# Description
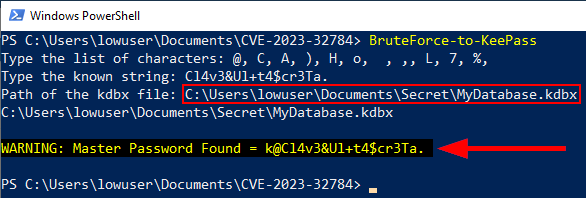
This script prompts the user to input a list of characters and a known suffix. It then generates a list of possible strings (dictionary) by combining each character in the list with the known suffix. The results are saved to a file named "Dictionary.txt" in the current directory.
It then uses the base functionality of the "***PoshKPBrute***" tool (the code has been shortened and adapted) to identify the valid Master Key to access the KeePass database (kdbx file).
# Demo
# Acknowledgements
- The ***keepass-password-dumper*** tool was developed and released by **vdohney** (https://github.com/vdohney/keepass-password-dumper)
- The ***PoshKPBrute*** tool was developed and released by **Wayne Evans** (https://github.com/wevans311082/PoshKPBrute)
Please be sure to give full credit to them.
# References
- https://infayer.com/archivos/1785 (*spanish*)
文件快照
[4.0K] /data/pocs/fe08ebaff961930c184de5a7da9de8889f9ca8de
├── [4.1K] BruteForce-to-KeePass.ps1
└── [1.1K] README.md
0 directories, 2 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。